SDN segmented routing defense method for link flooding attacks
A link flood attack and link technology, which is applied in the field of SDN segment routing defense against link flood attacks, and can solve problems such as lack of defense mechanisms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but the following embodiments in no way limit the present invention.
[0043] The SDN segment routing defense method of the link flood attack provided by the present invention comprises the following steps carried out in order:
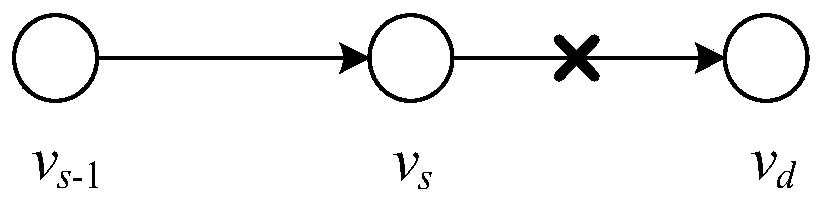
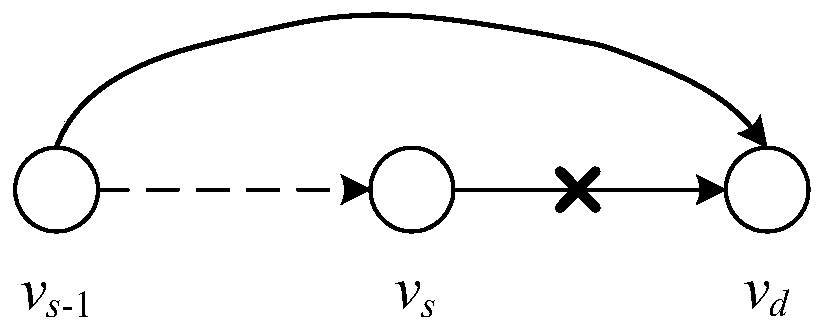
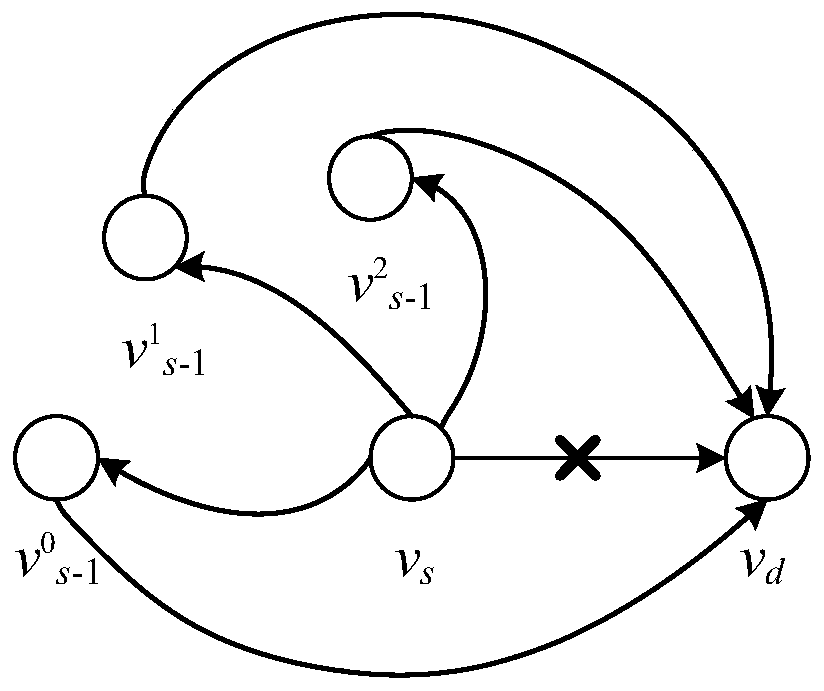
[0044] 1) For a given network topology, construct it as a network model based on a directed graph, and obtain the physical traffic set, capacity and traffic load of the link;
[0045] 2) Use the SDN-based system defense model to monitor the network model constructed in step 1), and judge whether the network model is attacked by LFA and the link is seriously congested. If the judgment result is "Yes", use the SDN controller and Physical traffic set, capacity, and traffic load of the above links segment-routing the network topology; otherwise continue monitoring.
[0046] In step 1), the described construction is based on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com