Shielding method, server and computer readable storage medium
A technology of server and shielding instructions, applied in the field of communication, can solve the problem of unable to shield video CRBT, and achieve the effect of reducing interaction cost and quickly shielding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
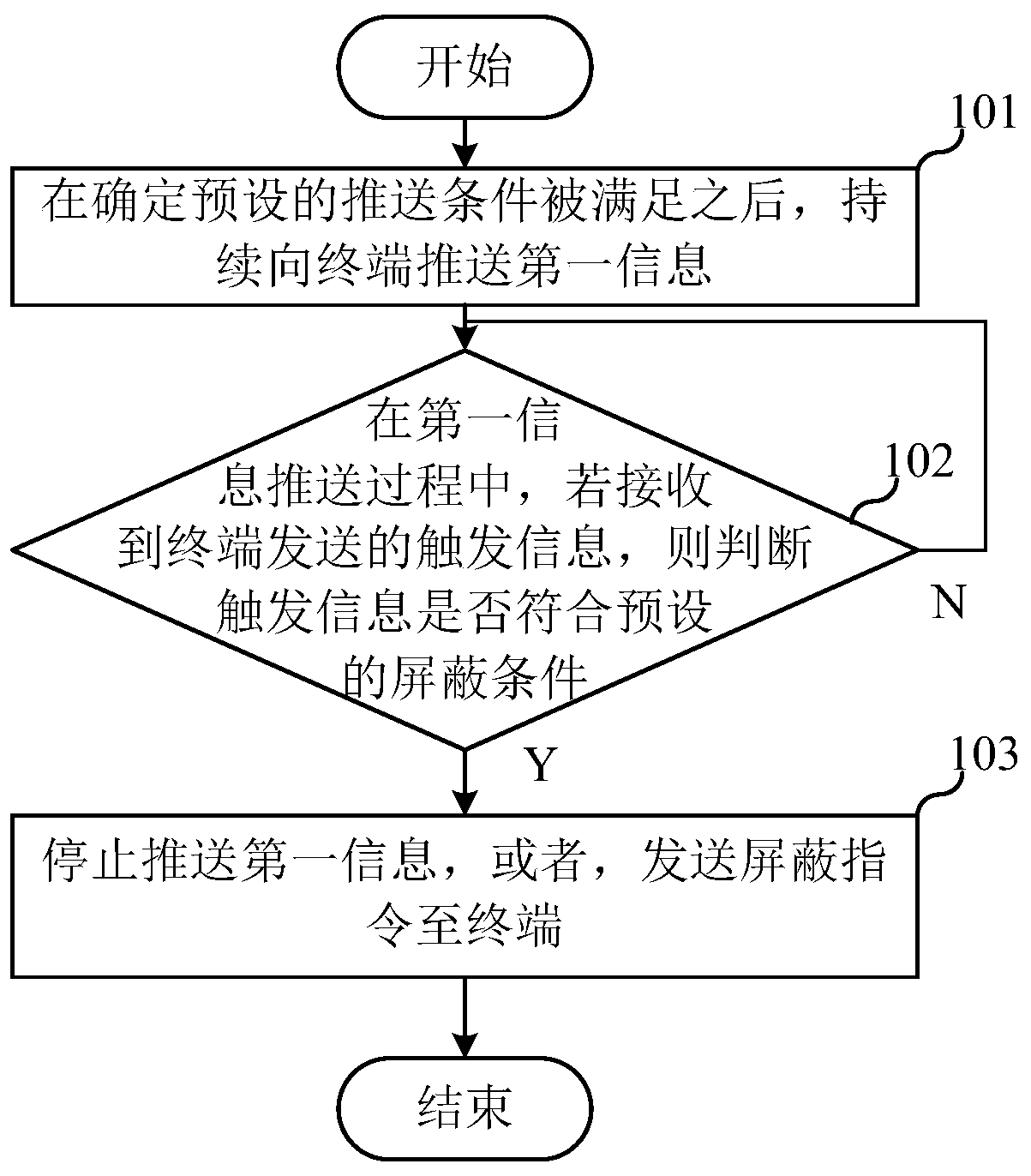
[0033] Example 1: The sensor of the terminal includes a gyroscope, and the shielding condition is that the shaking frequency of the terminal is greater than a preset second threshold, and / or the shaking amplitude of the terminal is greater than a preset third threshold. Specifically, when the user is not interested in the currently pushed first information, the mobile phone can be shaken quickly. The gyroscope of the terminal detects the shaking frequency and / or shaking amplitude, and sends the shaking frequency and / or shaking amplitude as trigger information to the server. The server compares the shaking frequency with the second threshold, and / or compares the shaking amplitude with the third threshold. If the shaking frequency is greater than the preset second threshold, and / or the shaking amplitude of the terminal is greater than the preset third threshold, it means that the trigger information meets the shielding condition. Wherein, the second threshold and the third thre...
example 2
[0034] Example 2: The sensor of the terminal includes a pressure sensor, and the shielding condition is that the number of key presses is greater than a fourth threshold, and / or, the frequency of key presses is greater than a preset fifth threshold. Taking the pressure sensor corresponding to the volume key as an example, when the user is not interested in the first information currently being pushed, he can quickly press the volume key. The terminal determines the number of key presses and / or the frequency of key presses according to the detection data of the sensor corresponding to the volume key, and sends the number of key presses and / or the frequency of key presses as trigger information to the server. The server compares the number of keystrokes with the fourth threshold, and / or compares the frequency of keystrokes with the fifth threshold. If the number of key presses is greater than the fourth threshold, and / or, the frequency of key presses is greater than the fifth th...
example 3
[0035] Example 3: The sensor of the terminal includes a touch sensor, and the shielding condition is that the operation gesture detected by the terminal is a preset gesture. Specifically, when the user is not interested in the currently pushed first information, a preset gesture can be drawn on the touch screen of the terminal. Wherein, the preset gesture may be a gesture entered by the user in advance and saved in the server, or may be a gesture specified by a developer. The terminal determines the gesture drawn by the user according to the data detected by the touch sensor, and sends information indicating the gesture drawn by the user as trigger information to the server. The server judges whether the gesture drawn by the user is a preset gesture according to the information indicating the gesture drawn by the user, and if so, it indicates that the trigger information meets the shielding condition.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com