Resource access control method and device
A technology for access control and resource access, which is applied in the field of communication and can solve problems such as no implementation plan given
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
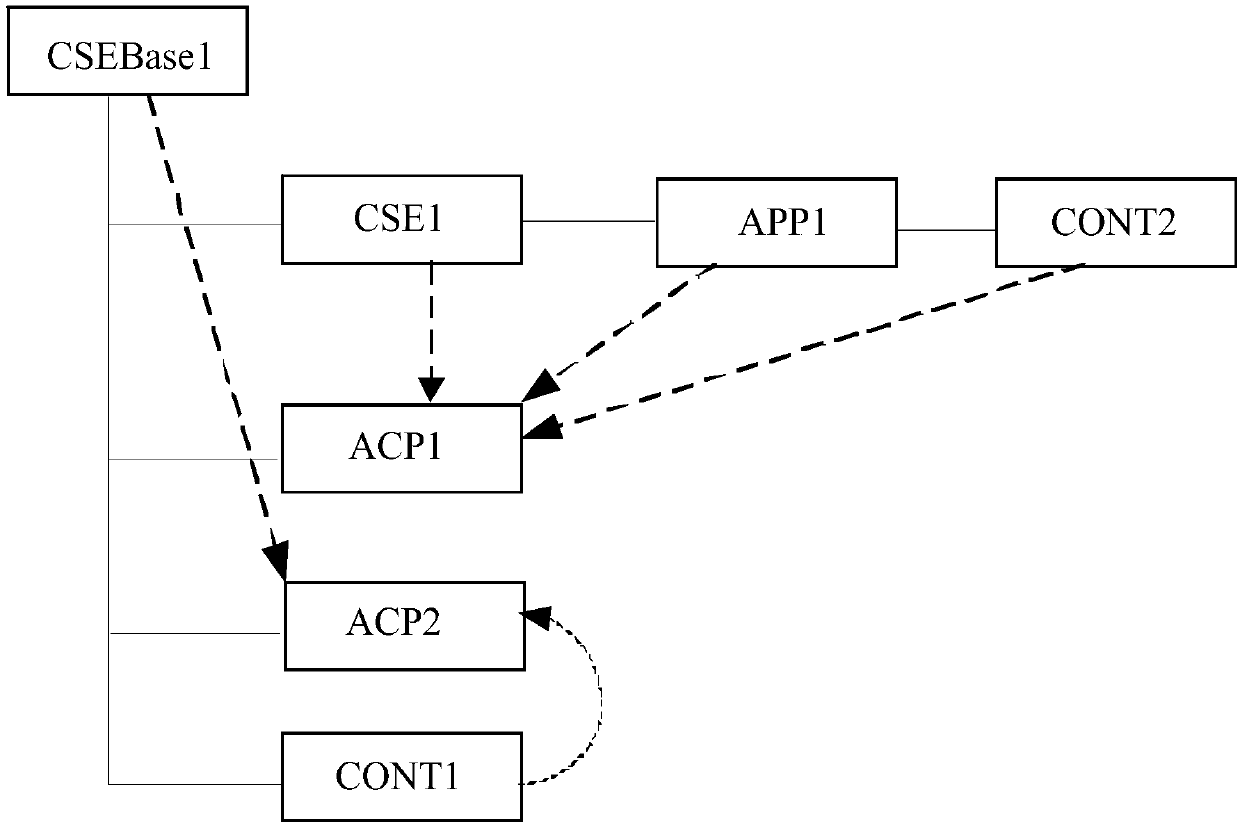
[0104] The access control rule description: the initiator (AE2, AE3, AE4, AE5) can \ Created under resources resource. The rule primitives in this access control rule include:
[0105] Rule effect="permit"
[0106] Rule primitive merge rule: "and"
[0107] Rule primitive 1: request.get("to")=="CSEBase\AE1" / /
[0108] Rule primitive 2: request.get("from") in "AE2, AE3, AE4, AE5"
[0109] Rule primitive 3: request.get("operation")=={"create","retrieve","update"}
[0110] Rule primitive 4: request.get("resource type")=="container"
[0111] Rule primitive 5: request.get("content")in{"maxNrOfInstances", "maxByteSize", "maxInstanceAge"}
[0112] illustrate:
[0113] The rule primitive Rule primitive 1 describes the target resource as CSEBase\AE1. This rule primitive can also be placed in a target resource rule.
[0114] Rule primitive 2 describes the initiator (AE2, AE3, AE4, AE5) as the initiator of the applicable resource access request. This rule...
example 2
[0119] The access control rule description: the initiator (CSE2, CSE3, CSE4) can obtain \ The property value of the resource property (resourceType) of the resource.
[0120] Rule effect="permit"
[0121] Rule primitive merge rule: "and"
[0122] Rule primitive 1: request.get("to")=="CSEBase\AE1"
[0123] Rule primitive 2: request.get("from") in "CSE2, CSE3, CSE4"
[0124] Rule primitive 3: request.get("operation")==”retrieve”
[0125] Rule primitive 4: request. get("content") in {"resourceType"}
[0126] illustrate:
[0127] The rule primitive Rule primitive 1 describes the target resource as CSEBase\AE1. This rule primitive can also be placed in a target resource rule.
[0128] Rule primitive 2 describes the initiator (CSE2, CSE3, CSE4) as the initiator of the applicable resource access request. This rule primitive can also be placed in an initiator rule.
[0129] Rule primitive Rule primitive 3 describes the allowed resource operations as: re...
example 3
[0132] The access control rule describes: role-based access control (Role-Based Access Control, RBAC). The role "Admin" is available in Created under resources resource.
[0133] Rule effect="permit"
[0134] Rule primitive merge rule: "and"
[0135] Rule effect="Permit"
[0136] Rule primitive 1: request.getParents("to")=="CSEBase"
[0137] Rule primitive 2: request. get("from") in "AE1, AE2, AE3"
[0138] Rule primitive 3: request. get("role ids") in "admin"
[0139] Rule primitive 4: request.get("operation") == "create"
[0140] Rule primitive 5: request.get("resource type")=="AE"
[0141] illustrate:
[0142] Rule primitive 1 describes that the target resource is a sub-resource under CSEBase. This rule primitive can also be placed in a target resource rule.
[0143] Rule primitive 2 describes the initiator (AE1, AE2, AE3) as the initiator of the applicable resource access request. This rule primitive can also be placed in an initiator ru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com