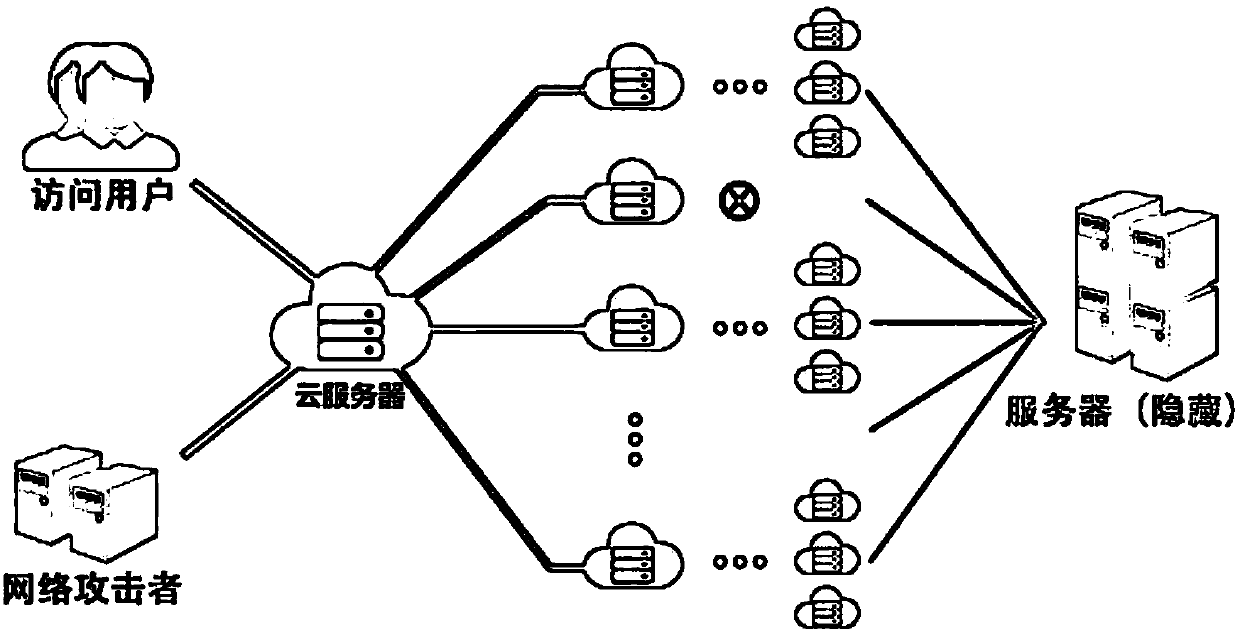
DDOS mass flow defense architecture
A large flow, protection platform technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of expensive, unsuitable for small and medium-sized enterprises, poor versatility, etc., to achieve the effect of ensuring the security of the source station and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0022] A kind of DDOS large flow defense framework of the present embodiment, protection platform comprises main server, miniature server and hidden server, and several miniature servers set up connection pool, by load balancing the IP and port that are connected with main server are mapped to each miniature server Hide the IP and port of the server, monitor the abnormality of the connection pool in real time, and quickly switch to the new IP and port when an abnormal IP is detected.
[0023] The number of individual IP and port access connections can be quantitatively controlled. When a certain number is reached, switch to a new IP, which can ensure that after an IP is attacked, only the current IP link will be affected, and other connections will still operate normally. .
[0024] When an abnormal IP is found, the abnormal connection will be quickly switched to a new IP and port, and the abnormal connection will be recorded; a batch of new IPs will be reassigned to the abnor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com