Concept lattice-based software credibility measurement method and device
A technology of concept lattice and credibility, applied in the direction of electronic digital data processing, instrument, platform integrity maintenance, etc., to avoid repeated measurement and speed up
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
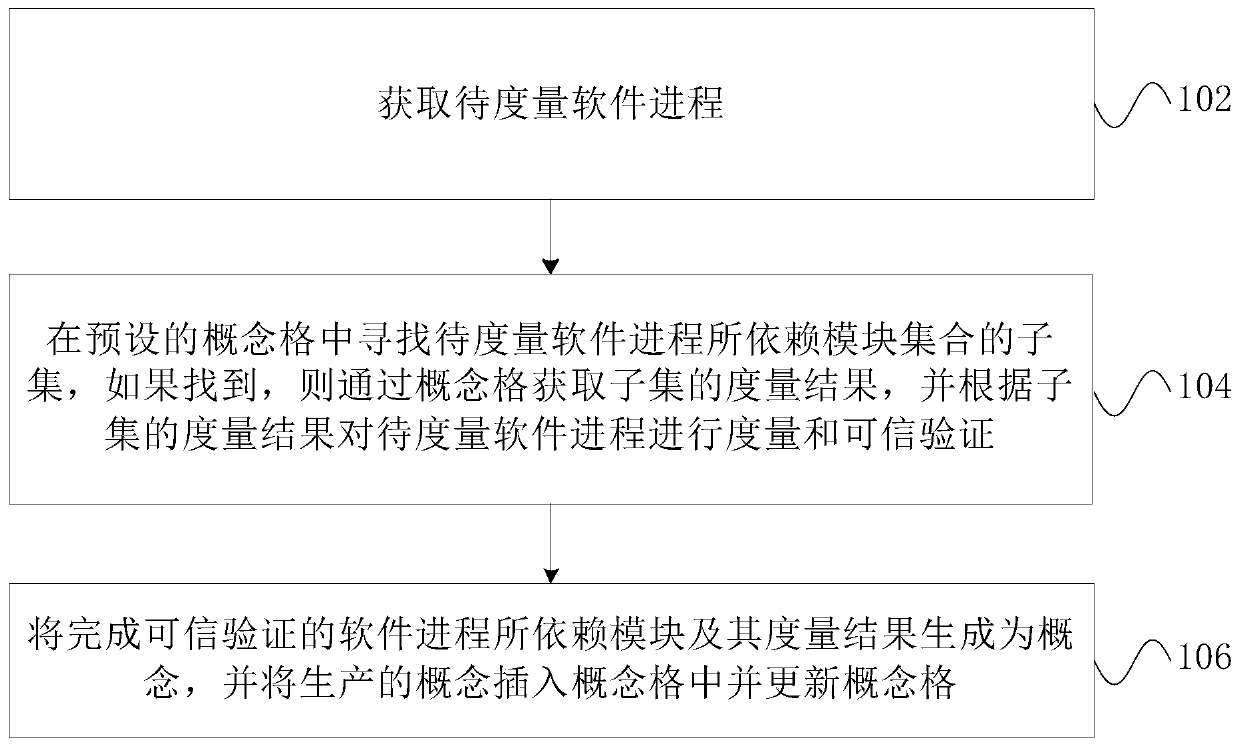
[0048] This embodiment provides a software credibility measurement method based on concept lattice, please refer to figure 1 , including the following steps:
[0049]Step 102, obtain the software process to be measured; the method for measuring software trustworthiness in this embodiment is to carry out trusted security maintenance for the entire computer operating system. When the computer operating system is started, the method starts. Each software process in the system performs trust measurement, which can passively obtain the software process to be measured, that is, the trust measurement method in this embodiment is set to a dormant state, and when each software process is started in the operating system, it is woken up for measurement , it can also be to actively acquire the software process to be measured, which can be acquired by actively scanning the software process in the operating system at an interval of time, and can also combine passive acquisition and active ...
Embodiment approach
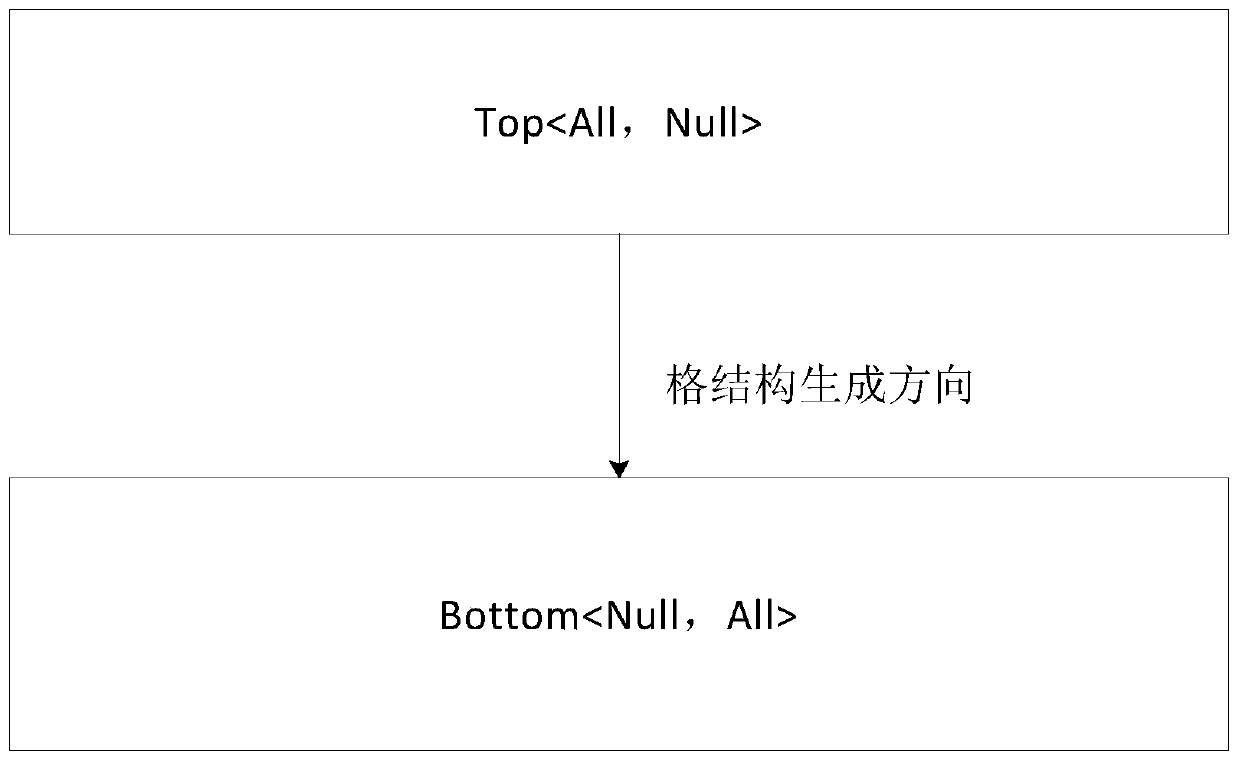
[0054] For the concept lattice, it is necessary to construct an initial concept lattice first. No concept with data is inserted in the initial concept lattice, which only includes the bottom concept and the top concept. Therefore, the preset concept lattice in this embodiment includes: The lattice structure generation direction generates bottom concept and top concept. The direction of lattice structure generation is the direction stipulated when constructing the concept lattice, which can be in various ways such as top-down or bottom-up. In one implementation mode, such as figure 2 As shown, the bottom concept and the top concept are generated according to the top-down direction; the top concept is set to maximize the extension and minimize the intension, and set the bottom concept to minimize the extension and maximize the intension. figure 2 Among them, the top concept top means and , that is, record the top concept as the concept top And the concept bottom, and form th...
Embodiment 2
[0075] See Figure 7 , on the basis of Embodiment 1, this embodiment provides a method for credible verification of dependent modules, including:
[0076] The measurement result of each dependent module is ANDed with the preset root of trust, and then the preset measurement benchmark and the calculation result are trusted and verified. If the trusted verification results are consistent, the dependent module is in a trusted state .
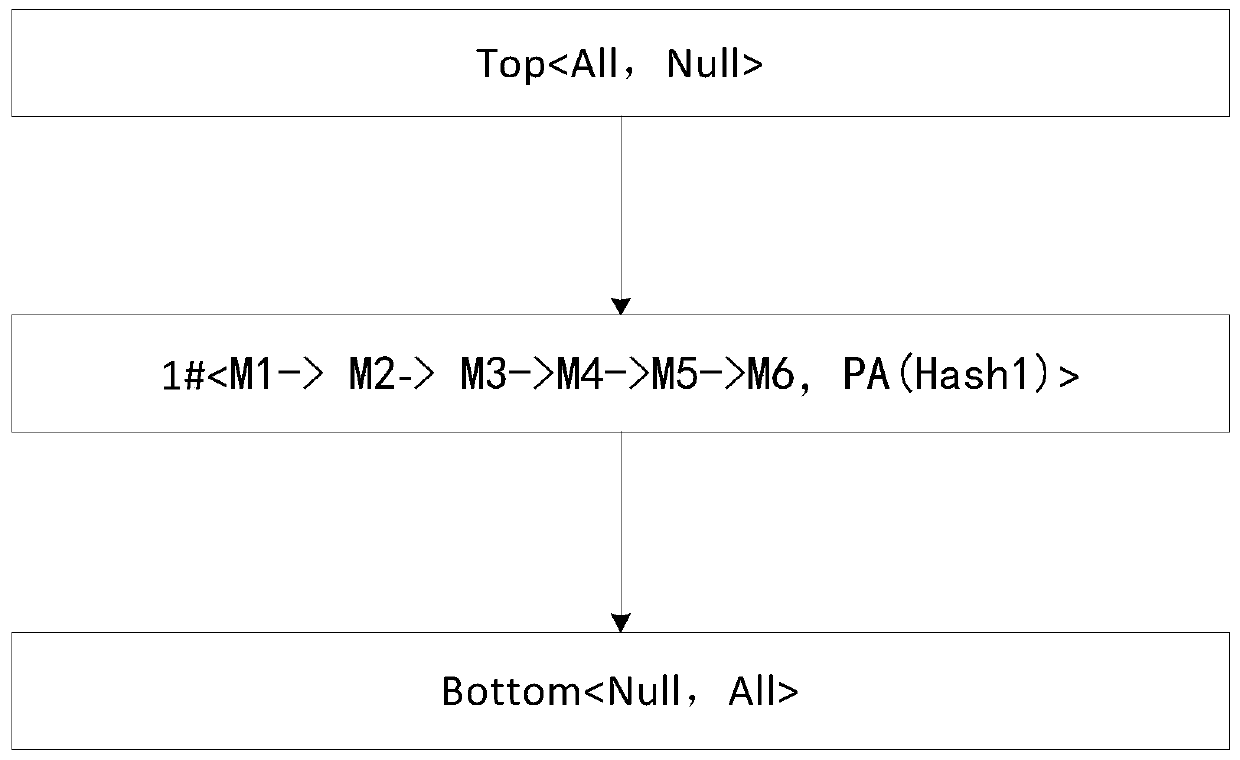
[0077] Such as Image 6 As shown, the measurement result of each dependent module is ANDed with the preset root of trust, for example, the measurement result Hash value 1 of the module Ntdll.dll is ANDed with the initial root of trust, and then the calculation result is compared with the predetermined A good measurement benchmark 1 is verified and compared. If the verification results are inconsistent, it means that the module Ntdll.dll has been tampered with. At this time, the measurement and trusted verification will be terminated and an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com