IP group identification method and device for abnormal user login
An identification method and identification device technology, which are applied in the field of network security and can solve the problems of inability to discover illegal behaviors of IPs that are independent of each other, and inability to detect illegal groups.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
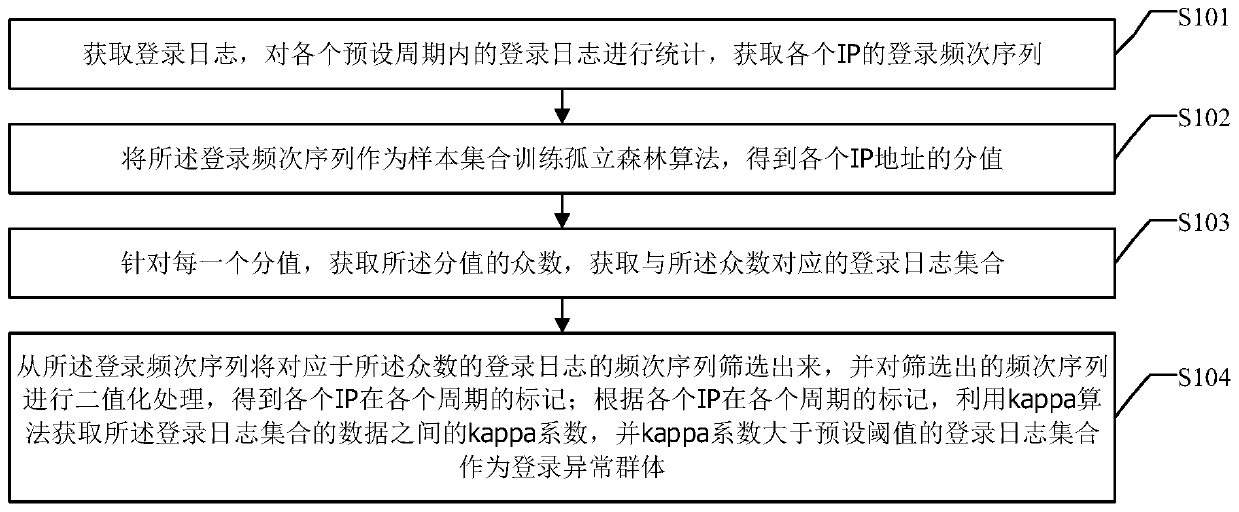
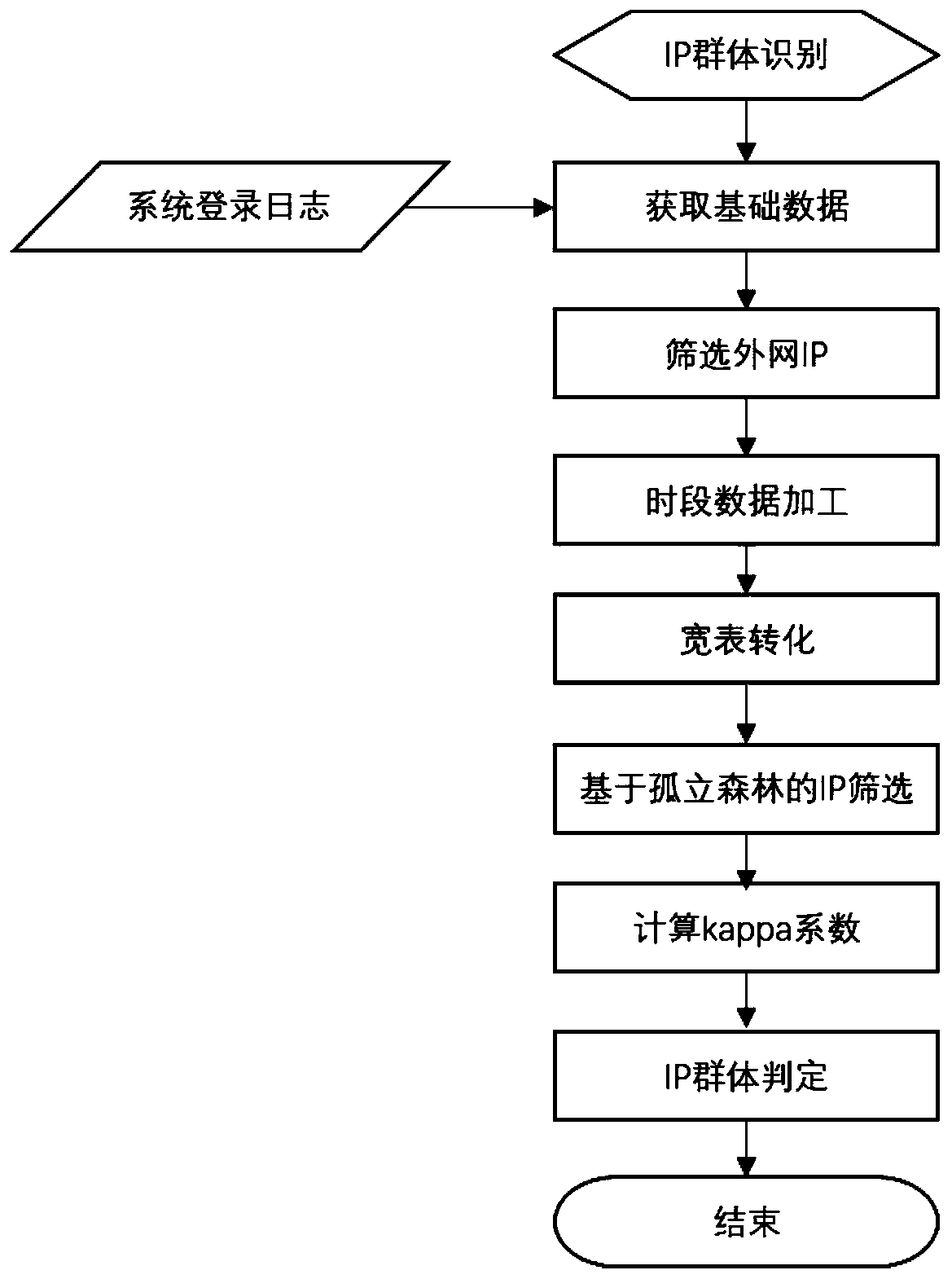
[0052] figure 1 It is a schematic flowchart of an IP group identification method for abnormal user login provided by an embodiment of the present invention; figure 2 A schematic diagram of the principle of an IP group identification method for abnormal user login provided by an embodiment of the present invention, as shown in figure 1 and figure 2 As shown, the method includes:
[0053]S101: Acquire login logs, make statistics on the login logs in each preset period, and acquire the login frequency sequence of each IP.
[0054] Exemplarily, the server login log within a day is obtained, and the number of logins of each IP in each period is counted with a preset period, such as half an hour, to obtain the login frequency subsequence of each period; Periods are sorted, and the corresponding login frequency subsequences are combined according to the order of periods to obtain the login frequency sequence of each IP.
[0055] Take half an hour as the time interval, divide 0-...
Embodiment 2
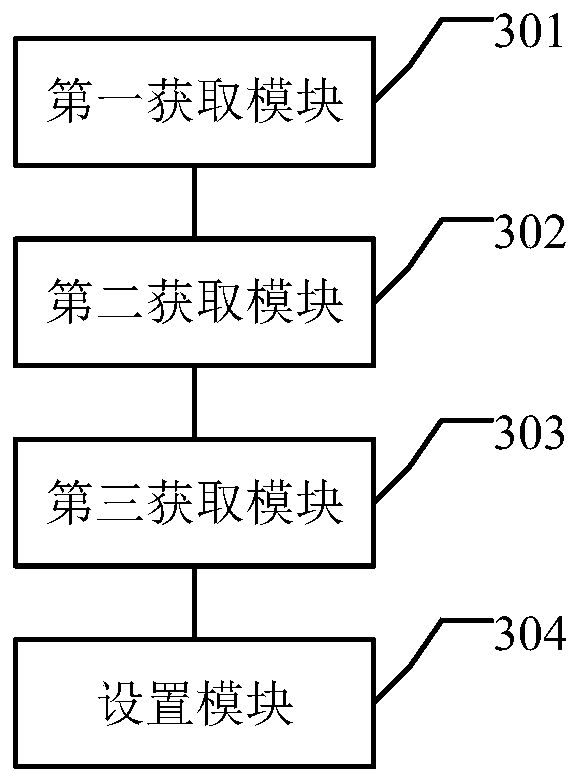
[0101] Corresponding to Embodiment 1 of the present invention, the embodiment of the present invention also provides an IP group identification device for abnormal user login.
[0102] image 3 A structural diagram of an IP group identification device with abnormal user login provided by an embodiment of the present invention, as shown in image 3As shown, the device includes:
[0103] The first obtaining module 301 is used to obtain the login log, perform statistics on the login log in each preset period, and obtain the login frequency sequence of each IP;
[0104] The second acquisition module 302 is used to use the login frequency sequence as a sample set to train the isolated forest algorithm to obtain the score of each IP address;
[0105] The third obtaining module 303 is used to obtain the mode of the score for each score, and obtain the log set corresponding to the mode;
[0106] The setting module 304 is used to filter out the frequency sequence of the login log co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com