Asymmetric image encryption method based on RSA and fractional order chaotic system
A chaotic system and encryption method technology, applied in digital transmission systems, secure communication through chaotic signals, transmission systems, etc., can solve the difficulties of incomplete restoration of plaintext images, secure key transmission and storage, and distribution and storage of symmetric encryption keys And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
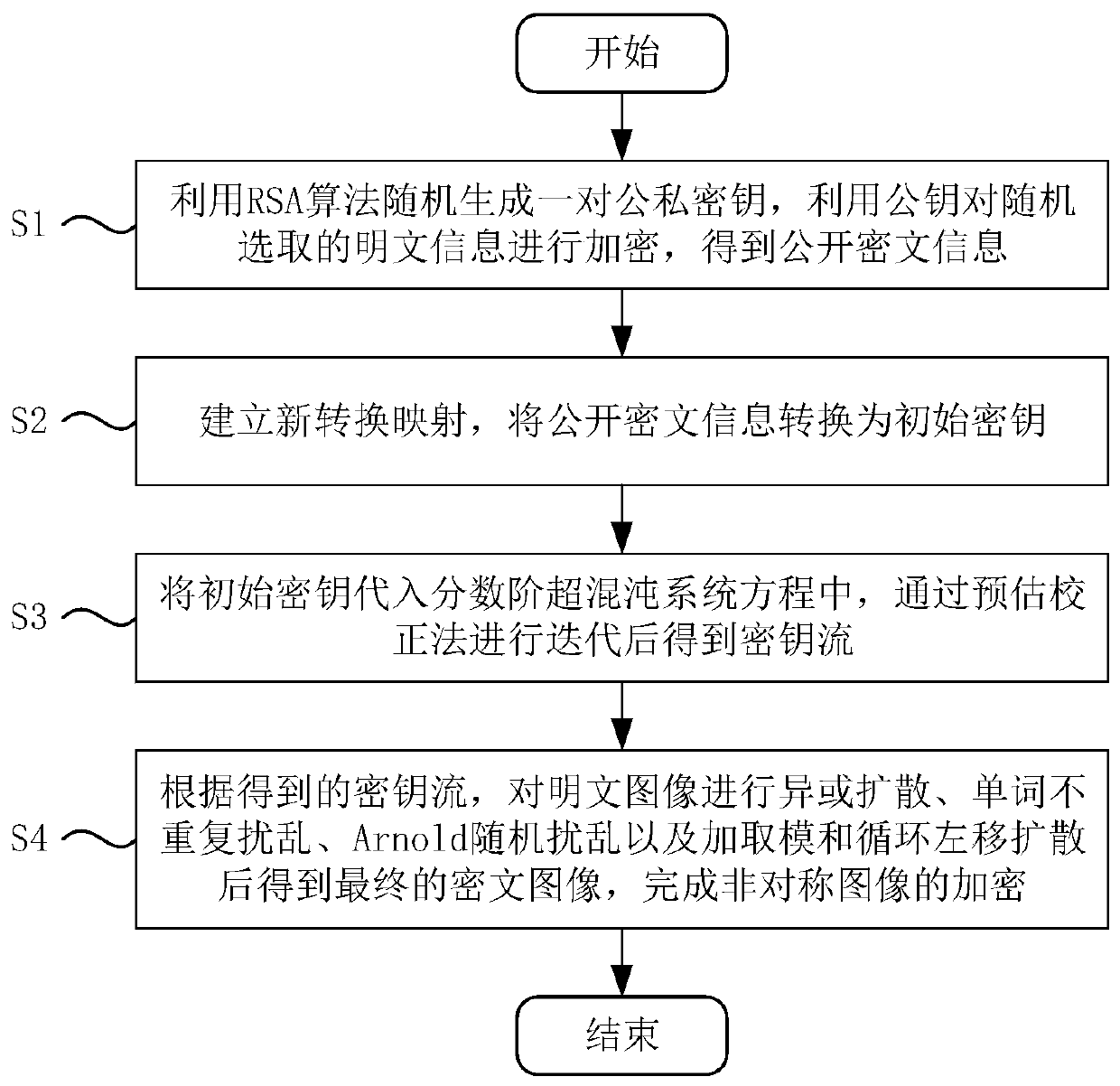
[0078] Such as figure 1 As shown, an asymmetric image encryption method based on RSA and fractional order chaotic system includes the following steps:
[0079] S1: Use the RSA algorithm to randomly generate a pair of public and private keys, use the public key to encrypt randomly selected plaintext information, and obtain public ciphertext information;
[0080] S2: Establish a new conversion map to convert the public ciphertext information into the initial key;
[0081] S3: Substitute the initial key into the fractional hyperchaotic system equation, and obtain the key stream after iterating through the estimation and correction method;
[0082] S4: According to the obtained key stream, the final ciphertext image is obtained after performing XOR diffusion, single non-repetitive perturbation, Arnold random perturbation, modulus and circular left shift diffusion on the plaintext image, and the encryption of the asymmetric image is completed.
[0083] In the specific implementat...
Embodiment 2
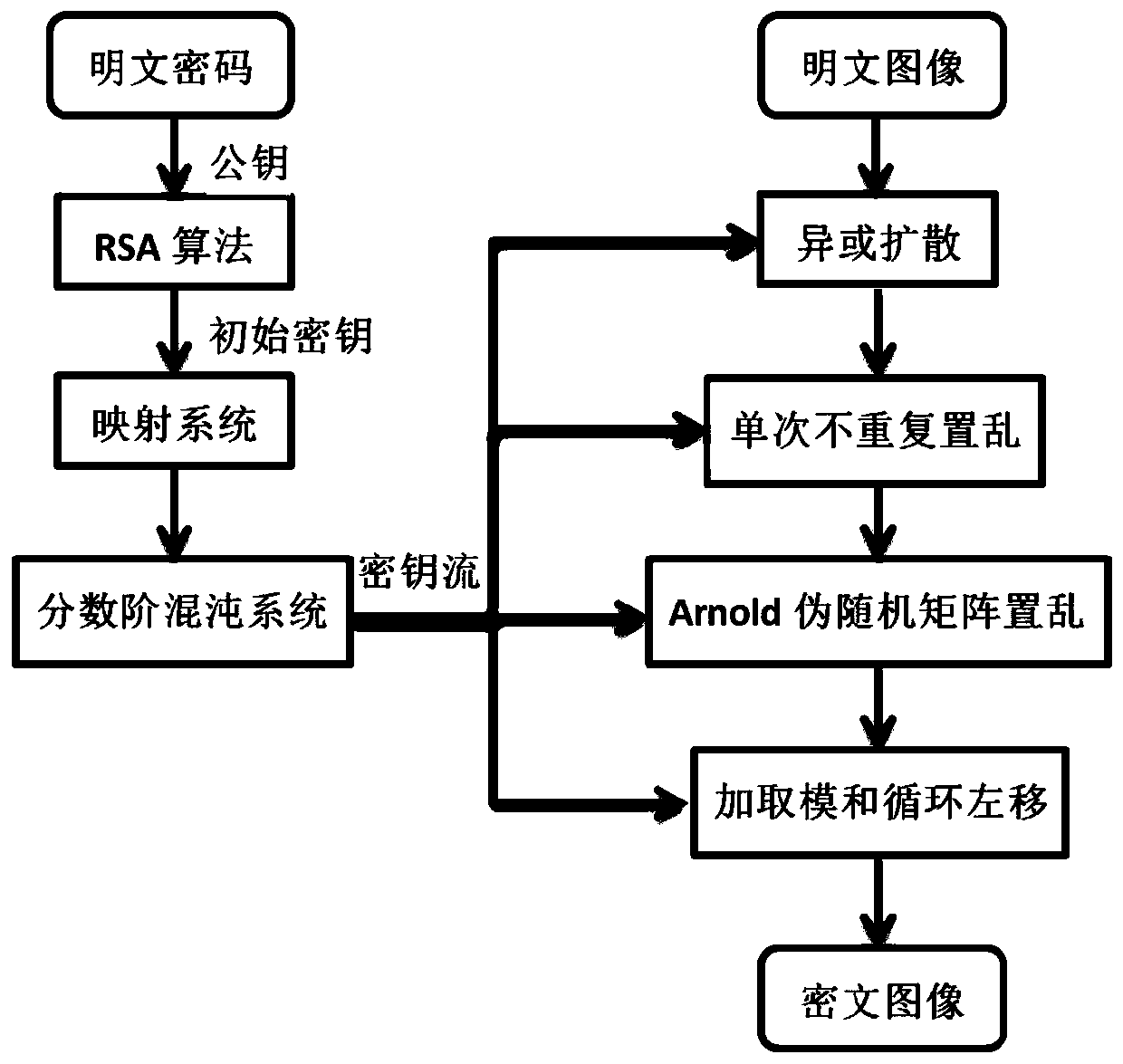
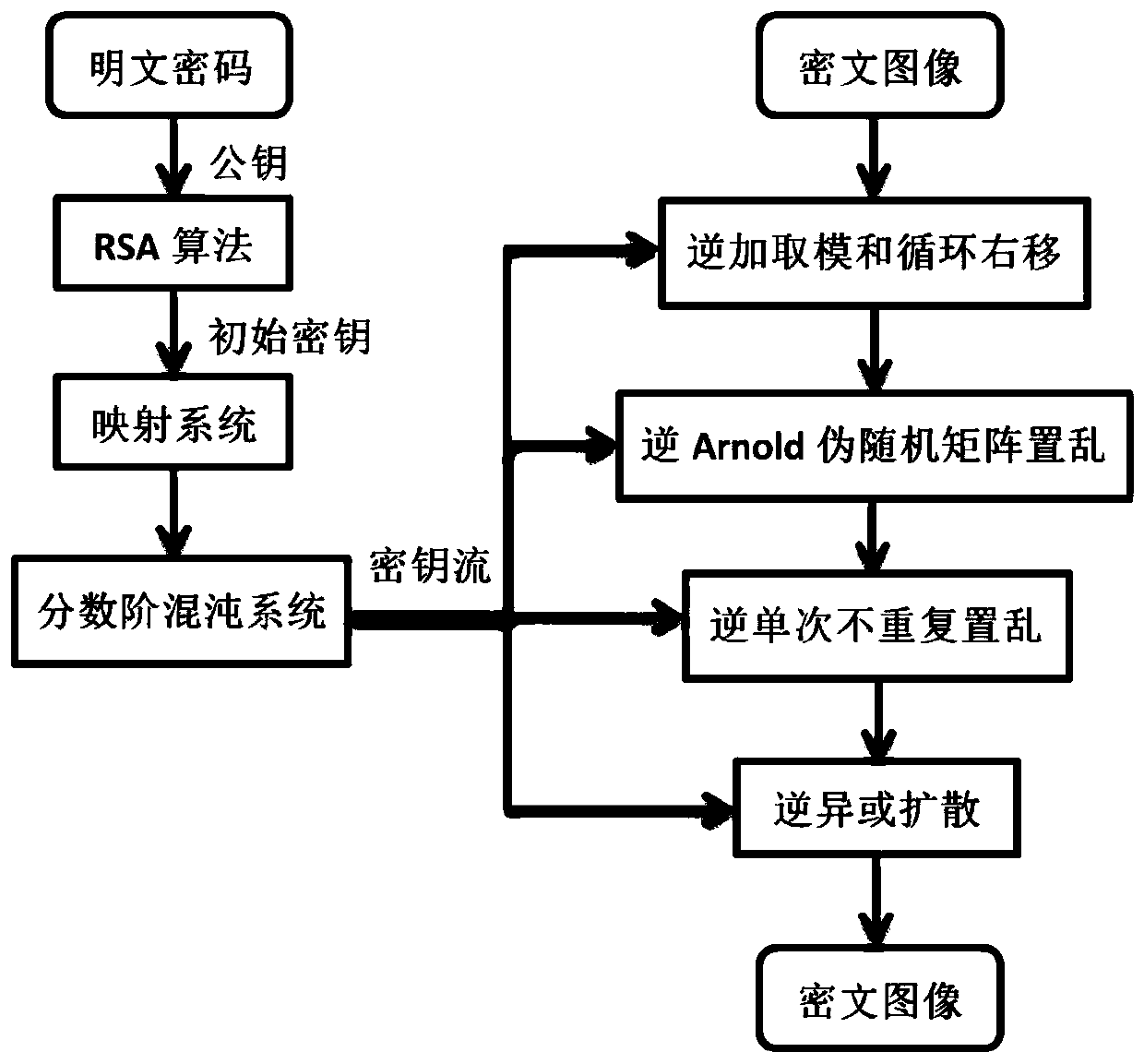
[0085] More specifically, on the basis of Example 1, such as figure 2 As shown in the frame diagram of image encryption, input: a plaintext image P with a size of M×N, two prime numbers p=857, q=877, and public key e=29. Set four plaintext passwords: m 1 =3,m 2 =5,m 3 =7,m 4 =9, integration time step h=0.01, number of iterations k1=5000, k2=5000, order α=0.9, control parameters a'=5.1, b'=8.6, c'=6, d'=2.7, e '=0.01, f'=-9.4. According to symmetry, image 3 It is the image decryption frame diagram of the present invention.
[0086] In the specific implementation process, first, the receiving party randomly selects two larger different prime numbers p and q, and calculates n=p×q and f(n)=(p-1)×(q-1); for the selected The p and q used as the key are strictly kept secret; the receiver finds an integer e that satisfies gcd(f(n),e)=1 and 1<e<f(n), and then according to the formula ed≡1(modf(n) ) is calculated to obtain an integer d; the integer pair (e, n) is a public key,...
Embodiment 3
[0120] In the specific implementation process, the present invention is in terms of security testing, such as Figure 7 The histogram of the original Lena plot shown, Figure 8 The histogram of the shown encrypted Lena image; it can be seen that the histogram of the original plaintext image is ups and downs, and the encrypted ciphertext histogram is very flat, so the method of the present invention is safe and effective. Figure 9 is the original all-black image, Figure 10 is an encrypted all-black image, Figure 11 is the original all-white image, Figure 12 is an encrypted all-white image.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com