A Two-way Identity Authentication Method Based on Single Photon
A two-way identity authentication, single-photon technology, applied in the field of quantum communication, to achieve the effect of easy implementation, easy operation, good fault tolerance and robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The application principle of the present invention will be described in detail below in conjunction with the accompanying drawings.
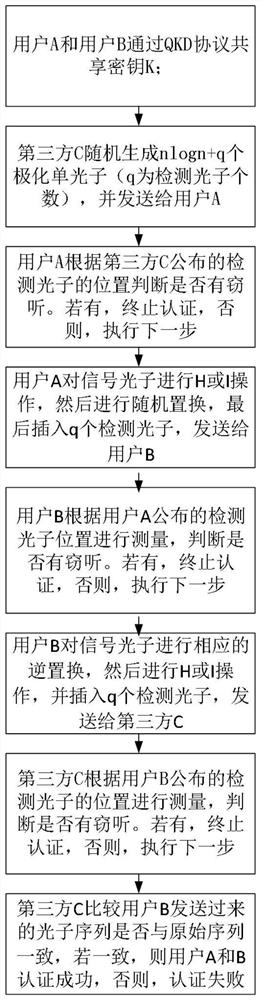
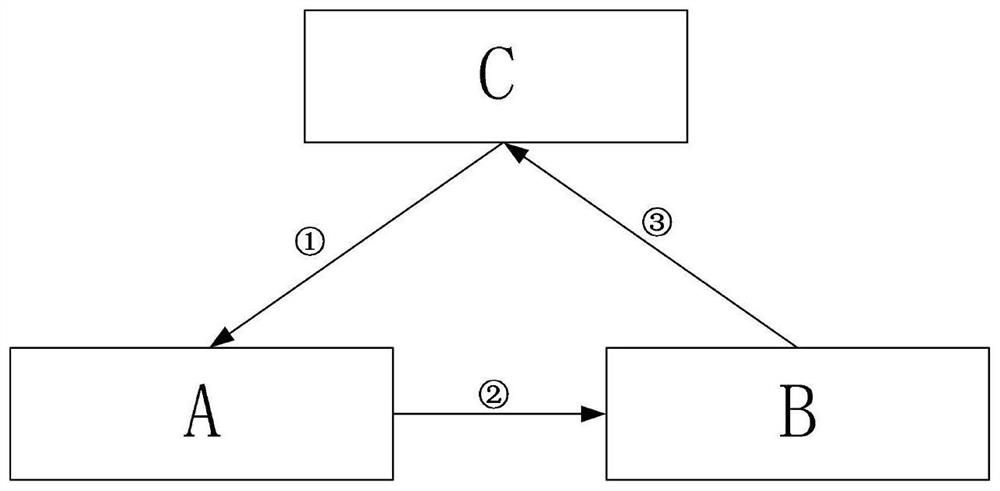
[0039] In this example, if figure 1 As shown, a two-way identity authentication method based on single photons is based on the quantum non-cloning and uncertainty theorem for wiretapping detection and identity authentication: firstly, the two sides of the authentication obtain the shared key through the quantum key distribution QKD protocol, and the semi-honest third party C generates and distributes the polarized single-photon sequence to authenticator A. Authenticator A performs corresponding operations on the polarized single-photon sequence and sends it to authenticator B. Authenticator B returns the polarized single-photon sequence after performing the corresponding operation. Two-way authentication is completed after C measurement; this protocol first distributes keys, then detects channel security, and then performs identity authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com