Internet of Vehicles communication control active security defense method and device
A communication control and active security technology, which is applied in the field of information security, can solve the problems of long-term eavesdropping, scanning and infiltration by the attacker, and achieve the effect of resisting network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
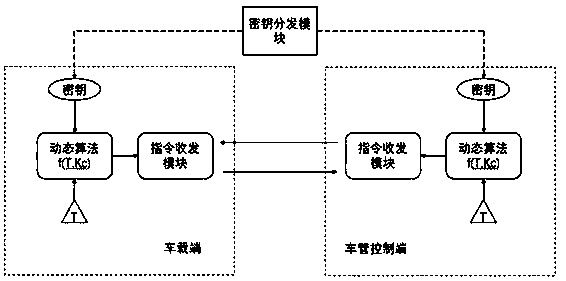
[0031] According to an embodiment of the present invention, there is an active security defense method based on the communication control of the Internet of Vehicles, the steps of which include:
[0032] 1) The vehicle terminal presets the differentiated key before distribution;
[0033] 2) Before communicating with the vehicle, the vehicle management control terminal uses a dynamic algorithm to generate random commands and returns them to the vehicle terminal along with the control commands;
[0034] 3) After receiving the control command, the vehicle terminal first calls the same dynamic algorithm to generate a random command and matches it with the received random command. If the verification is passed, the command is executed, and if the verification fails, the postscript command is refused to be executed;
[0035] 4) Return the command operation r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com