Access control method, device, computer device and computer-readable storage medium
A technology for access control and access equipment, applied in the field of information security, can solve problems such as unrelated, complex authority judgment, etc., and achieve the effect of reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
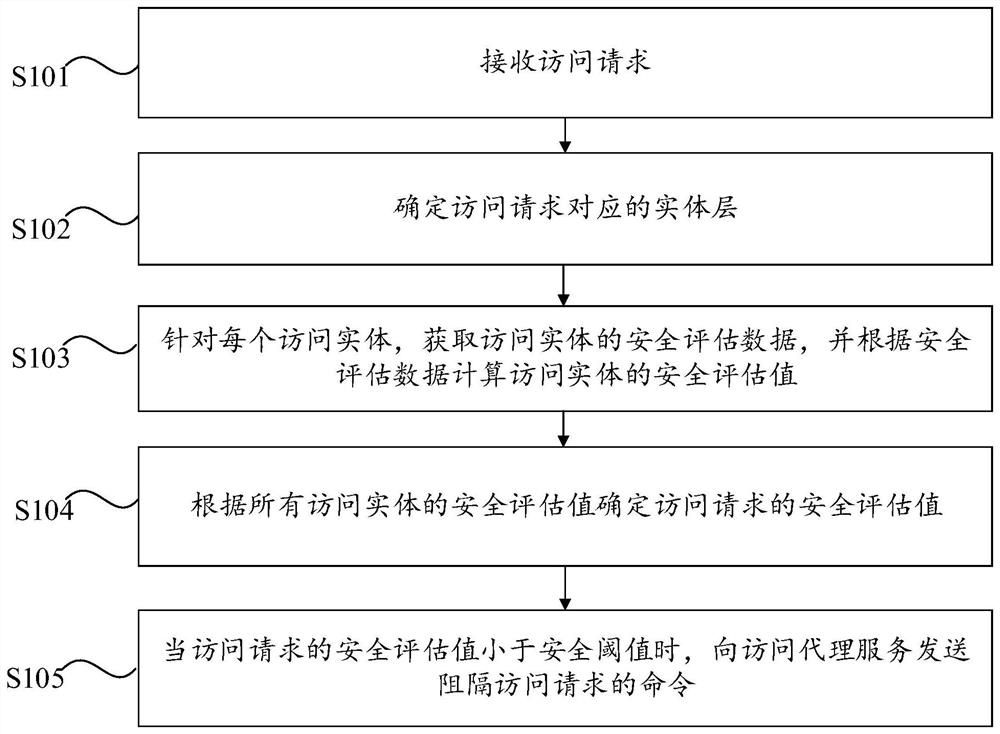
[0028] The first embodiment of the present invention provides an access control method, which can be applied to a "zero trust" system. In the system, a trusted proxy service is set between an access object and an access subject. The access provided by this embodiment As an access control service, the control method judges the access request received by the trusted proxy service, and controls whether the trusted proxy service forwards the access request sent by the access subject to the access object. Judgmental complexity, specifically, figure 1 It is a flowchart of the access control method provided by Embodiment 1 of the present invention. As shown in the figure, the access control method provided by Embodiment 1 includes the following steps S101 to S105.
[0029] Step S101: Receive an access request.
[0030] Specifically, the access request sent by the access subject first reaches the trusted proxy service, and the trusted proxy service sends the access request to the acc...
Embodiment 2
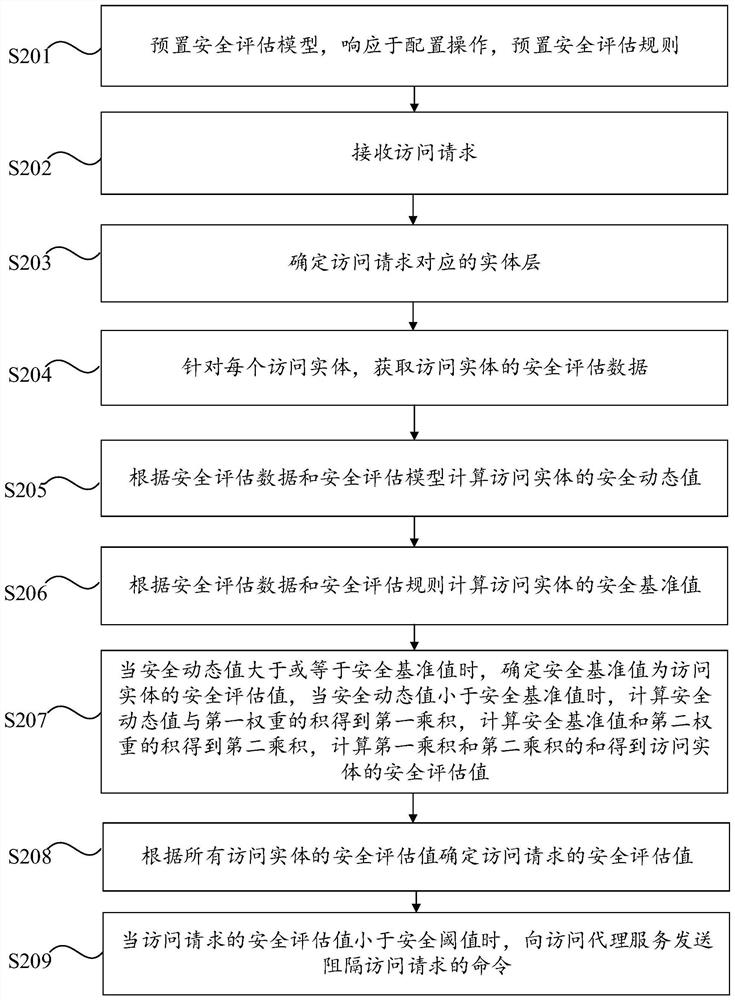
[0046] The second embodiment of the present invention provides a preferred access control method, so as to perform authority judgment on the access request received by the trusted proxy service, and then control whether the trusted proxy service forwards the access request sent by the access subject to the access object, Some technical features are the same as those of the above-mentioned first embodiment, and the specific description and corresponding technical effects may refer to the above-mentioned first embodiment. Further, in the second embodiment, the security assessment model and the security assessment rule are set at the same time, and the security assessment rule is used as the trust baseline, so as to exert the controllability of the trust baseline and the flexibility of the analysis model, improve the accuracy of the trust calculation, and reduce the complexity of the trust calculation. probability of misjudgment. specifically, figure 2 A flow chart of the acces...
Embodiment 3
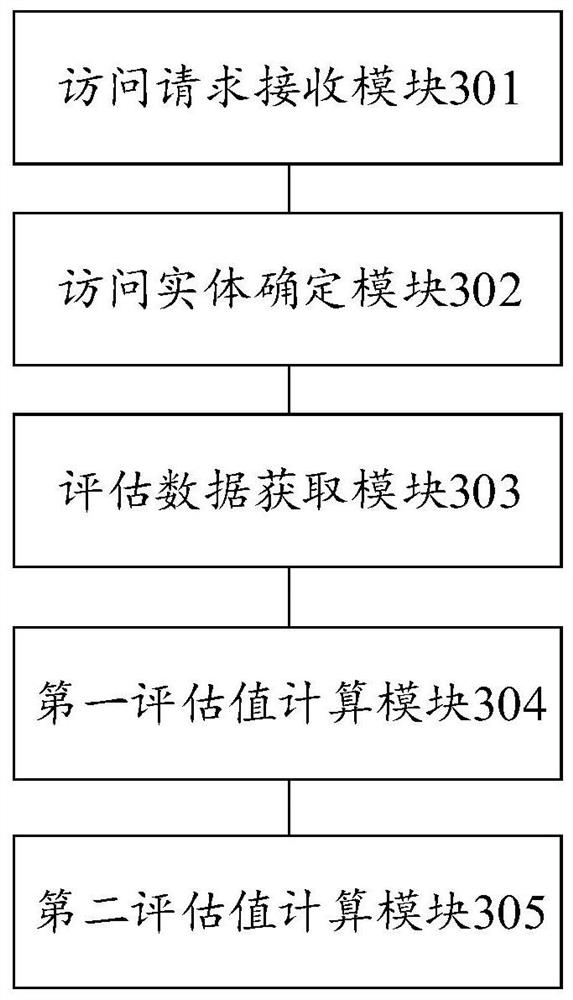
[0065] Corresponding to the above-mentioned first embodiment, the third embodiment of the present invention provides an access control apparatus, and the corresponding technical features and technical effects can be referred to the above, which will not be repeated here. image 3 A block diagram of an access control apparatus provided in Embodiment 3 of the present invention, such as image 3As shown, the apparatus includes an access request receiving module 301 , an access entity determining module 302 , an evaluation data acquisition module 303 , a first evaluation value calculation module 304 and a second evaluation value calculation module 305 .
[0066] The access request receiving module 301 is used to receive the access request; the access entity determination module 302 is used to determine the entity layer corresponding to the access request, wherein the entity layer includes four access entities, namely the access user, the access device, the access proxy service and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com