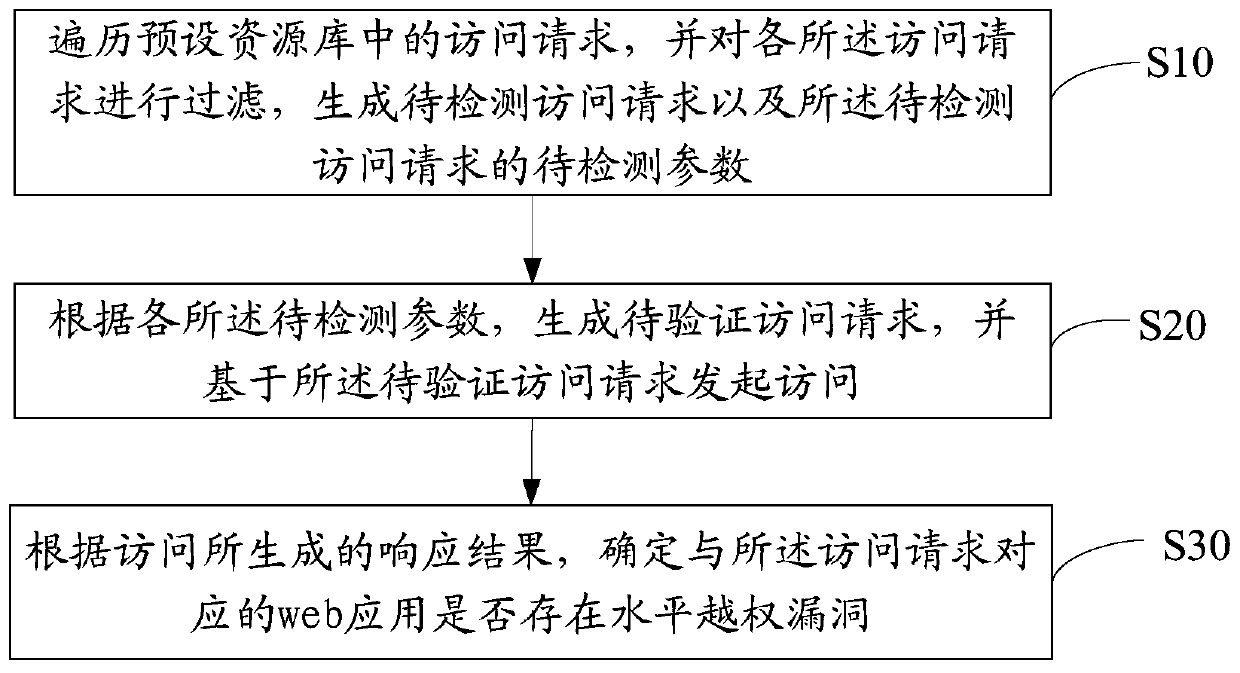
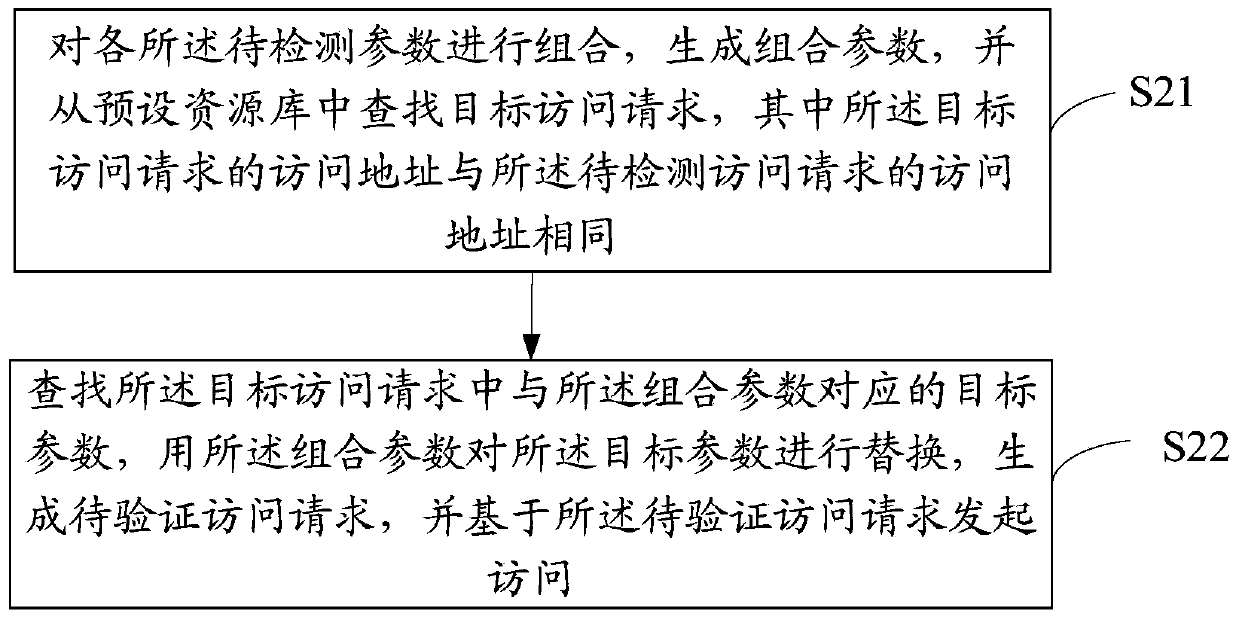
Horizontal unauthorized vulnerability detection method and device and computer readable storage medium
A vulnerability detection, level technology, applied in the Internet field to ensure flexibility and comprehensiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
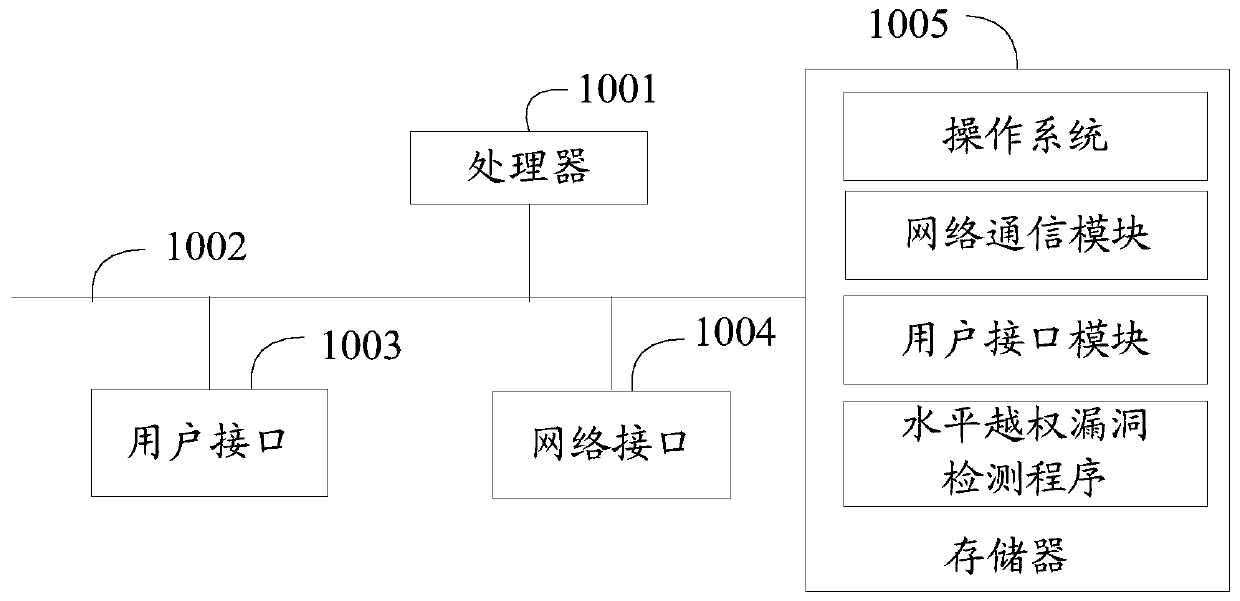
[0045] The present invention provides a horizontal unauthorized vulnerability detection device, referring to figure 1 , figure 1 It is a schematic structural diagram of the hardware operating environment of the device involved in the embodiment of the horizontal unauthorized vulnerability detection device of the present invention.
[0046] Such as figure 1 As shown, the horizontal unauthorized vulnerability detection device may include: a processor 1001 , such as a CPU, a communication bus 1002 , a user interface 1003 , a network interface 1004 , and a memory 1005 . Wherein, the communication bus 1002 is used to realize connection and communication between these components. The user interface 1003 may include a display screen (Display), an input unit such as a keyboard (Keyboard), and the optional user interface 10...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com