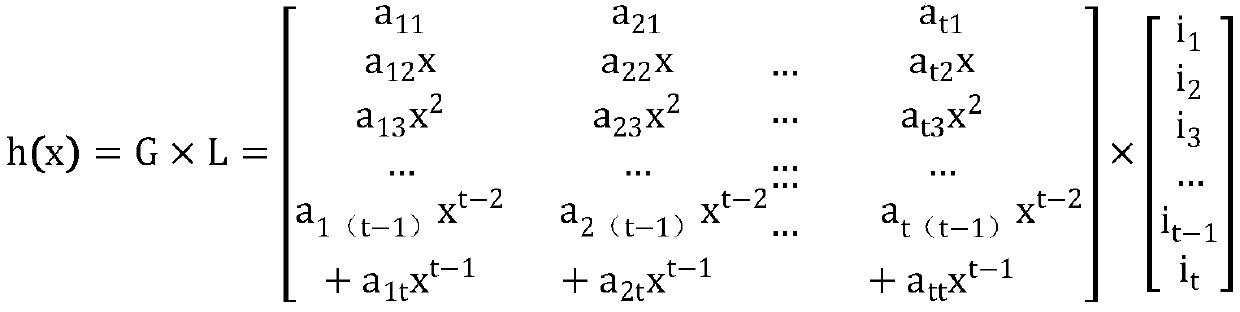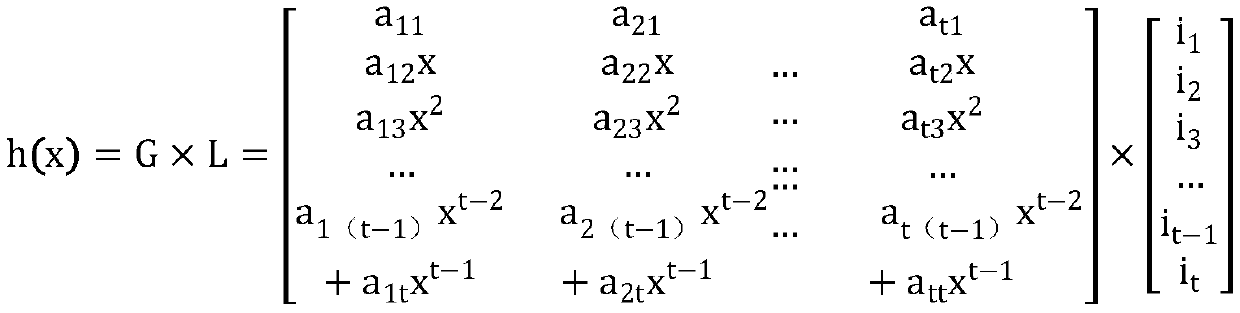Service path verification method for mimicry configuration in mimicry defense
A technology of path verification and service, applied in the field of network communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0042] In order to make it easier for those skilled in the art to understand and realize the present invention, the technical solution of the present invention is now further described, and a specific implementation manner of the present invention is given.
[0043] The controller generates switch path verification identifiers A, B, and C of a service chain according to the polynomial, and configures them on the switch respectively. When the data packet passes through the switch, it will trigger a packet_in message to be sent to the controller, carrying the switch path verification identifier, indicating that the data packet After passing through the switch currently, when the data packet reaches the destination, the controller collects the switch path verification identifier sent by the switch through which the data packet passes. Flow1 results in switches S1, S2, and S4, and sends them to controllers A, B, and C for switch path verification IDs. By comparing the switch path v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com