Security analysis method of AADL (Advanced Analysis and Design Language) model based on smartIflow
An analysis method and security technology, applied in the field of security analysis of the AADL model, can solve the problems of large description granularity, insufficient description, and difficulty in analysis and verification of security attributes, so as to achieve accurate security analysis results and comprehensive behavior descriptions. , The effect of safety analysis results improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
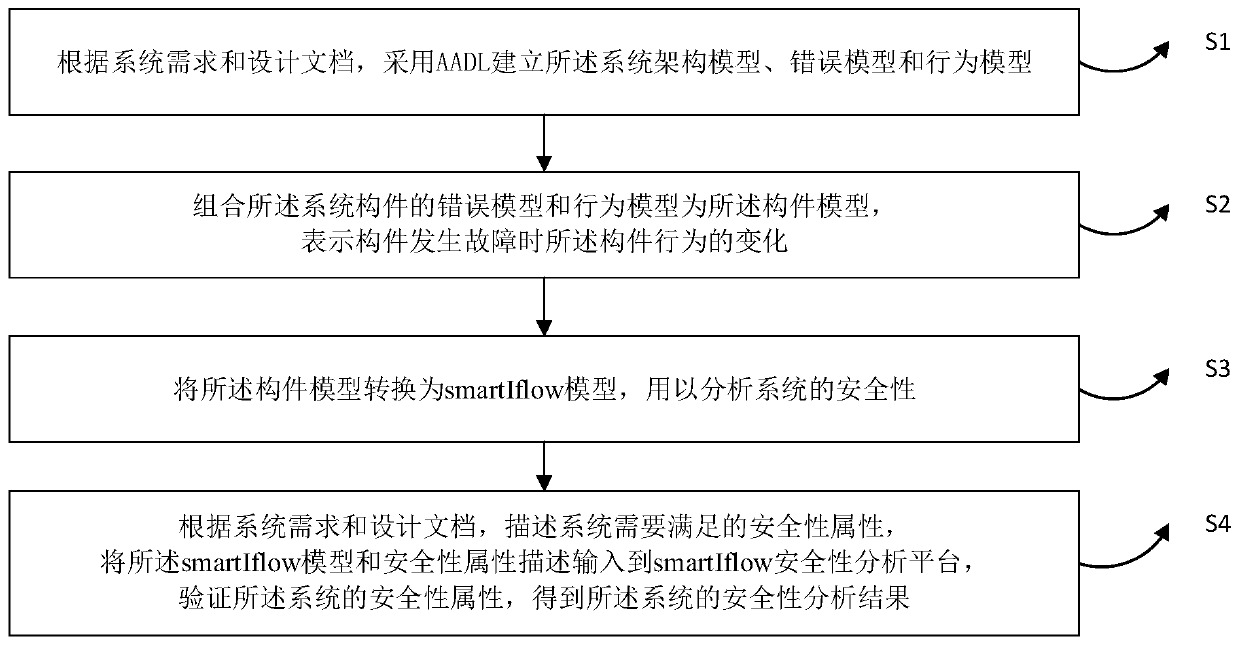
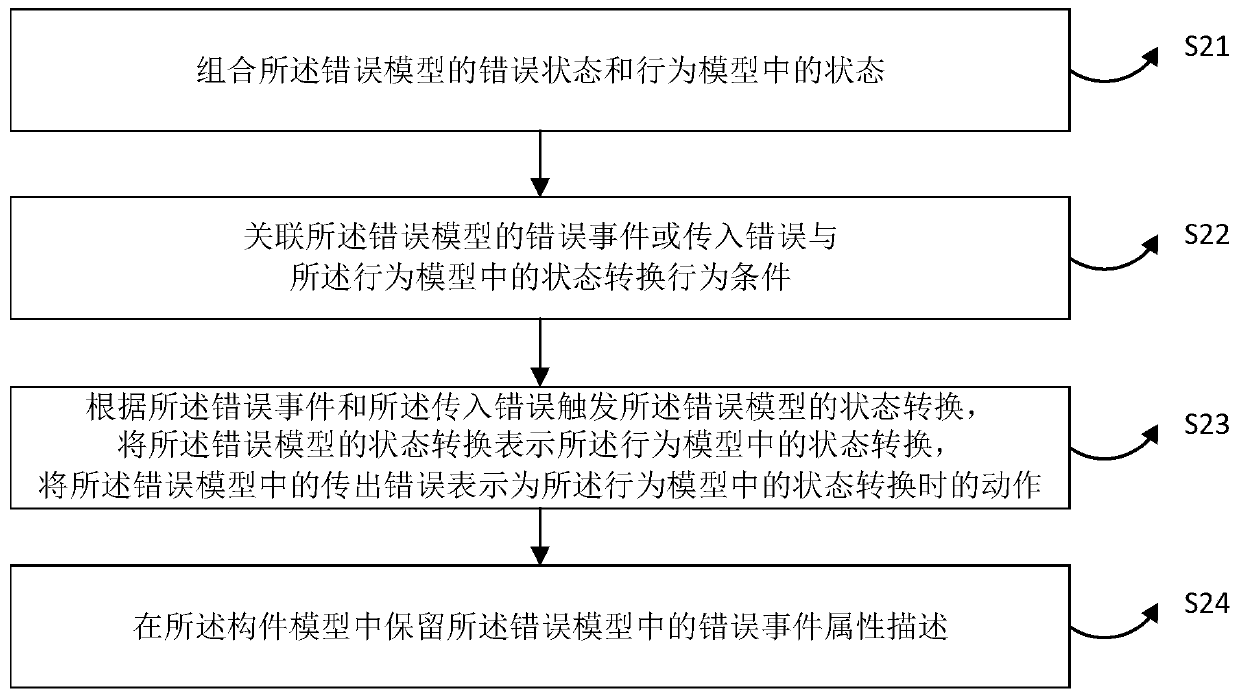
[0037] In order to make the above objects, features and advantages of the present application more obvious and understandable, the embodiments of the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
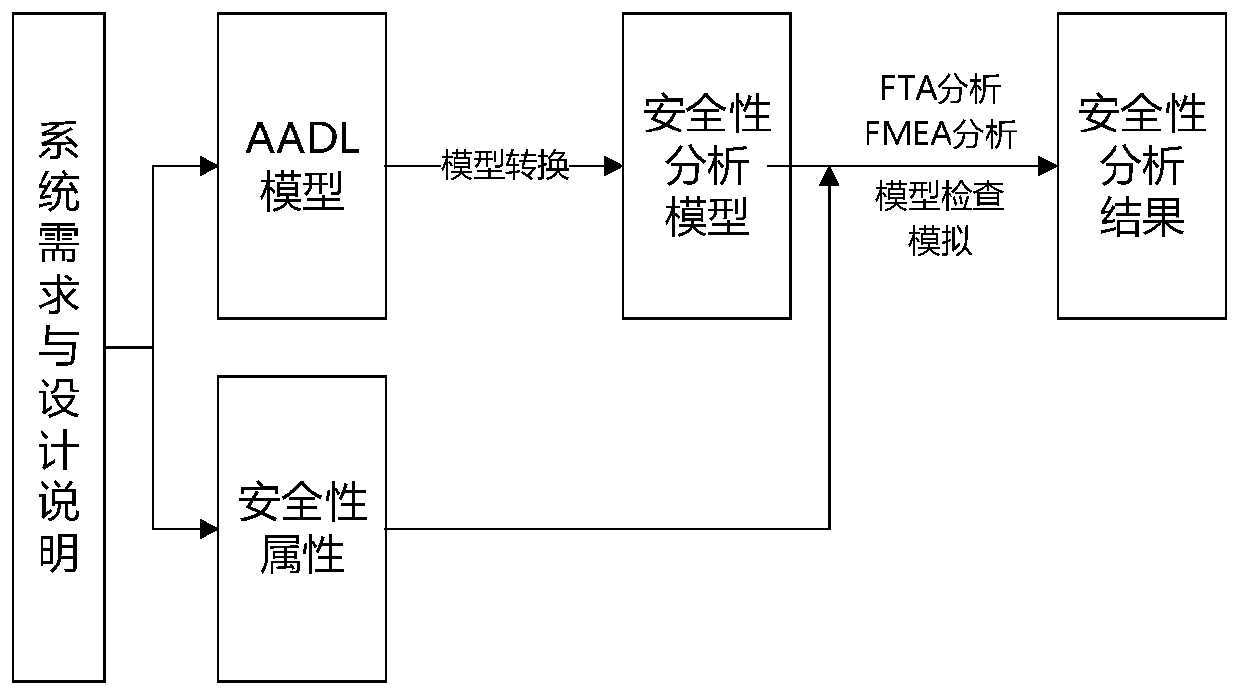
[0038] In terms of AADL model conversion, in order to reduce the semantic difference before and after model conversion and improve the accuracy of security analysis, it is very important to select the appropriate AADL subset and target model.
[0039] At present, Altarica, SAML, smartIflow, etc. can support FLM and FEM at the same time, which can fully model the safety system failure situation and obtain accurate safety analysis results.
[0040] smartIflow has: a moderate level of abstraction, which can analyze security requirements through model detection and other methods, and the calculation amount will not be too large; it supports two-way connection modeling, which is closer to re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com