Public key encryption and decryption method and system with double supervisors
A public key encryption, public key technology, applied in transmission systems, digital transmission systems, key distribution, can solve problems such as asset insecurity, and achieve the effect of solving supervision problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
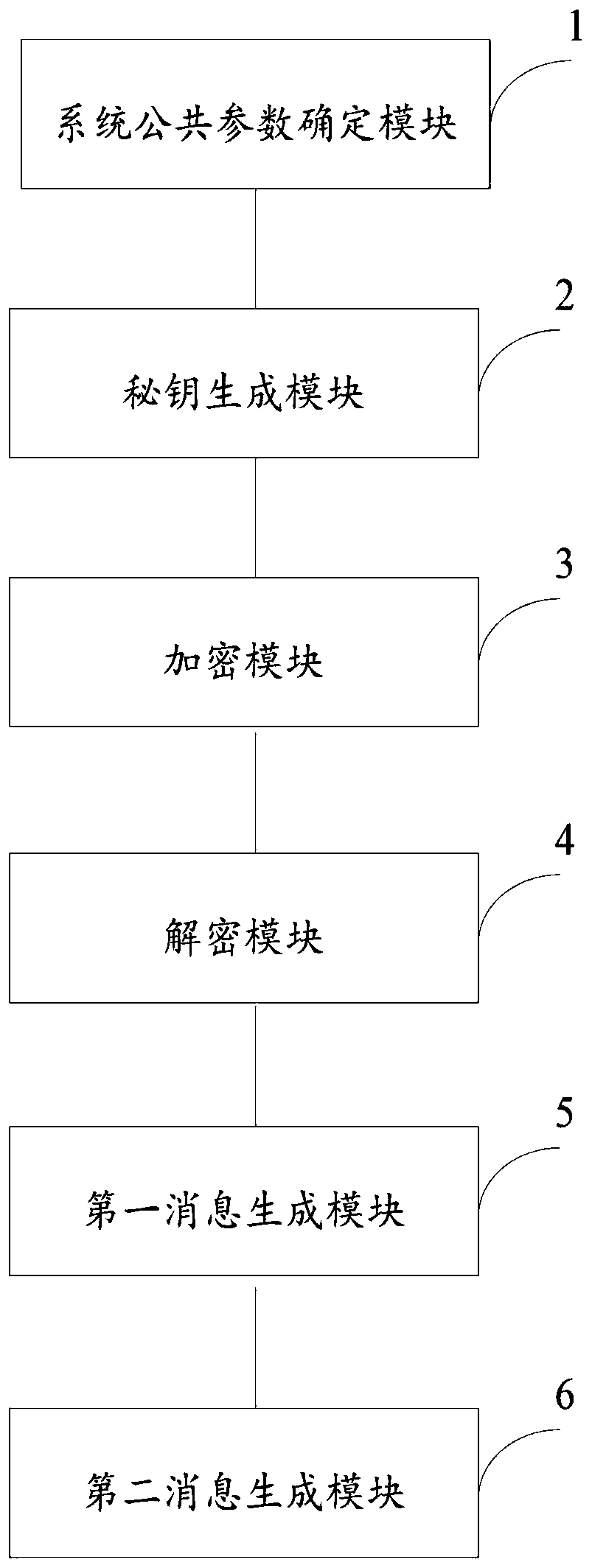
Image
Examples
Embodiment 1
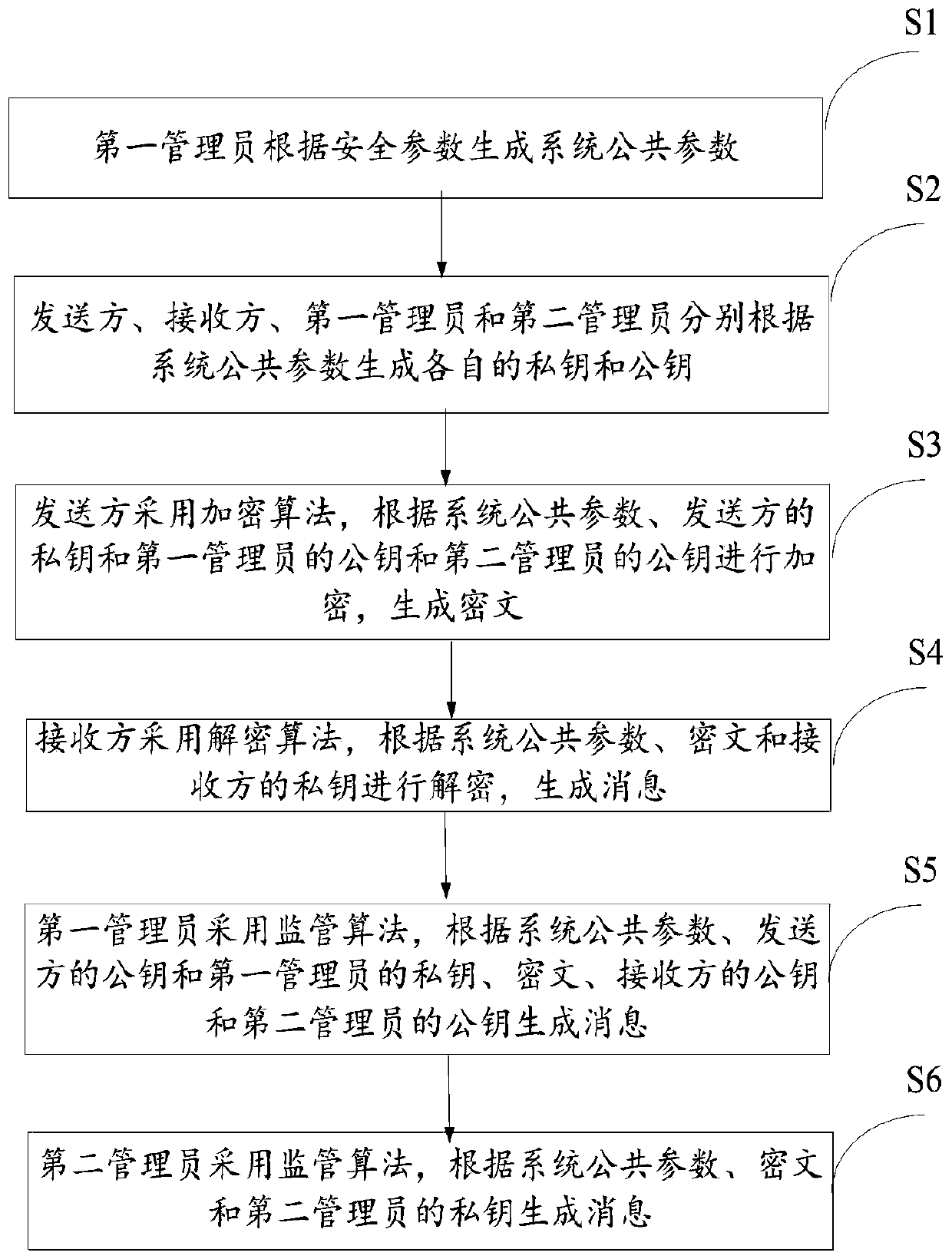
[0066] Step S1: The first administrator generates system public parameters according to the security parameters, and the specific formula is:
[0067] Param←Initialize(1 λ );
[0068] Among them, 1 λ is the security parameter, Initialize is the initialization algorithm, Param is the system public parameter, Param={e,G,g,H 1 ,H 2}, symmetric bilinear map e:G×G→G T , the generator of the group G is g, and the hash function H 1 :{0, 1} 2n → {0, 1} n ; Hash function H 2 :G T →{0,1} n .
[0069] Step S2: The sender, the receiver, the first administrator and the second administrator respectively generate their own private key and public key according to the system public parameters, specifically including:
[0070] Step S21: The sender uses the secret key generation algorithm to determine the private key and public key of the sender according to the system public parameters and the first secret random number. The specific formula is:
[0071] (SK 1 , PK 1 )←KGen(Param,...
Embodiment 2
[0103] Step S1: The first administrator generates system public parameters according to the security parameters, and the specific formula is:
[0104] Param←Initialize(1 λ );
[0105] Among them, 1 λ is the security parameter, Initialize is the initialization algorithm, Param is the system public parameter, Param={e,G,g,H 1 ,H 2}, symmetric bilinear map e:G×G→G T , the generator of the group G is g, and the hash function H 1 :{0, 1} 2n → {0, 1} n ; Hash function H 2 :G T →{0,1} n .
[0106] Step S2: The sender, the receiver, the first administrator and the second administrator respectively generate their own private key and public key according to the system public parameters, specifically including:
[0107] Step S21: The sender uses the secret key generation algorithm to determine the private key and public key of the sender according to the system public parameters and the first secret random number. The specific formula is:
[0108] (SK 1 , PK 1 )←KGen(Param,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com