Wireless energy supply full duplex relay cooperation secret transmission method and system
A wireless energy supply and confidential transmission technology, applied in the field of communication systems, can solve the problems of information leakage, difficulty for legitimate communication users to obtain perfect eavesdropping channel status information, system security performance degradation, etc., and achieve the effect of multiplexing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
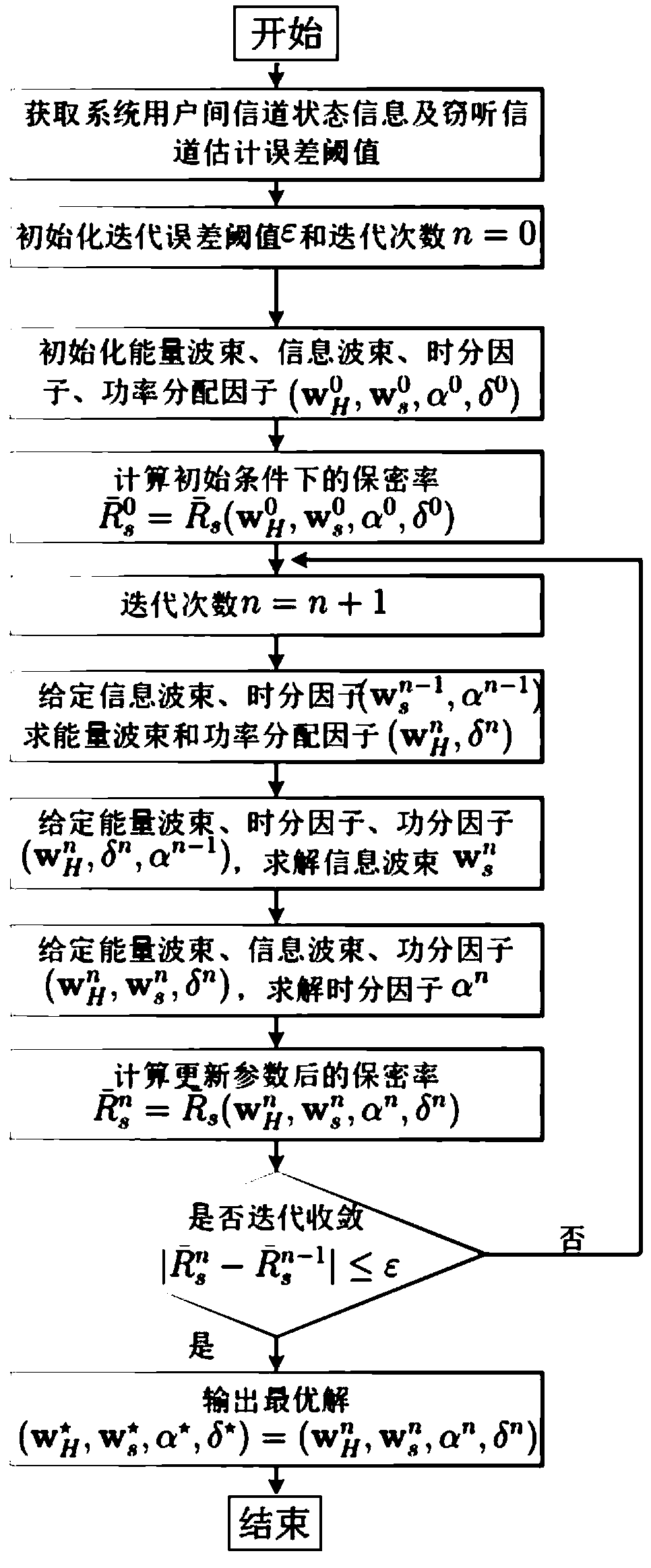
[0033] Such as figure 1 As shown, this embodiment provides a secure transmission method for wireless powered full-duplex relay cooperation, and the specific steps include:
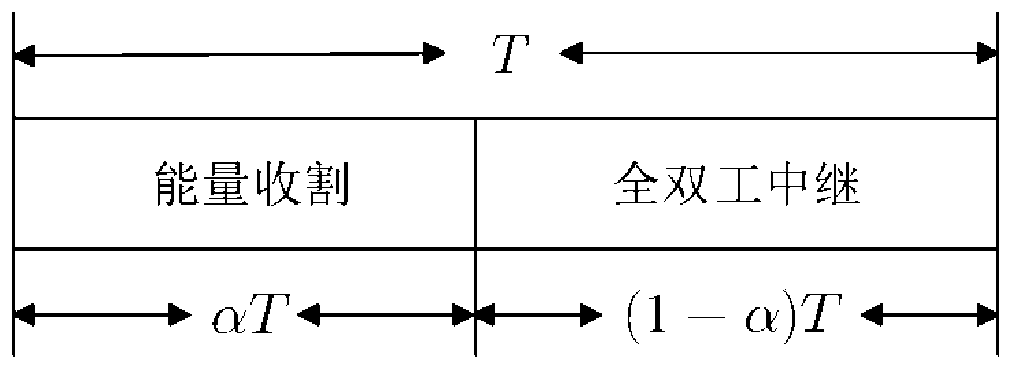
[0034] S1: The relay receives the energy signal sent by the source to harvest energy;
[0035] S2: The relay receives the information carrying the privacy signal sent by the source, uses the harvested energy to forward the information to the legitimate receiver, and eavesdrops on the user to receive the information;
[0036] S3: Calculate the lower bound of the secrecy rate under the imperfect eavesdropping channel state according to the information received by the legal receiver and the eavesdropping user;
[0037] S4: Construct the optimization problem of maximizing the secrecy rate according to the energy beam, information beam, time division factor and power allocation factor;
[0038] S5: Decompose the non-convex optimization problem into three sub-optimization problems, and use the iterative conver...
Embodiment 2
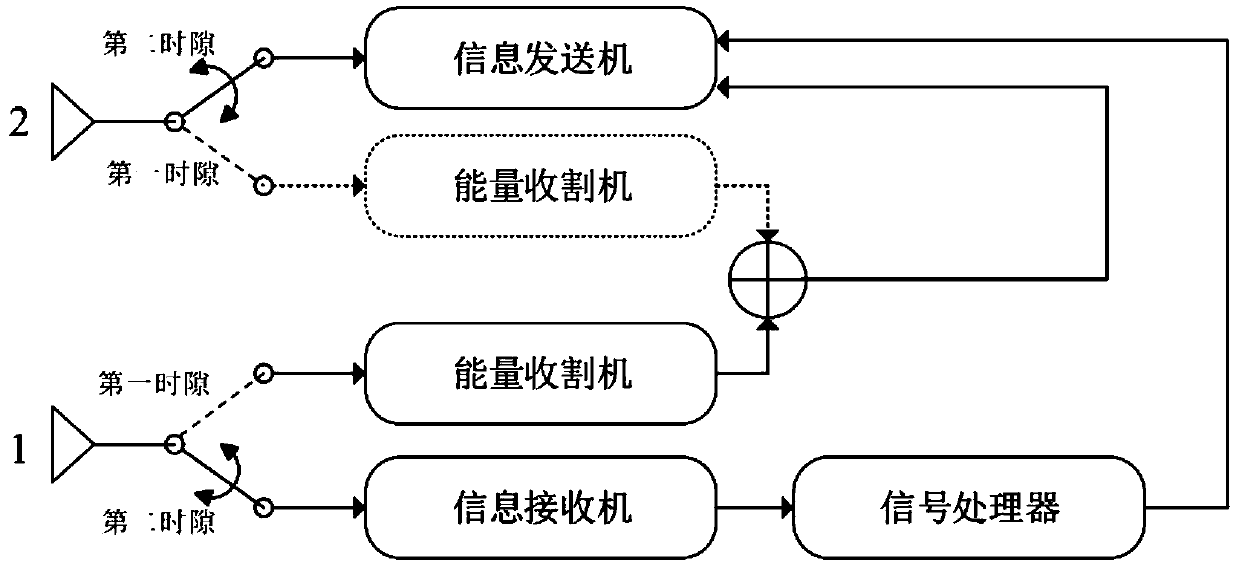
[0088] This embodiment provides a secure transmission system for full-duplex relay cooperation with wireless power supply, such as Image 6As shown, including a wireless power supply full-duplex cooperative relay model and a secure transmission module;
[0089] The wireless power supply full-duplex cooperative relay model includes a source, a legal receiver, a relay, and an eavesdropping user;
[0090] The relay receives the energy signal sent by the information source, and performs energy harvesting;
[0091] The relay receives the information carrying the privacy signal sent by the information source, uses the harvested energy to forward the information to the legal receiving end, and eavesdrops on the user to receive the information;
[0092] In this system, the information source is equipped with N antennas, which is a multi-antenna information source; all receivers, legal receivers and eavesdropping users are equipped with only one antenna due to terminal space constrain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com