Big data network data protection method and system based on edge computing
A technology for network data and protection systems, applied in the field of network security, which can solve problems such as heavy server load and system crashes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
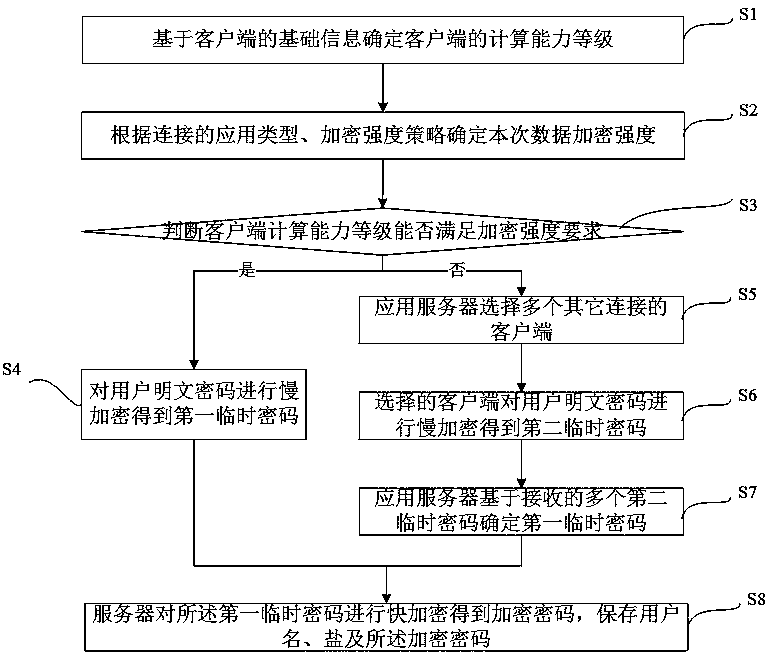
[0085] Such as figure 1 As shown, this embodiment proposes an edge computing-based big data network data protection method, especially a method for encrypting private data such as user passwords, including:
[0086] S1. Determine the computing power level of the client based on the basic information of the client;
[0087] In the era of big data, the amount of user data is increasing rapidly. In order to overcome the problem of overloading the server in the server-based data protection method, the present invention performs part of the data protection calculation based on the client to effectively reduce the processing cost of the server. With the popularization of terminal devices and the development of the Internet of Things in the future, terminal devices are becoming more and more diverse, and the performance on the client side is getting stronger and stronger, which makes it possible to migrate some computing tasks from servers to mobile terminals. Therefore, the present...
Embodiment 2
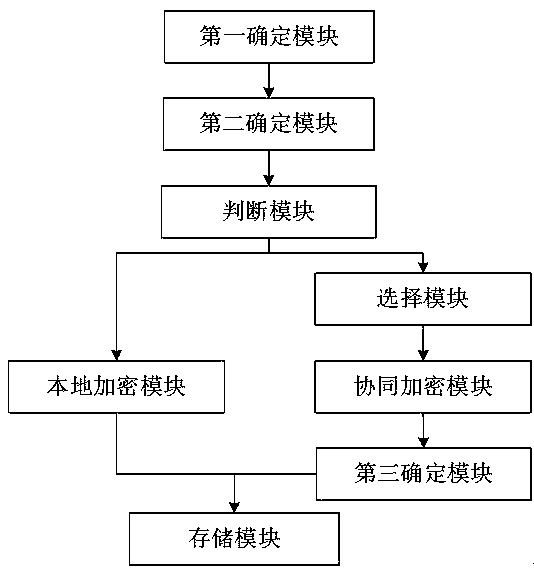
[0139] Such as figure 2 As shown, this embodiment proposes a big data network data protection system based on edge computing, especially a system for encrypting private data such as user passwords, including:
[0140] A first determining module, configured to determine the computing capability level of the client based on the basic information of the client;
[0141] In the era of big data, the amount of user data is increasing rapidly. In order to overcome the problem of overloading the server in the server-based data protection method, the present invention performs part of the data protection calculation based on the client to effectively reduce the processing cost of the server. With the popularization of terminal devices and the development of the Internet of Things in the future, terminal devices are becoming more and more diverse, and the performance on the client side is getting stronger and stronger, which makes it possible to migrate some computing tasks from server...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com