Steganographic method of unsupported text based on linguistic steganographic feature space
A feature space, carrier-free technology, applied in the field of text information hiding, can solve the problems of poor versatility and small hiding capacity, and achieve the effect of large steganographic capacity, good concealment, and strong robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
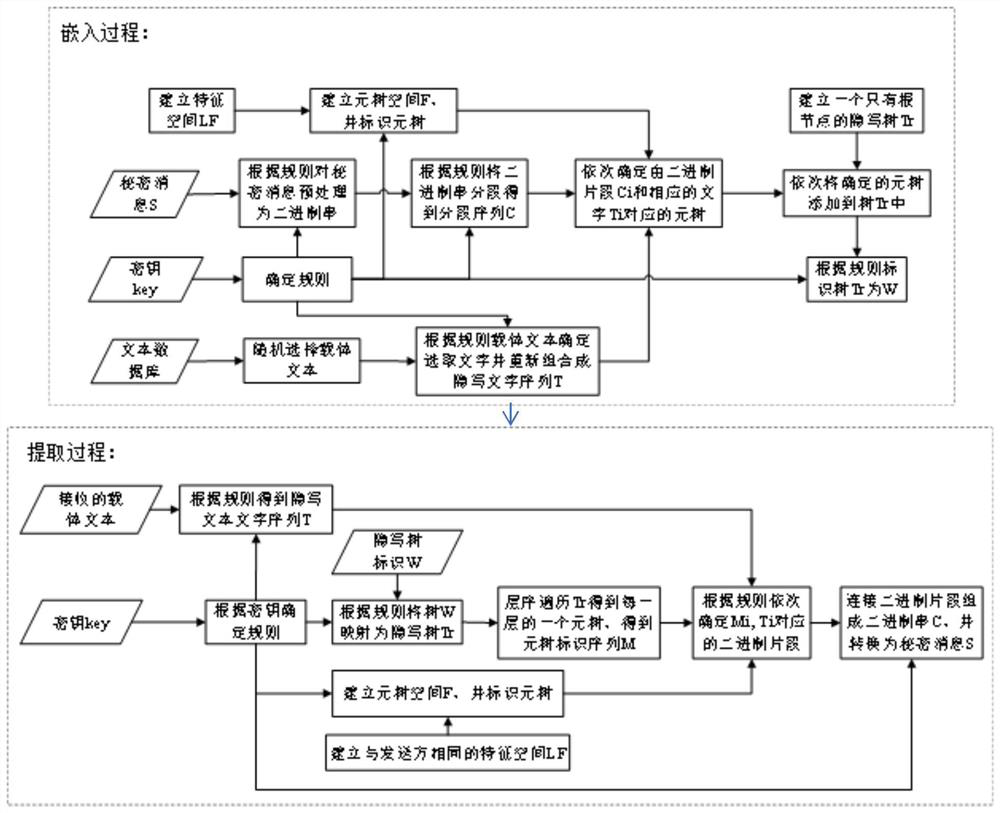
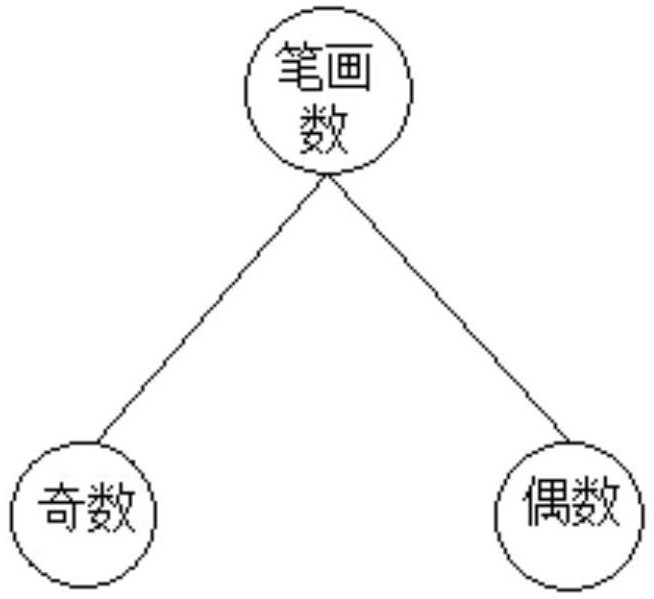
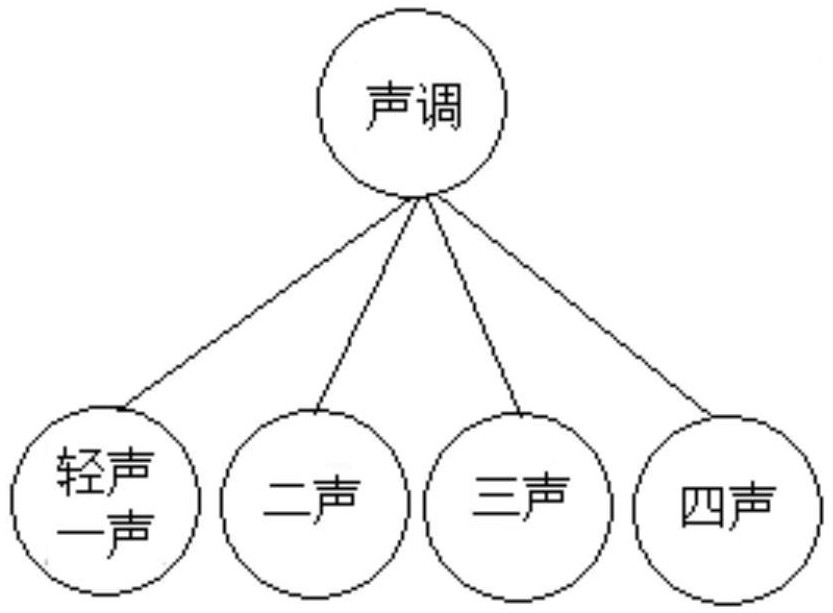
[0045] This specific implementation is based on Chinese characters, and only three different features are selected as examples for illustration, which are the number of strokes, the tone of the pinyin, and the structure of Chinese characters.
[0046] Here we define the simplest mapping relationship between the key and the sharing between the two parties, that is, the method of adopting fixed rules when there is no key or a fixed key is agreed. The specific rules are: the preprocessing method of the secret message S is to convert the text into the corresponding Unicode The method of binary representation of the code; the segmentation rule of the binary string is simply specified as: segment according to the longest number of digits that can be represented by the meta tree; the generation method of the text sequence T used to carry the secret message in the text: sequential selection in the text For the text that appears, if the length of the text is less than the number of segm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com