Implementation method and system for Python source code security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
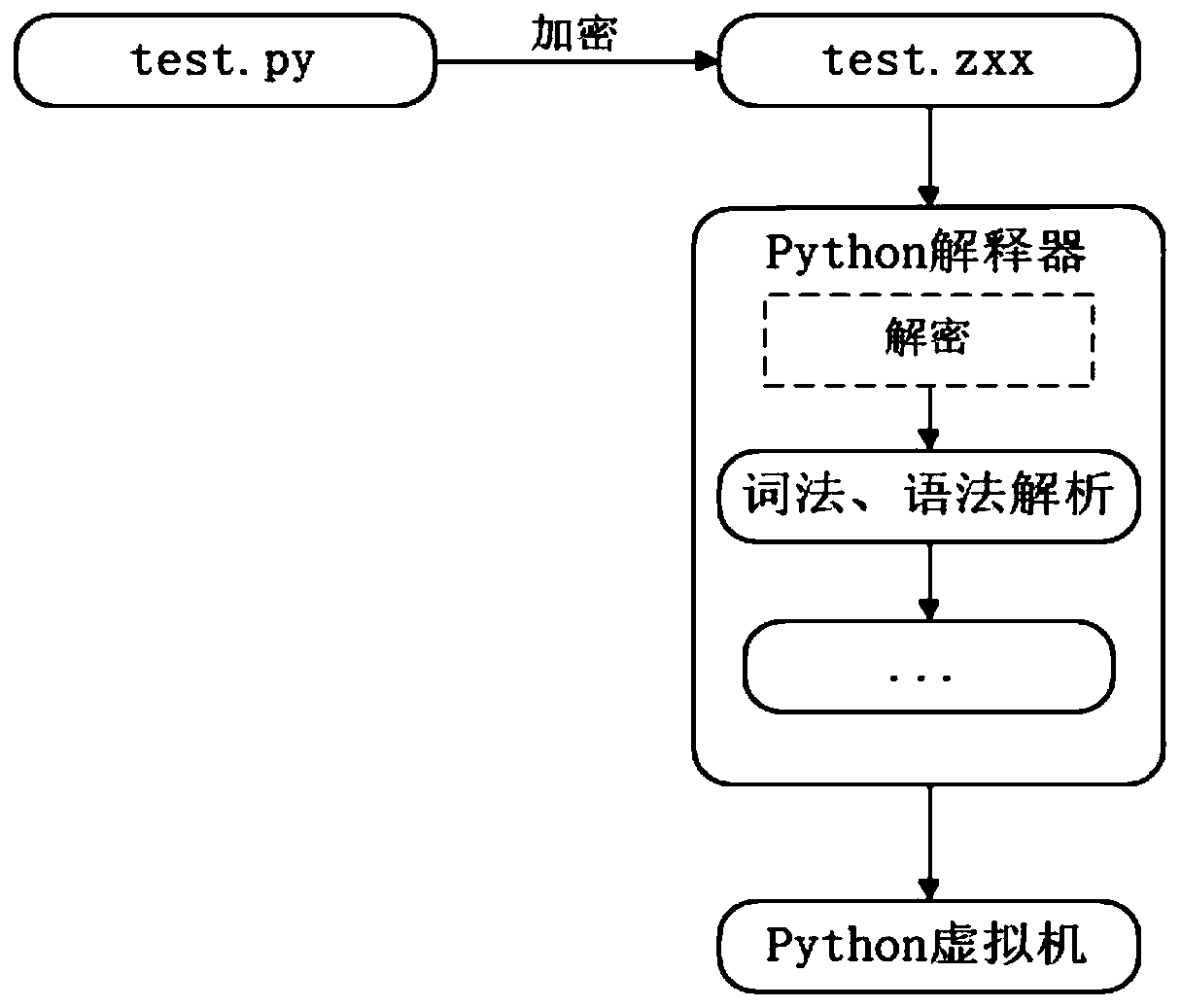
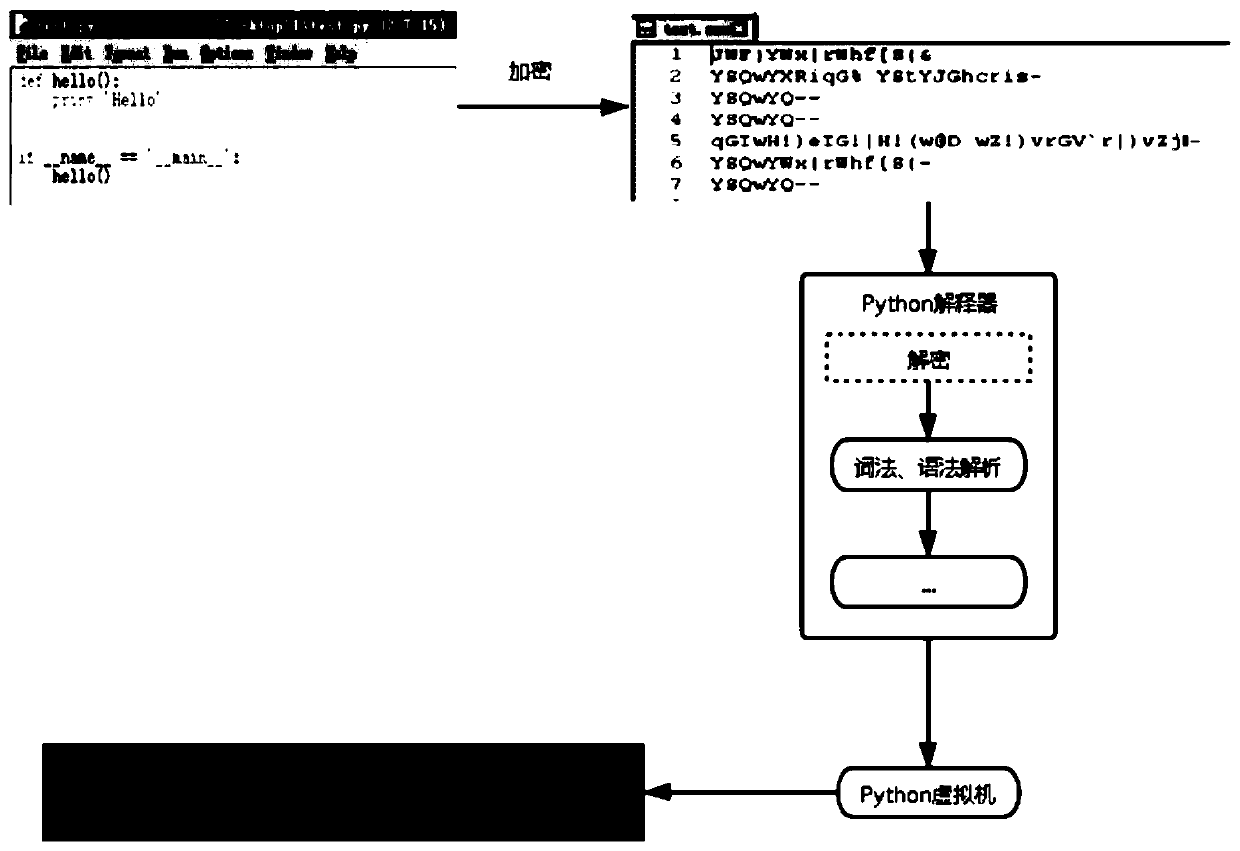
[0036] combine Figure 1-2 As shown, an implementation method of Python source code security protection includes the following steps:
[0037] S01. Encrypt the content of the Python source code file;
[0038] S02. Modify the source code of the Python interpreter to obtain the modified source code of the Python interpreter;
[0039] S03. recompile the modified Python interpreter source code to obtain the Python binary file, and pack and protect the Python binary file to obtain a packed Python interpreter;
[0040] S04. Use the packed Python interpreter to execute the encrypted Python source code program.
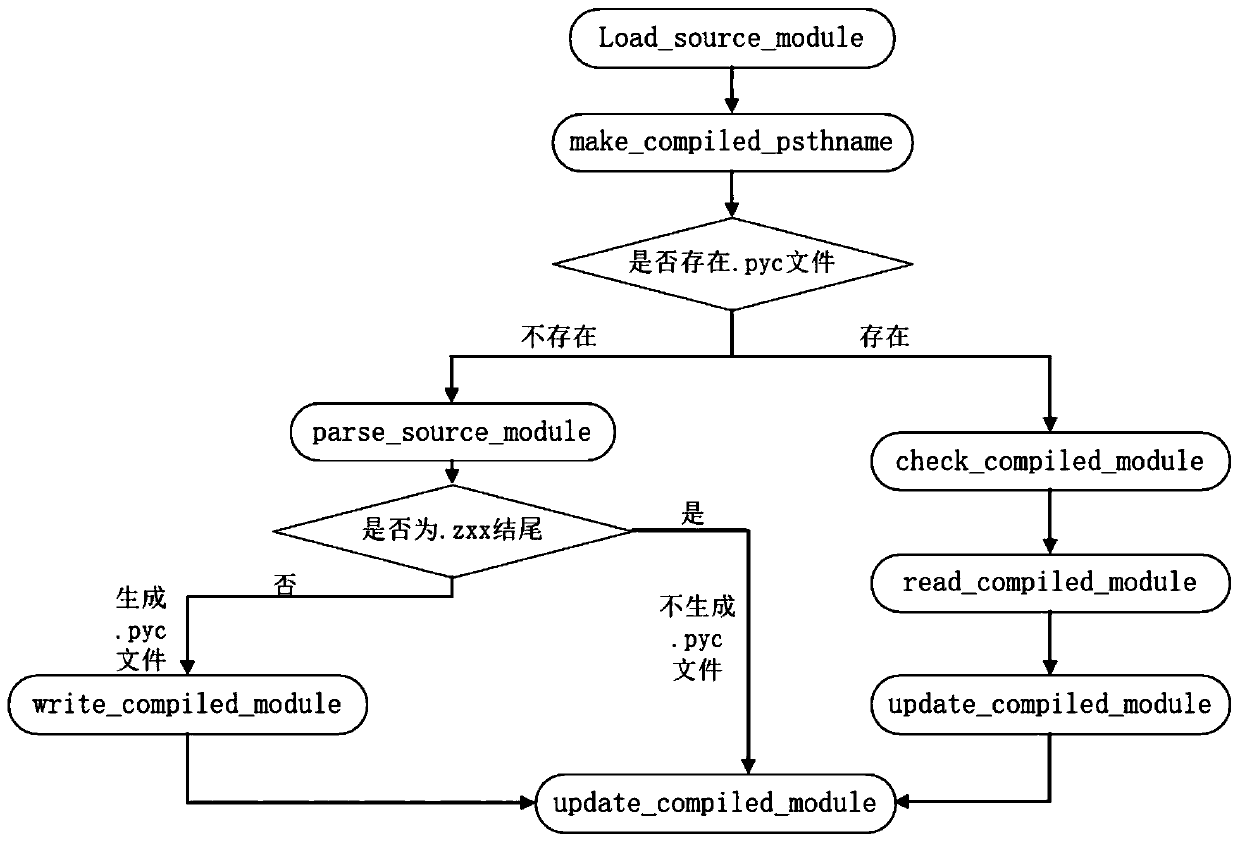
[0041] Further, the specific method of modifying the source code of the Python interpreter in the S02 step is:
[0042] S0211. Add the decryption code to the encrypted .zxx file in the Python interpreter source code;
[0043]S0212. Cancel the generation of the .pyc file in the Python interpreter.
[0044] Further, the encryption method in the step S01 adopts a symmetric ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com