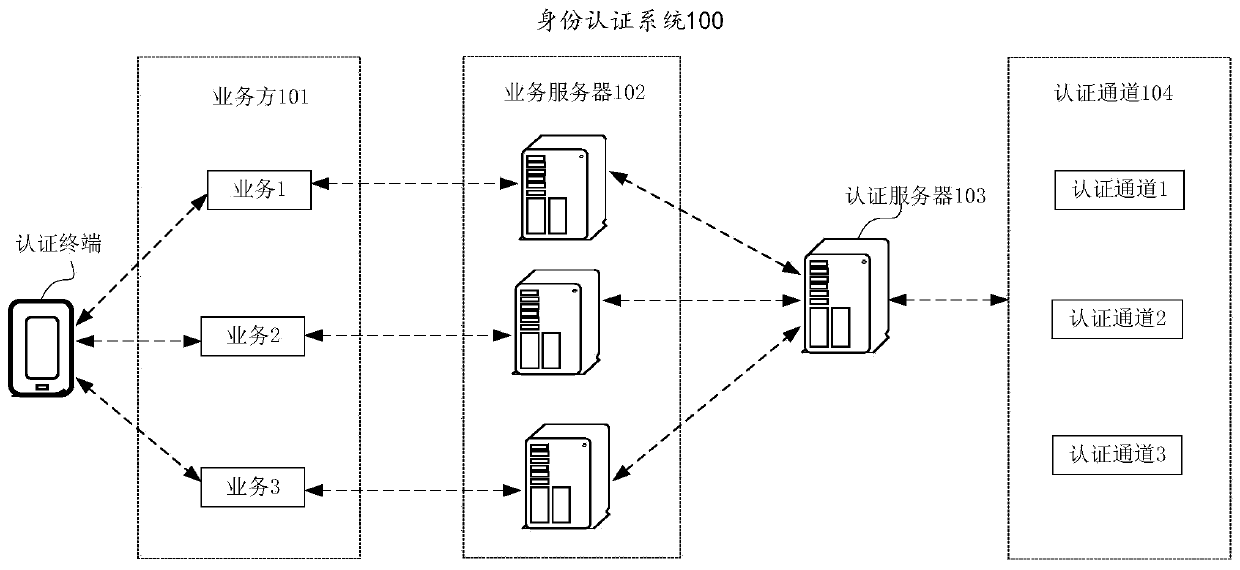
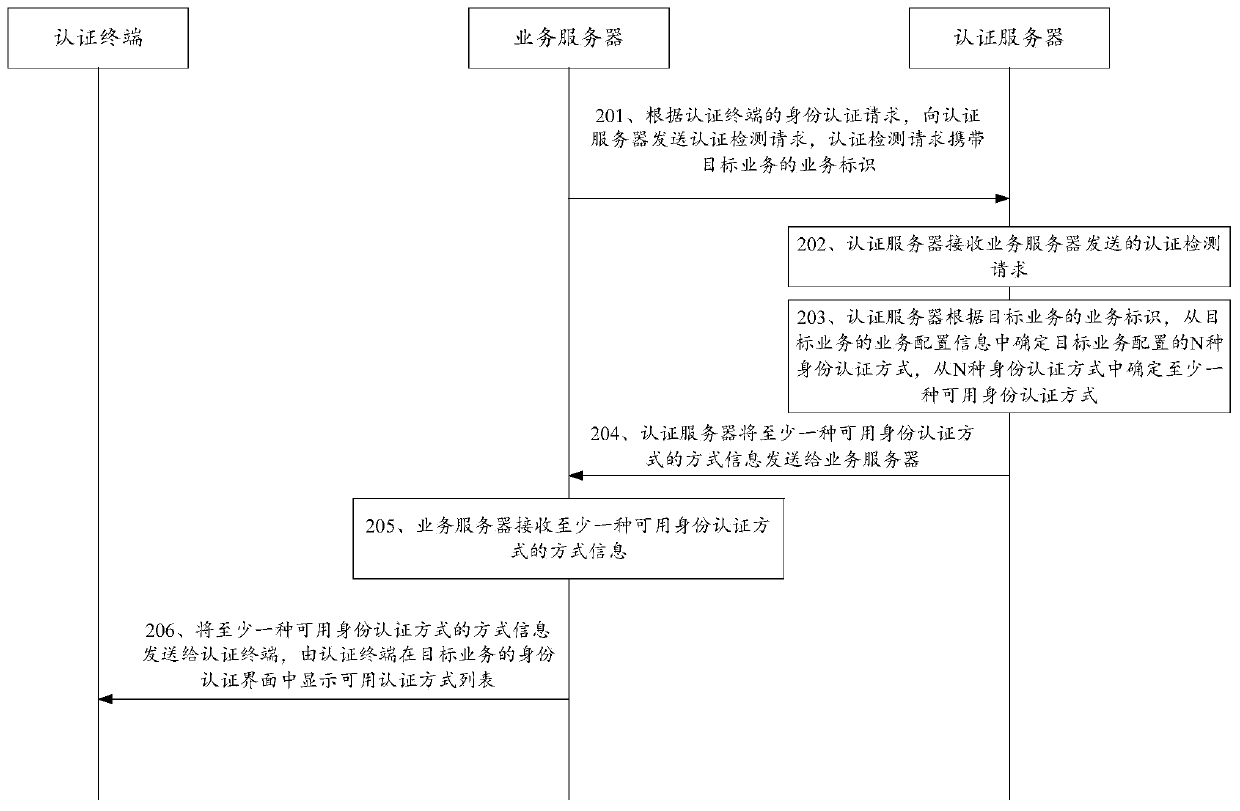
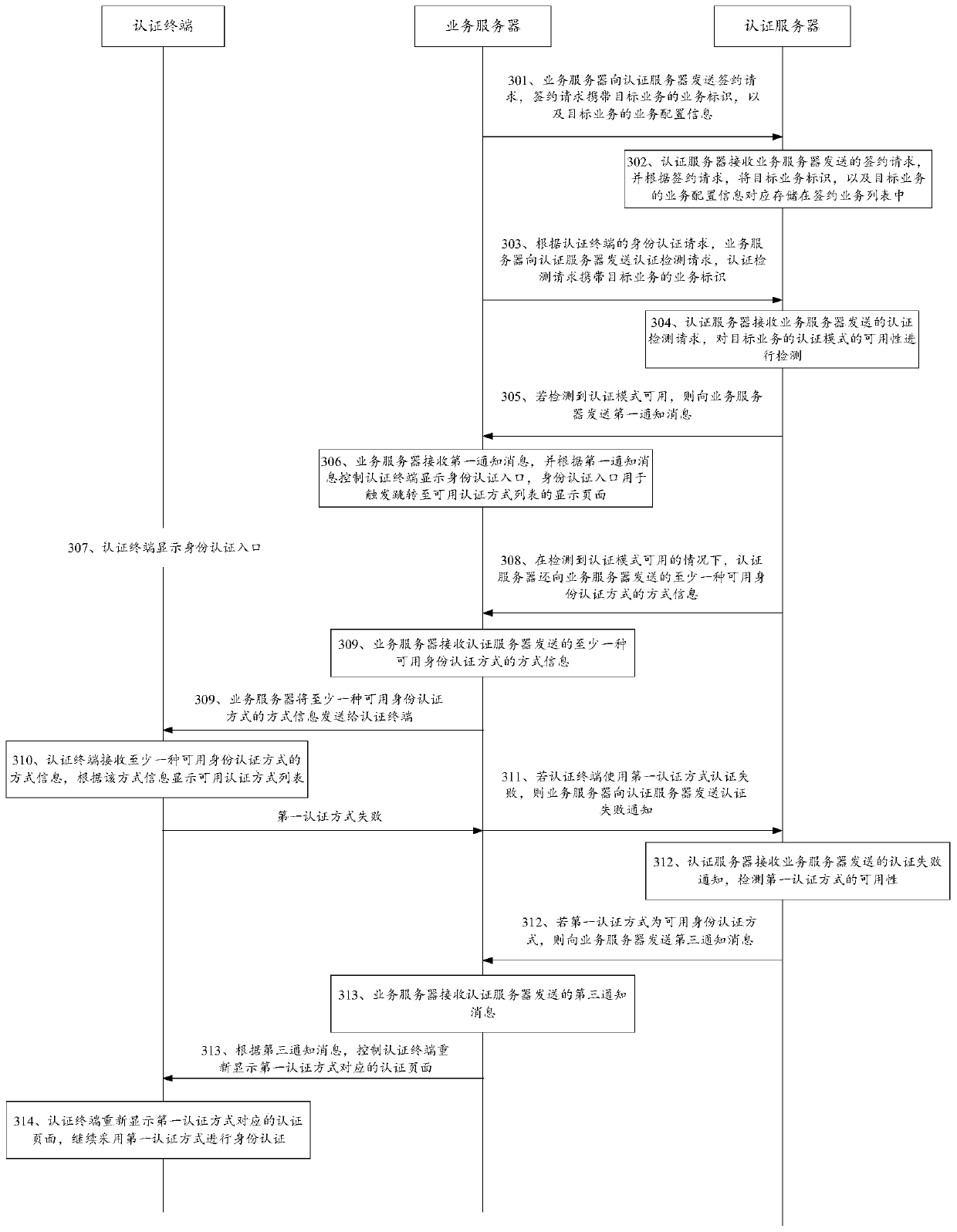
Identity authentication method, system and device and computer storage medium
A technology of identity authentication and authentication methods, which is applied in the field of identity authentication methods, systems, devices, and computer storage media, and can solve the problems of long time-consuming authentication process and heavy processing burden of business servers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0111] In order to make the purpose, technical solution and advantages of the present application clearer, the implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0112] Before explaining the embodiment of the present application in detail, the application scenario of the embodiment of the present application will be described first.
[0113] With the rapid development of the financial industry and the Internet, users tend to conduct financial business-related operations through authentication terminals such as mobile phones. For example, log in to the mobile client for online consumption, or cancel and handle business through online banking. In order to further protect the data security between business parties and users, more and more offline and online businesses gradually require identity authentication. For example, in the process of applying for a bank card online or making online pay...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com