Operation and maintenance auditing system hybrid protocol agent system and method
A mixed protocol and protocol technology, applied in the transmission system, digital transmission system, electrical components, etc., can solve the problem that the protocol cannot be included in the monitoring and management of the operation and maintenance audit system, the operation and maintenance audit system cannot be operated and audited, and the operation and maintenance audit system protocol Unable to proxy and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
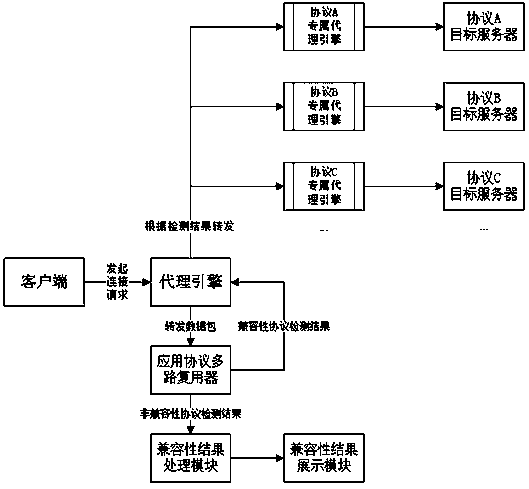
[0038] A hybrid protocol agent method for an operation and maintenance audit system, such as figure 1 , mainly including the following steps in sequence:
[0039] Step S1: The listening program detects that a client initiates a request;
[0040] Step S2: forwarding the detected data to the application protocol multiplexer module for detecting the protocol type;
[0041] Step S3: The proxy engine receives the compatible result matched in the previous detection step, and initiates a connection to the target server.
[0042] Working principle: A mixed protocol proxy method for the operation and maintenance audit system described in this solution directly matches the decoded protocol for the data packets of unknown protocols sent by the client of the operation and maintenance audit system to the back-end virtual host of the operation and maintenance audit system Fields compare individual character protocols or graphics protocols or plaintext protocols.
Embodiment 2
[0044] In the present invention, on the basis of the above-mentioned embodiment 1, the method for detecting the protocol type of the protocol multiplexer is: extracting the first data packet after the three-way handshake, and directly matching the decoded protocol when the number of protocols is small field, confirm the protocol type according to the protocol field and send it to the proxy engine.
[0045] The method for judging the protocol type of the data packet by the application protocol multiplexer is: using a rule detection method: relying on the preset character string or binary sequence in the rule base for comparison and selection, recording the similarity, and recording the similarity in the data When the similarity between the packet and the pre-input protocol meets the threshold requirement, it is determined that the data packet belongs to the protocol.
[0046] When the application protocol multiplexer regularly matches the data packet to an incompatible protocol...
Embodiment 3
[0055] An operation and maintenance audit system hybrid protocol proxy system, such as figure 1 , including client, proxy engine, application protocol multiplexer,
[0056] Client: initiate a connection request to the proxy engine;
[0057] Proxy engine: forward the data packet sent by the client to the application protocol multiplexer, and according to the protocol type of the data packet detected by the application protocol multiplexer, mark the data packet and send it to different The protocol's exclusive proxy engine;
[0058] Application protocol multiplexer: receives the data packet forwarded by the proxy engine, judges the protocol type of the data packet according to the pre-input protocol field, and sends it to the proxy engine according to the detected protocol type.
[0059] Working principle: In the hybrid protocol proxy system of the operation and maintenance audit system described in this solution, for the data packets of unknown protocols sent by the client of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com