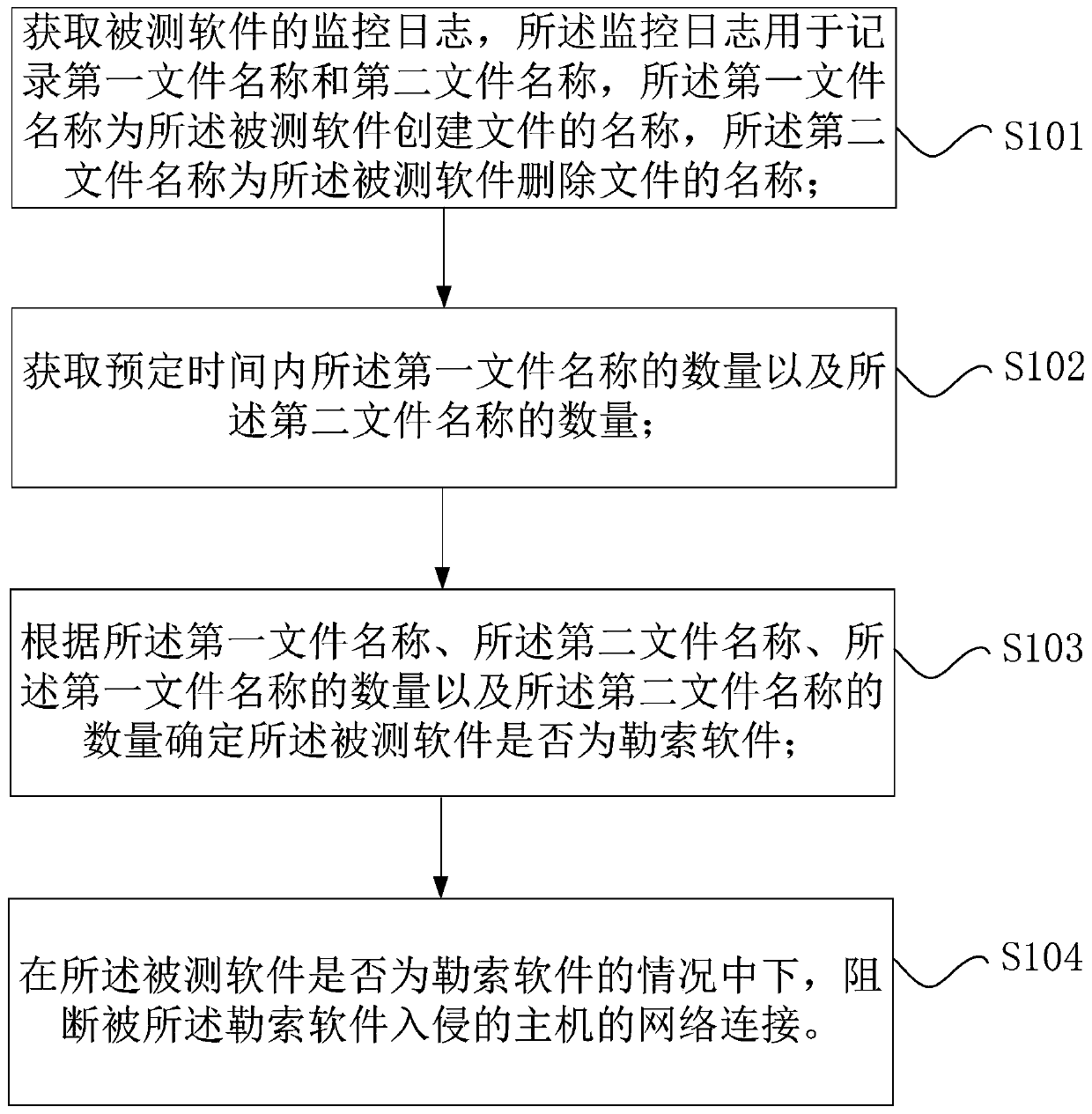
Ransomware defense method and device, storage medium, processor and host
A software and host technology, applied in the field of network security, can solve the problem of high implementation difficulty of ransomware defense methods, and achieve the effects of low implementation difficulty, prevention of proliferation, and simple deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
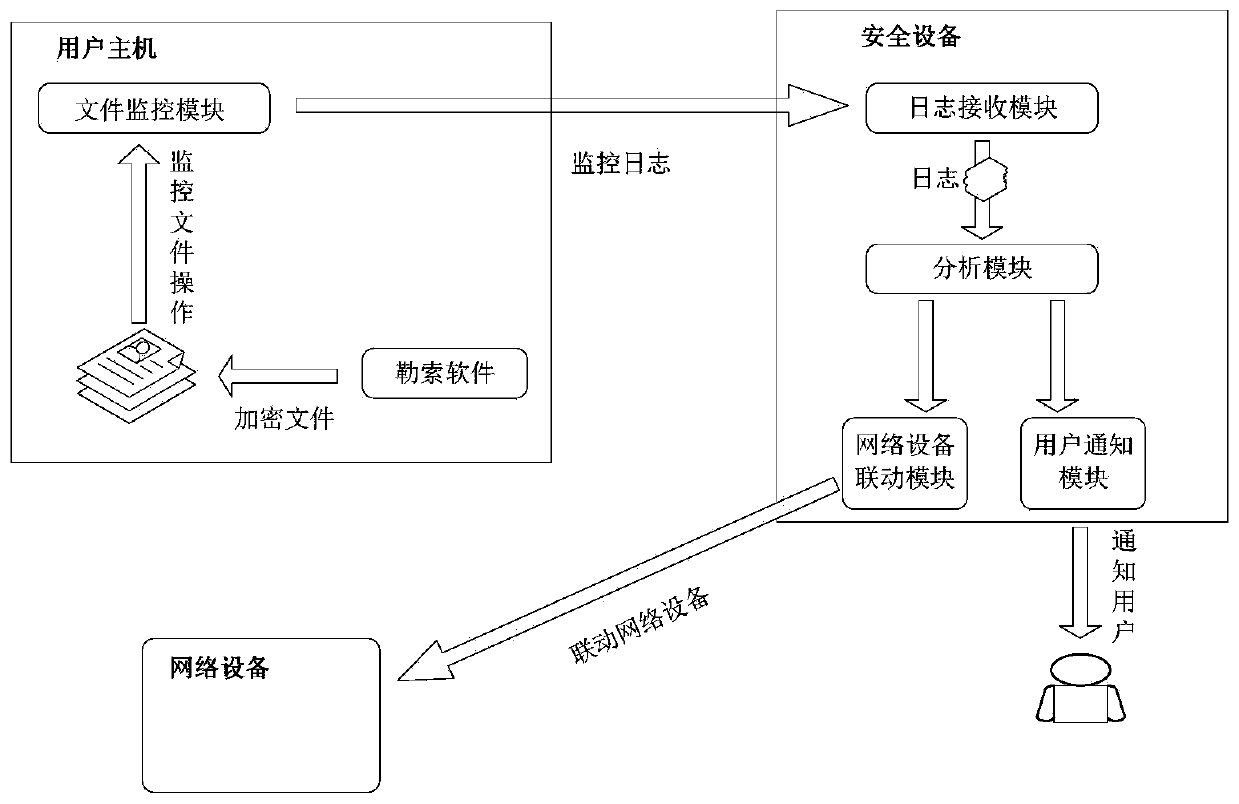
[0070] Such as image 3 As shown, in the application scenario of the ransomware defense method of this embodiment, the user host is connected to the security device through communication, the user host and the security device are respectively connected to the network device, and the security device is a BDS security device, wherein the user host includes file monitoring module and ransomware, the above-mentioned file monitoring module is a sysmon tool, the security device is a BDS security device, and the security device includes a log receiving module, an analysis module, a network device linkage module and a user notification module.
[0071] The steps of the above-mentioned setting to execute the defense method of ransomware are as follows: the user host monitors the file operation behavior of the software under test to generate a monitoring log, and sends the monitoring log to the security device, and the log receiving module of the security device receives the monitoring l...
Embodiment 2
[0073] Such as Figure 4 As shown, in the application scenario of the ransomware defense method of this embodiment, the user host is connected to the security device through communication, the user host and the security device are respectively connected to the network device, and the security device is a BDS security device, wherein the user host includes file monitoring module, ransomware and analysis module, the above-mentioned file monitoring module is a sysmon tool, the security device is a BDS security device, and the security device includes a threat information receiving module, a network device linkage module and a user notification module.
[0074] The steps of the above-mentioned setting to execute the defense method of ransomware are as follows: the user host monitors the file operation behavior of the software under test to generate a monitoring log, and sends the monitoring log to the analysis module, and the analysis module analyzes the file operation behavior of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com