Secret divulgence prevention method, secret divulgence prevention device and encryption device
An anti-leakage and confidential information technology, applied in the blockchain field, can solve the problems of untraceable leakers, low cost of leaking, and leaking of confidential information in announcements, so as to improve security and reliability, ensure security, and reduce leaks risk effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
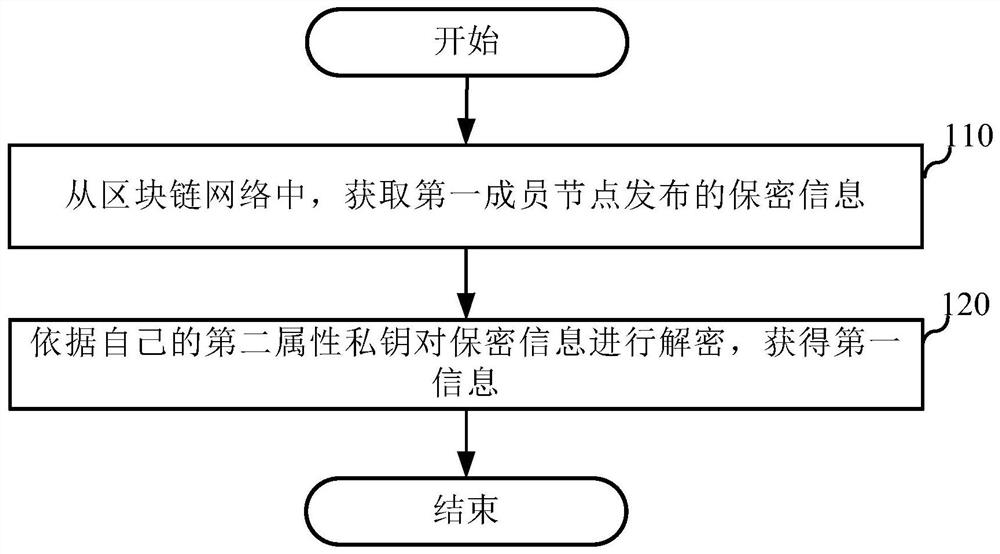
[0032] An embodiment of the present application provides an anti-leakage method, which can be applied to an anti-leakage device, and the device can be placed in the second member node. figure 1 It is a flow chart of the anti-disclosure method in this embodiment, including:
[0033] Step 110, from the blockchain network, obtain the confidential information released by the first member node.
[0034]Among them, the confidential information is the information obtained by the first member node by encrypting the plaintext information according to the attribute public key, and the attribute public key is the secret key generated by the first member node according to the system public key and N attribute characteristics in the attribute set, and the attribute set Including the second attribute feature, N is a positive integer greater than or equal to 1. For example, when N is equal to 3, the attribute set includes the attribute characteristics of three member nodes, all of which hav...
Embodiment 2
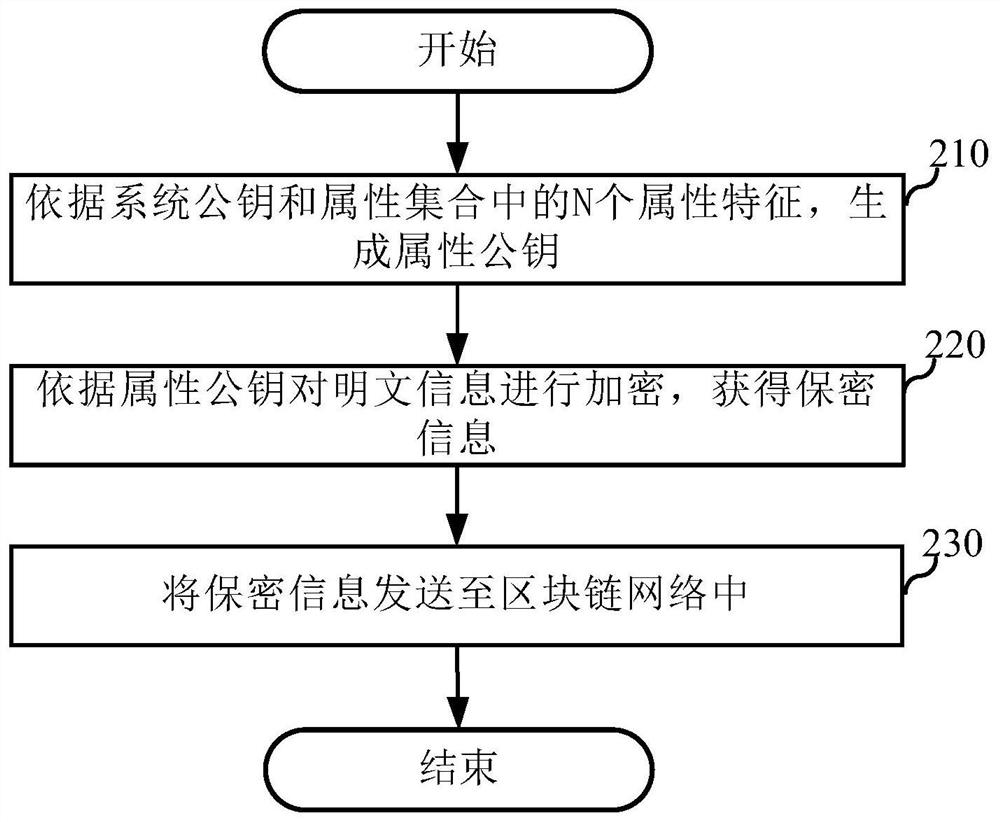
[0051] An embodiment of the present application provides an anti-leakage method, which can be applied to an encryption device in a blockchain network, and the device can be placed in a first member node. figure 2 It is a flow chart of the anti-disclosure method in this embodiment, including:
[0052] Step 210, generate an attribute public key according to the system public key and N attribute characteristics in the attribute set.
[0053] Wherein, the attribute set includes the second attribute feature of the second member node, and N is a positive integer greater than or equal to 1.
[0054] It should be noted that the attribute set can also include the attribute private keys of other multiple member nodes. If the first member node wants multiple member nodes to be able to view the confidential information issued by it, then when generating the attribute public key, just You can put the attribute characteristics of the desired member nodes into the attribute set. For examp...
Embodiment 3
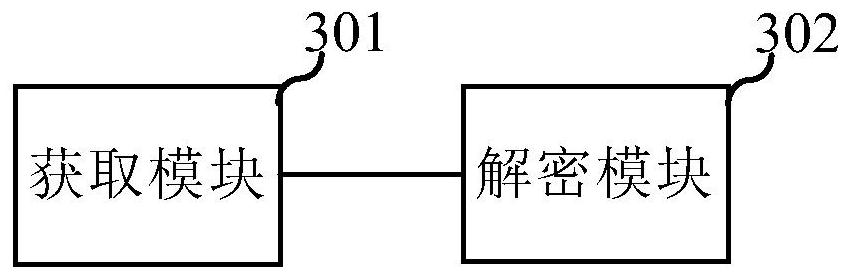
[0063] image 3 It is a schematic structural diagram of an anti-leakage device provided in the embodiment of the present application. For the specific implementation of the device, please refer to the relevant description of Embodiment 1, and the repetition will not be repeated. It is worth noting that the specific implementation of the device in this embodiment is not limited to the above embodiments, and other undescribed embodiments are also within the protection scope of the device.
[0064] Such as image 3 As shown, the anti-leakage device specifically includes: an acquisition module 301 used to acquire the confidential information released by the first member node from the blockchain network, wherein the confidential information is that the first member node encrypts the plaintext information according to the attribute public key The obtained information, the attribute public key is the secret key generated by the first member node according to the system public key an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com