A mobile app permission list automatic verification method and system
A permission and automatic technology, applied in the field of information security, can solve the problems of excessive claims, heavy workload, and low verification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
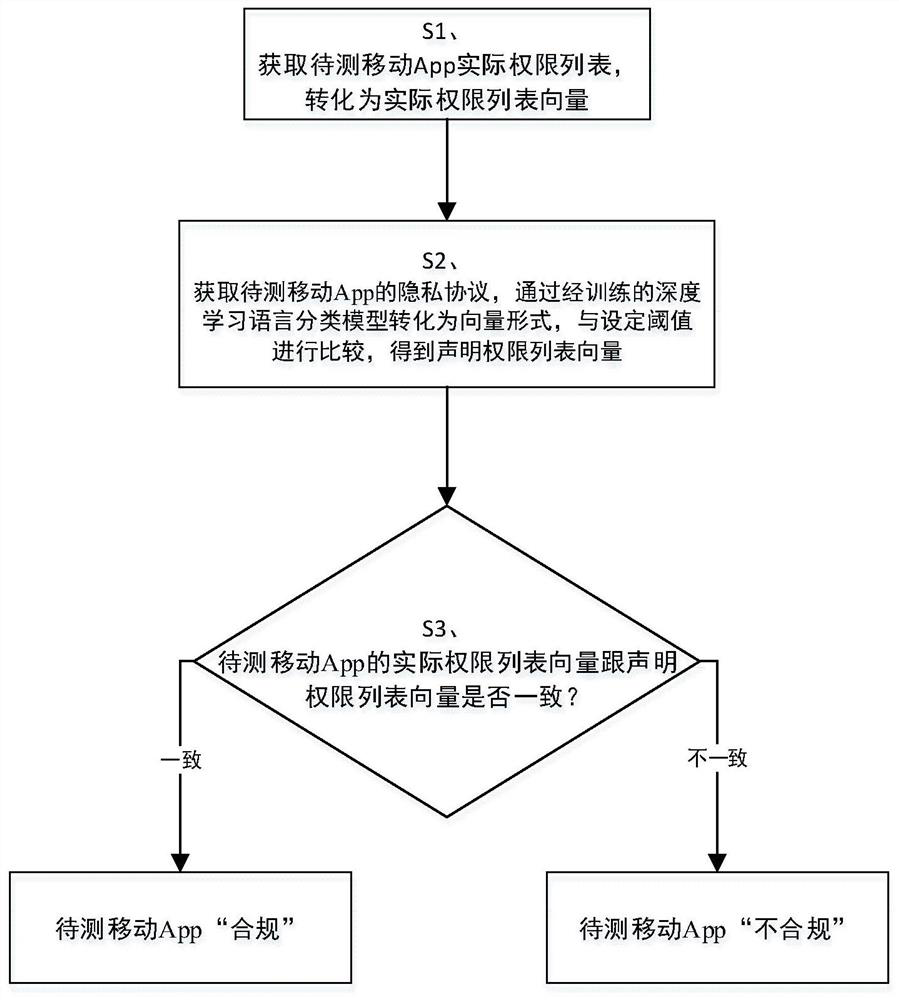
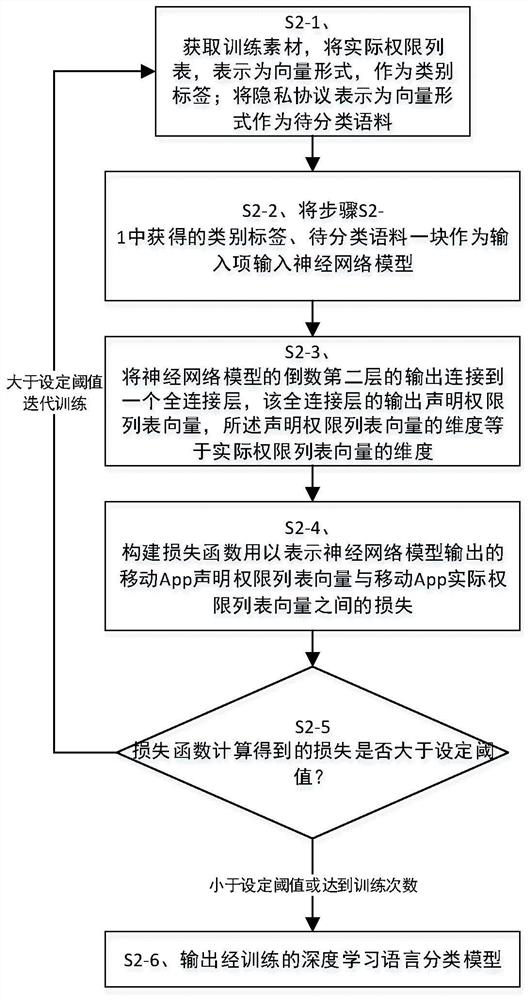
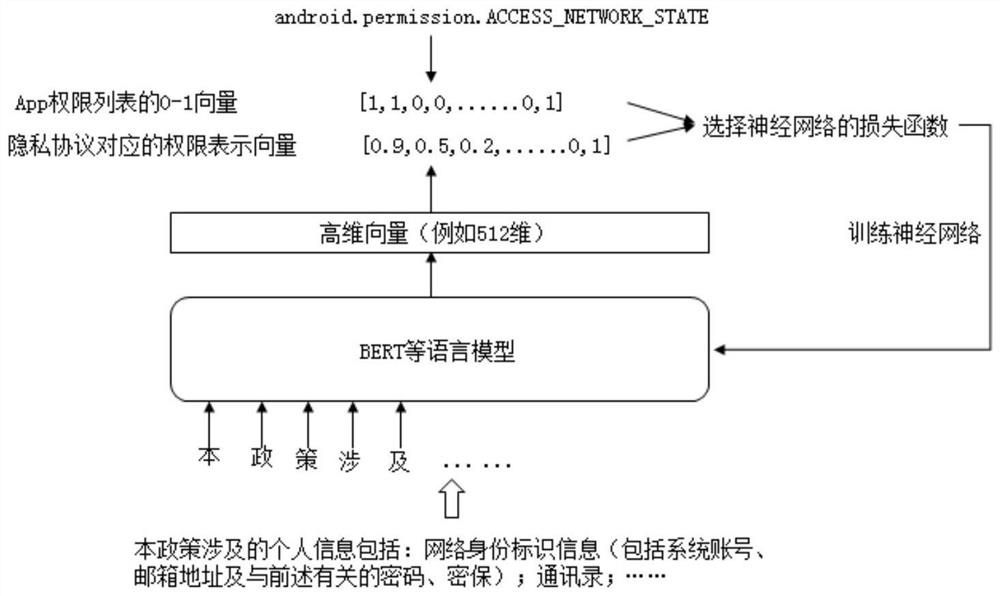
[0049] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
[0050]Android operating system permissions are divided into native Android operating system permissions, such as ACCESS_FILE-LOCATION, READ_CONTACTS, etc., or permissions customized to adapt to more Launchers, such as uses-permission:com.huawei.launcher2.permission.READ_SETTINGS, uses- permission: com.meizu.android.launcher.permission.READ_SETTINGS, etc., and various Android developers customize permissions such as com.tencent.tim.music.data.permission2, com.ss.android.ugc.live.permission for the convenience of use .READ_ACCOUNT etc. At present, 2068 custom permissions and 135 native Android system permissions are counted from the permission list of 10,000 APPs obtained.
[0051] The permission list in the present ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com