Permission authorization method and device based on machine identification code
A machine identification and identification code technology, applied in computer security devices, instruments, program/content distribution protection, etc., can solve problems such as unrealistic implementation, high cost, and complicated login services.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
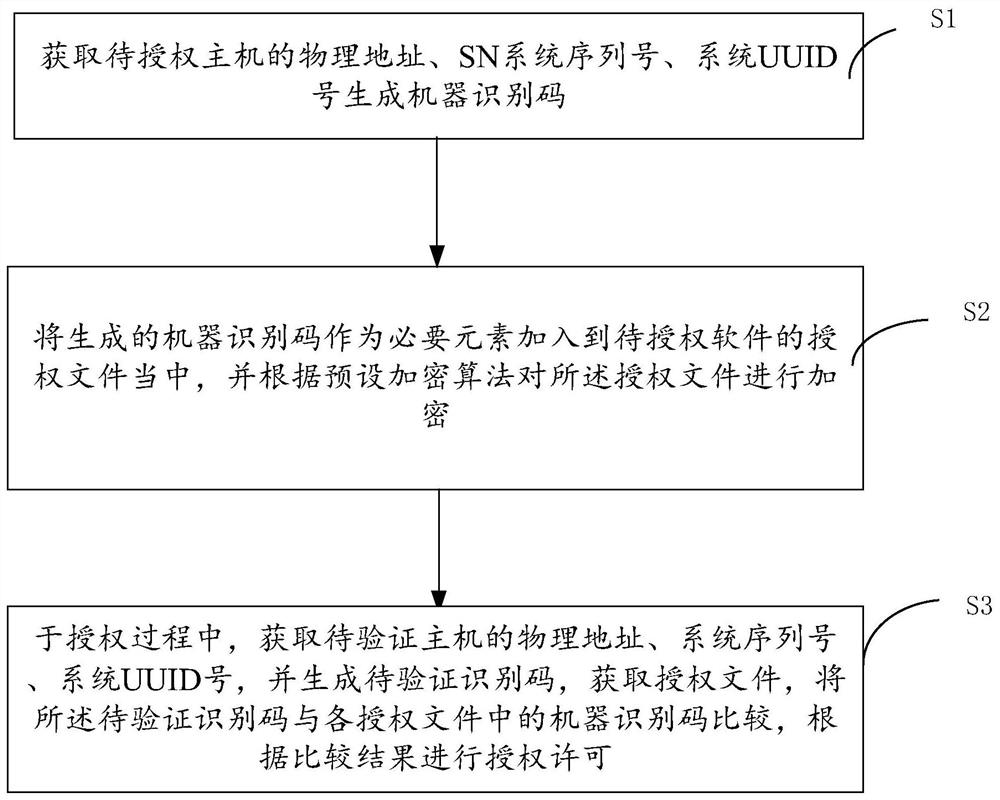
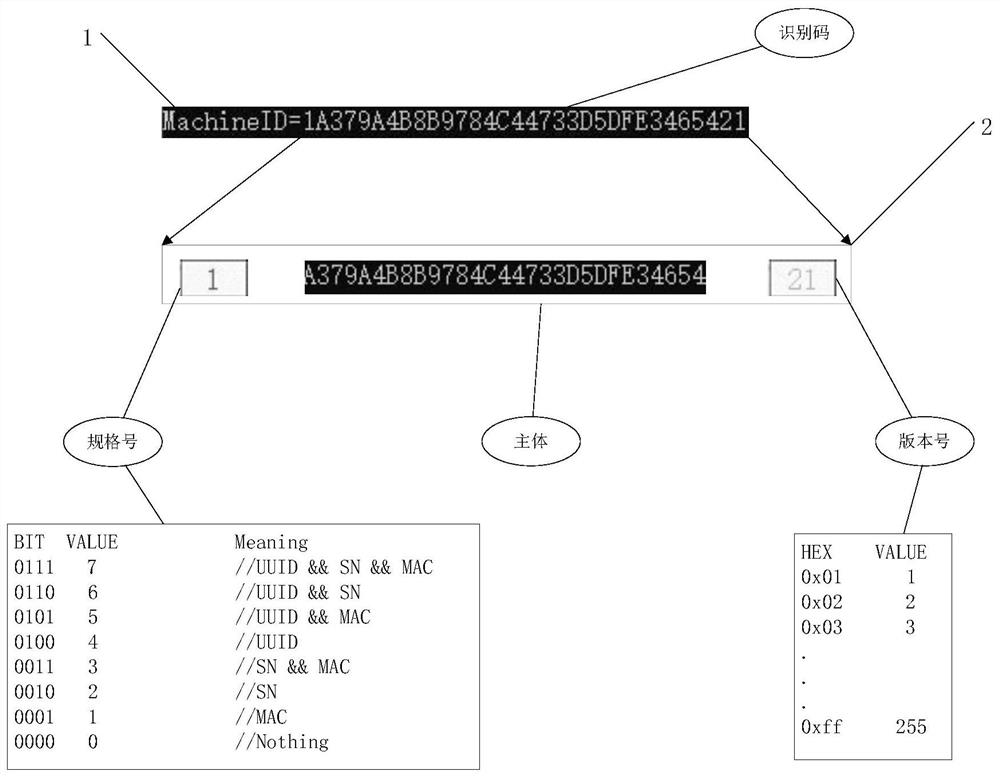
[0065] Figure 4 It is the process of generating the machine identification code in the embodiment of the present invention. Such as Figure 4 As shown, in this embodiment, the generation process of the machine identification code includes the following steps:
[0066] The first step is to obtain the registry of the host to be authorized, and check whether the registry has added MAC address encryption string information. If it exists, obtain the value of the MAC address encryption string information as the MAC address part of the machine identification code. If it does not exist , then reacquire the MAC address of the host to be authorized, encrypt it into a string, and add it to the registry;
[0067] The second step is to obtain the value of the system serial number (the SN number is marked in the figure) of the host computer to be authorized;
[0068] The third step is to obtain the system UUID number of the host to be authorized;
[0069] The fourth step is to concaten...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com