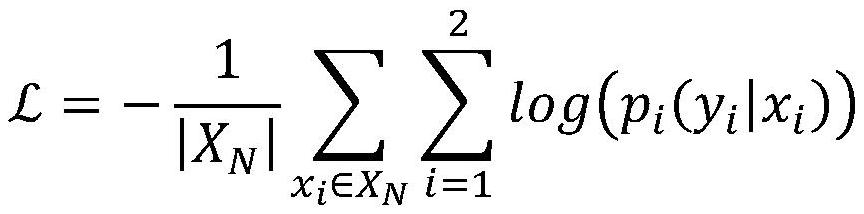Malicious code sample screener and method based on Two-Head exception detection model
Anomaly detection and malicious code technology, applied in the field of information security, can solve the problems of complex structure, unsatisfactory effect, long training process cycle, etc., to achieve the effect of saving time and strong universality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
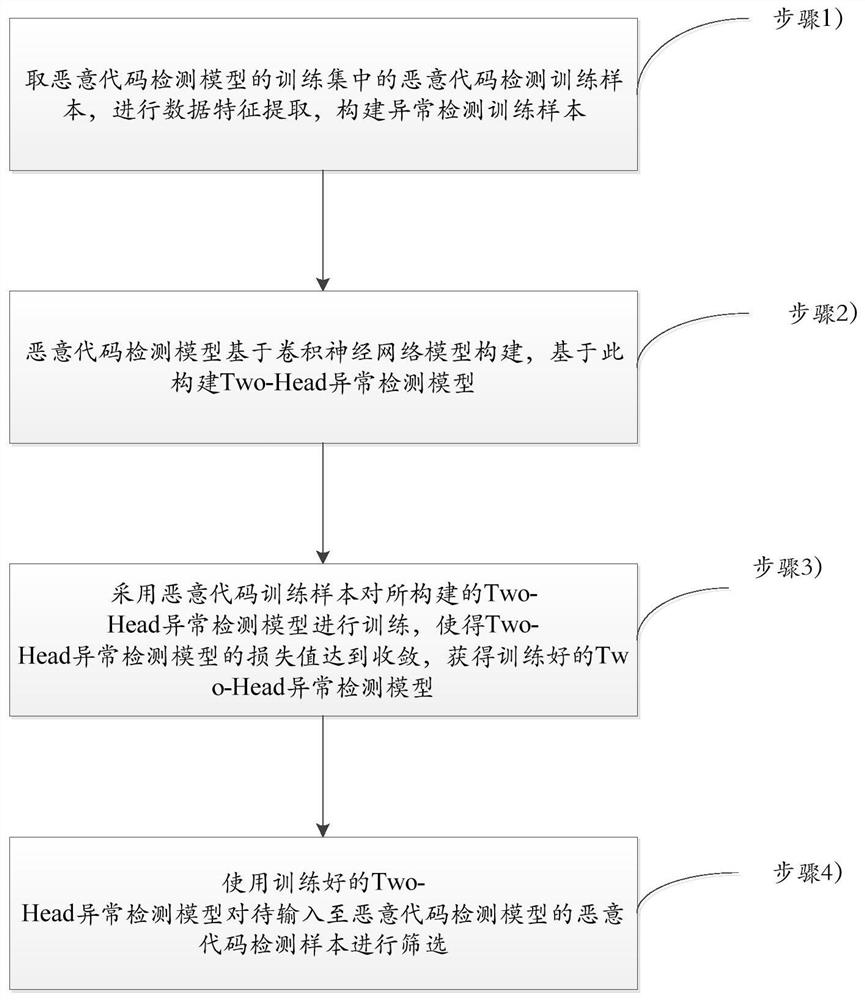
[0050] The present invention will be described in detail below with reference to the accompanying drawings and examples.
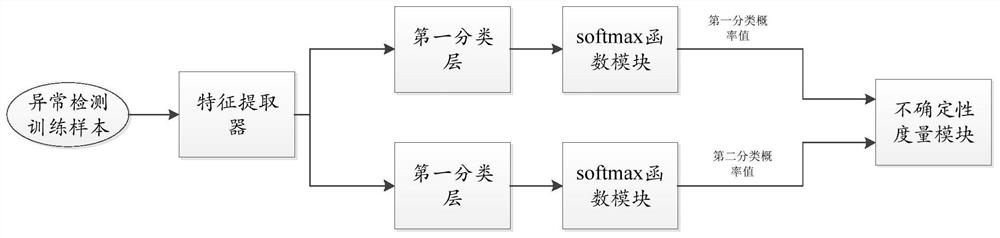
[0051] Aiming at the time robustness problem of the malicious code detection model, the present invention proposes a malicious code sample selection method based on the Two-Head anomaly detection model. The basic idea of the sample selection method is to design an abnormal sample detection model to filter out the abnormal samples in the test data before the malicious code detection model starts to predict, and let the model predict the remaining normal samples. Manual labeling is used to perform active learning, thereby improving the prediction reliability of the model, reducing the cost of manual analysis, and updating the malicious code detection model in a continuous and incremental manner.
[0052] An embodiment of the present invention provides a malicious code sample filter based on the Two-Head anomaly detection model, which is used for sample scr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com