Access request shunting method and related equipment
An access request and request-end technology, applied in the computer field, can solve problems such as response timeout, no response, and reduced stability of the system to be accessed, and achieve the effect of improving stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
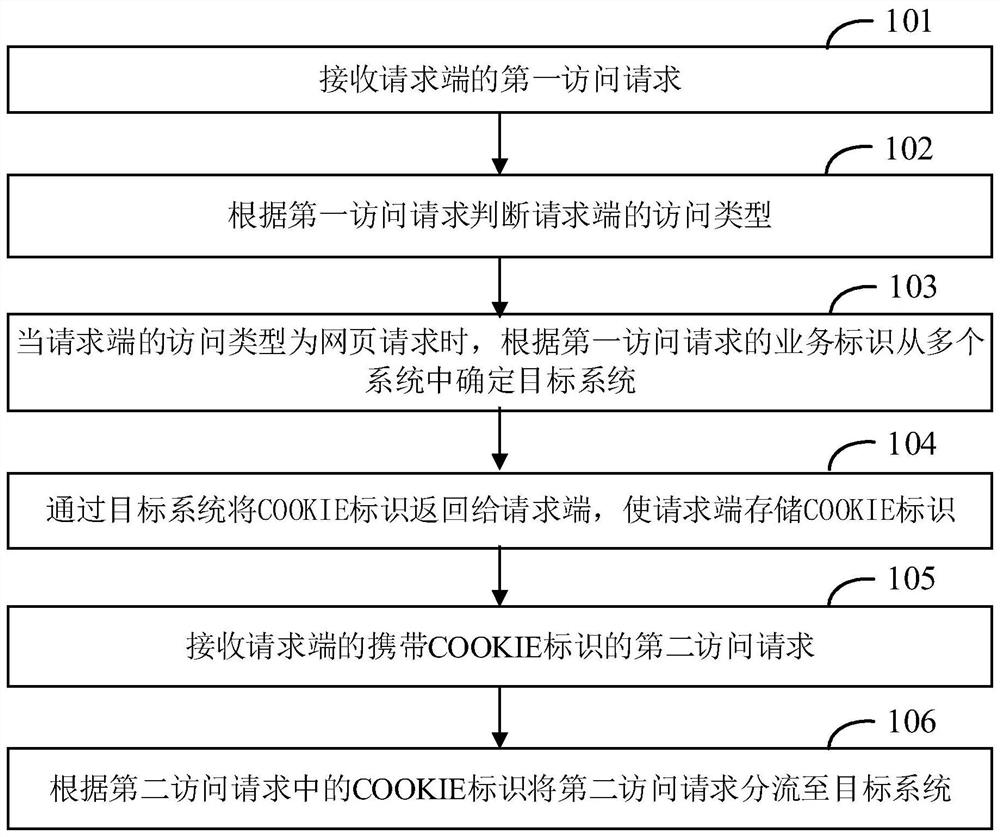
[0050] figure 1 It is a flow chart of the access request distribution method provided by Embodiment 1 of the present invention. The method for distributing access requests is applied to computer equipment, and is used for distributing access requests, balancing the access pressure of the systems to be accessed including multiple systems, and improving the stability of the systems to be accessed.
[0051] like figure 1 As shown, the access request distribution method includes:
[0052] 101. Receive a first access request from a requesting end.
[0053] The requesting end may include a mobile terminal or a PC terminal. The first access request of the mobile terminal may be received, or the first access request of the PC terminal may be received.
[0054] The first access request may include a type identifier, a service identifier, description information of the target data to be requested, and the like.
[0055]In a specific embodiment, when the requesting end needs multipl...
Embodiment 2
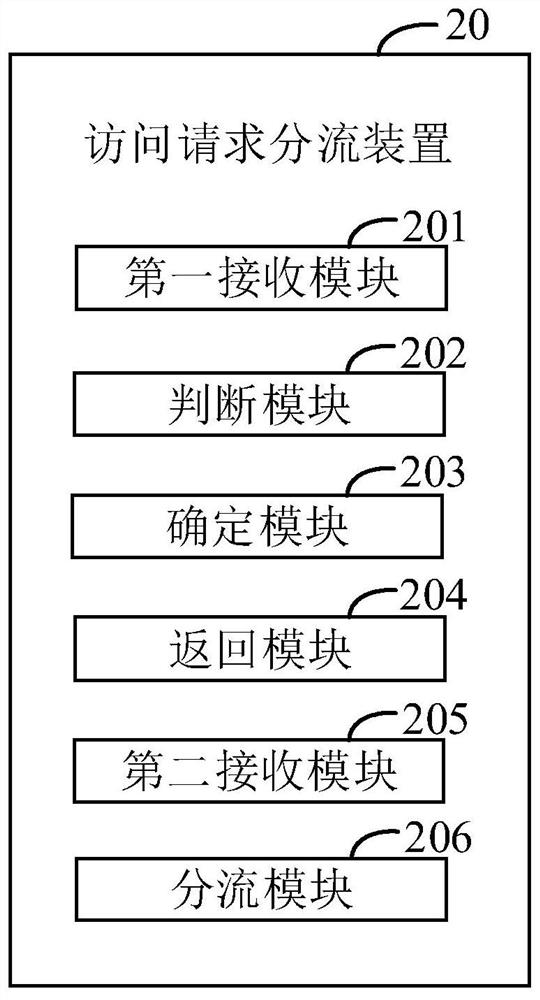
[0092] figure 2 It is a structural diagram of an access request distribution device provided in Embodiment 2 of the present invention. The access request distribution apparatus 20 is applied to computer equipment. The access request distribution device 20 is used to classify the objects to be supervised according to the indicators, so as to improve the accuracy of the classification results.
[0093] like figure 2 As shown, the device 20 for splitting access requests may include a first receiving module 201 , a judging module 202 , a determining module 203 , a returning module 204 , a second receiving module 205 , and a splitting module 206 .
[0094] The first receiving module 201 is configured to receive a first access request from a requesting end.
[0095] The requesting end may include a mobile terminal or a PC terminal. The first access request of the mobile terminal may be received, or the first access request of the PC terminal may be received.
[0096] The firs...
Embodiment 3
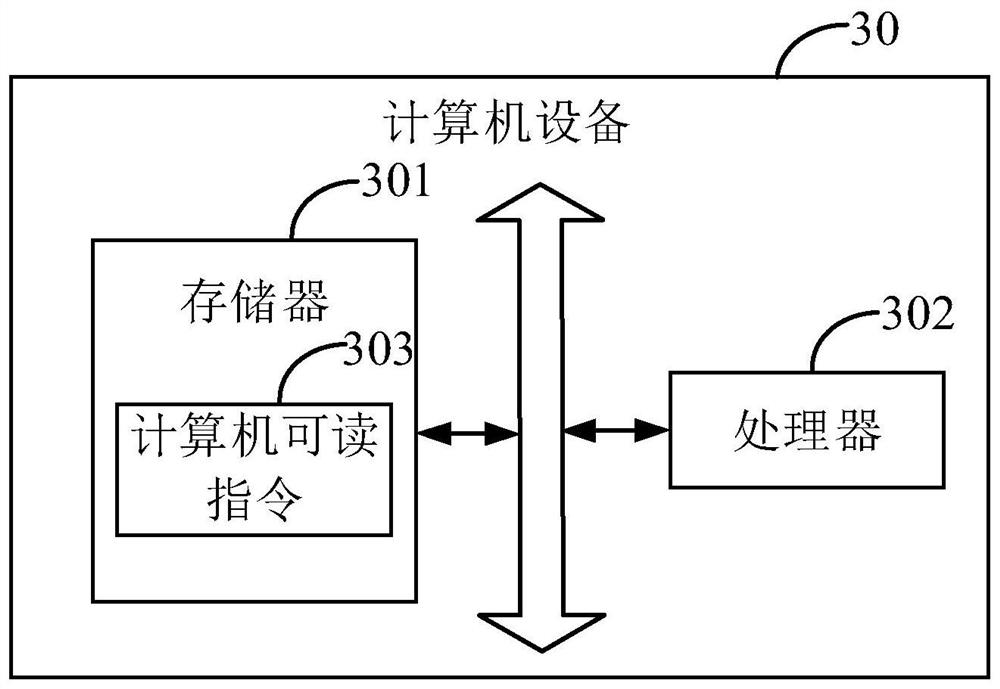
[0131] This embodiment provides a computer-readable storage medium, where computer-readable instructions are stored on the computer-readable storage medium, and when the computer-readable instructions are executed by a processor, the steps in the above embodiments of the access request distribution method are implemented, for example figure 1 Steps 101-106 shown:
[0132] 101. Receive a first access request from a requesting end;
[0133] 102. Determine the access type of the requesting end according to the first access request;
[0134] 103. When the access type of the requesting end is a webpage request, determine a target system from multiple systems according to the service identifier of the first access request;
[0135] 104. Return the COOKIE identifier to the requesting end through the target system, so that the requesting end stores the COOKIE identifier;
[0136] 105. Receive a second access request carrying the COOKIE identifier from the requesting end;
[0137] 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com