An attack chain intelligence analysis method, system and storage medium
An analysis method and intelligence technology, applied in the field of network security, can solve problems such as inability to produce synergistic effects, and achieve the effect of convenient dynamic deployment and convenient defense strategies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so as to define the protection scope of the present invention more clearly.
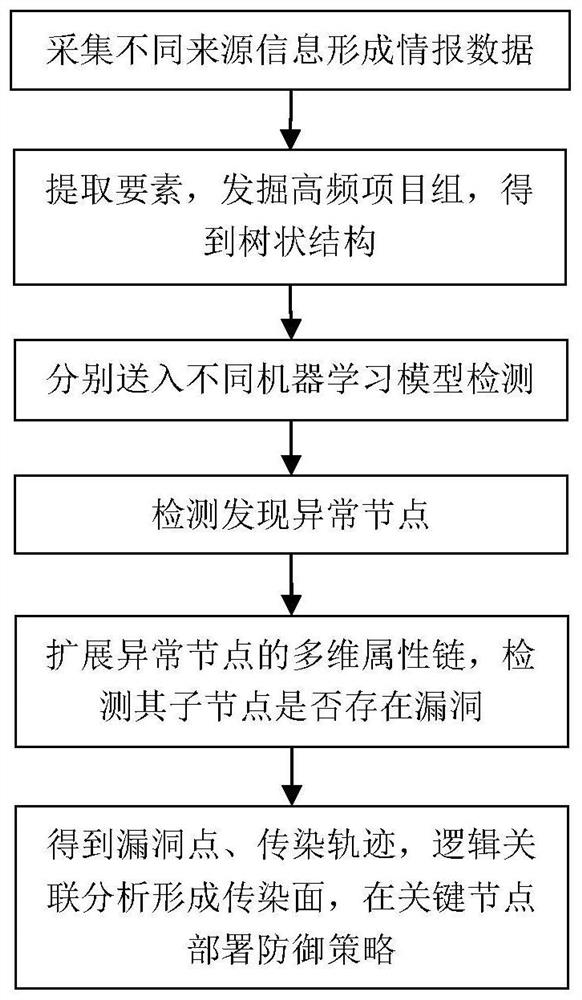
[0036] figure 1 A general flow chart of the attack chain intelligence analysis method provided by this application, the method includes:
[0037] The data collector collects the mirrored traffic of the switch, network traffic logs, security device logs, and raw data of transmitted files, and receives vulnerability information, virus database information, and intelligence data of network attack behavior characteristics from multiple different data sources. Raw data and intelligence data are cached;
[0038] Collect the operating status data, IP data, domain name information, URL information, transmission data packets, and database dynamic informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com