Network abnormal flow detection method, device and equipment
A network abnormality and traffic detection technology, applied in the field of network security, can solve the problems of inability to efficiently and accurately analyze and process abnormal traffic, and high capacity limitations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
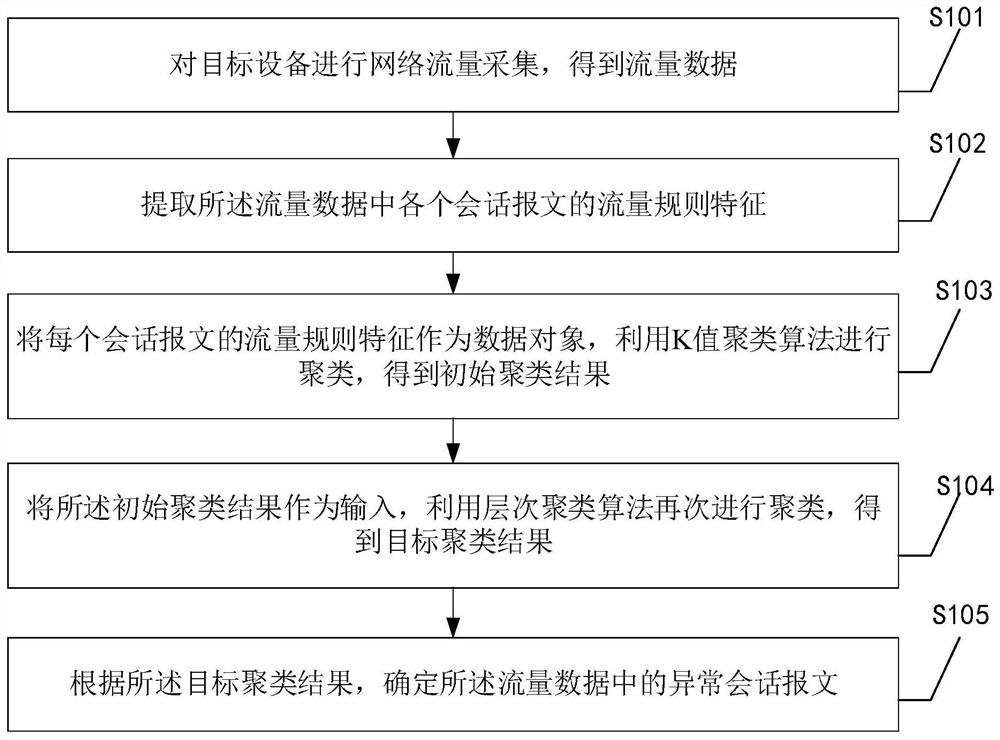
[0057] The following introduces Embodiment 1 of a method for detecting abnormal network traffic provided by the present application, see figure 1 , embodiment one includes:
[0058] S101. Collect network traffic of the target device to obtain traffic data;
[0059] S102. Extract traffic rule features of each session packet in the traffic data;
[0060] S103. Using the traffic rule feature of each session packet as a data object, perform clustering using a K-value clustering algorithm to obtain an initial clustering result;
[0061] S104. Using the initial clustering result as an input, perform clustering again using a hierarchical clustering algorithm to obtain a target clustering result;
[0062] S105. Determine abnormal session packets in the traffic data according to the target clustering result.
[0063] Specifically, this embodiment can run at the exit where the subnet is connected to the backbone network, and access the switching device at the border in a bypass mode....
Embodiment 2
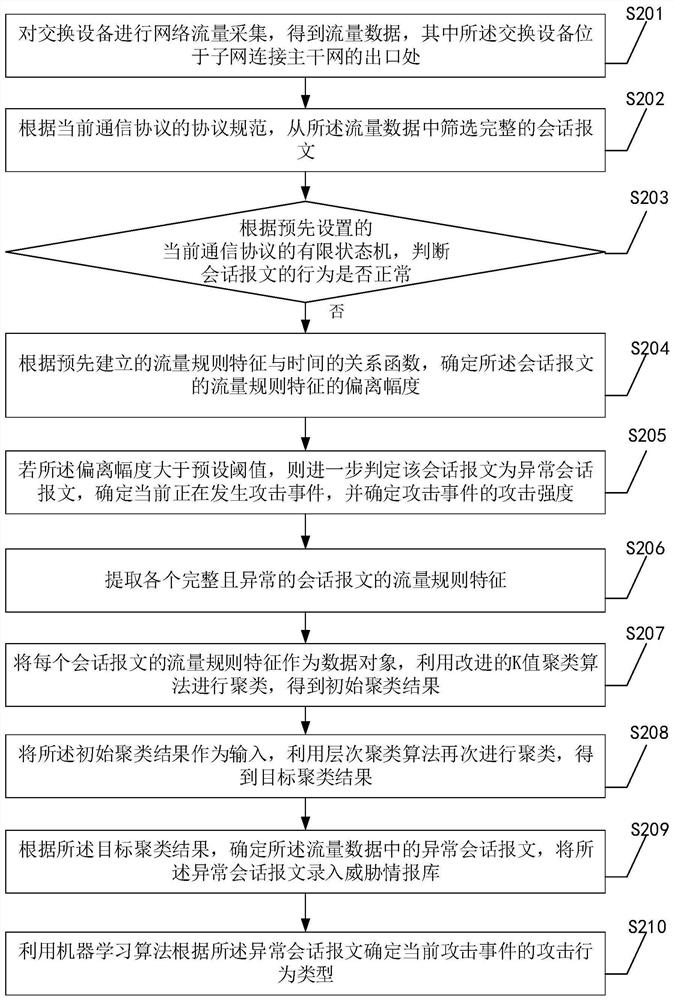
[0075] see figure 2 , embodiment two specifically includes:
[0076] S201. Collect network traffic from the switching device to obtain traffic data, wherein the switching device is located at an exit where the subnet is connected to the backbone network;
[0077] S202. According to the protocol specification of the current communication protocol, filter the complete session message from the traffic data;
[0078] S203. For each complete session message, judge whether the behavior of the session message is normal according to the preset finite state machine of the current communication protocol, wherein the finite state machine is used to describe a normal session under the current communication protocol Behavior and / or abnormal session behavior; if normal, then release; if not normal, then enter S204;
[0079] S204. Determine the deviation range of the traffic rule feature of the session packet according to the pre-established relationship function between the traffic rule ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com