Lightweight security authentication method based on XOR-APUF
A technology of XOR-APUF and security authentication, which is applied in the field of lightweight security authentication methods, can solve problems such as breaching and consuming hardware circuit resources, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
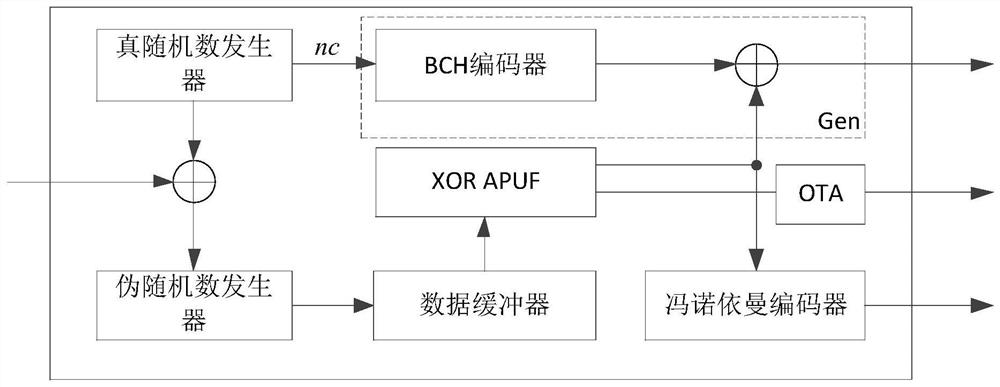
[0036] The present invention designs a lightweight security authentication method based on the unclonable function XOR-APUF of the XOR gate arbitrator, the content of the method includes the registration stage and the authentication stage, and the protocol entities include tokens and servers,
[0037] The registration phase has the following steps:
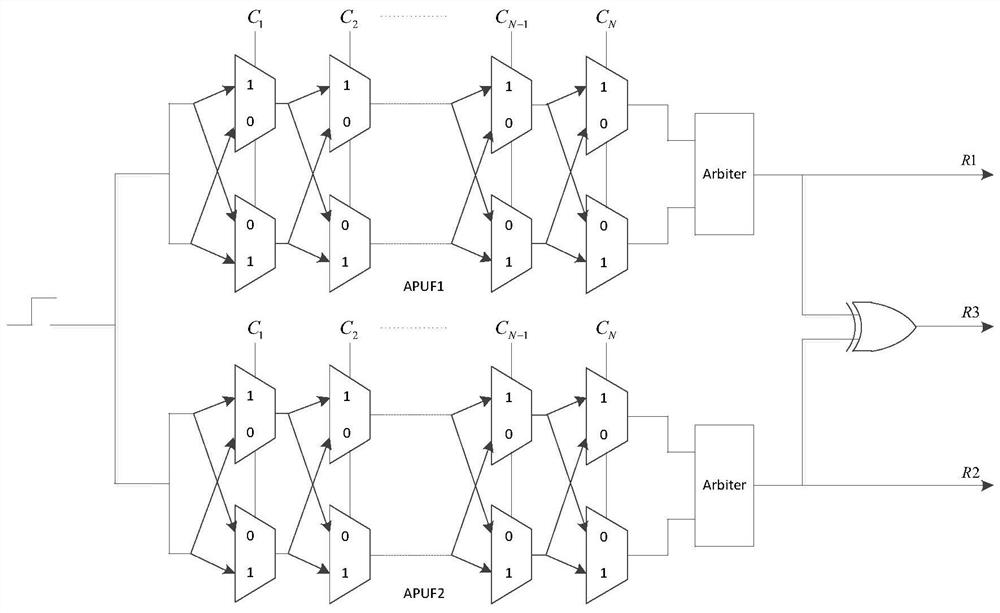
[0038] Step 1: The server uses TRNG to generate a true random number as an ID and sends it to the token storage with XOR-APUF;
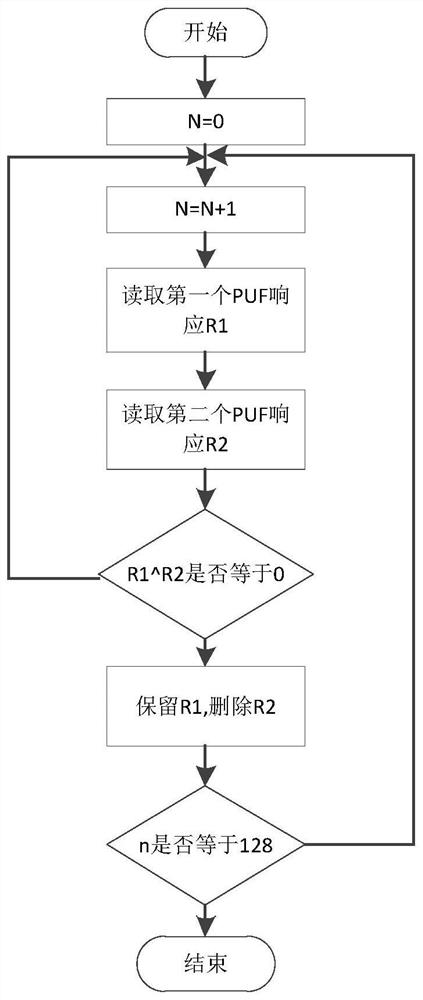
[0039] Step 2: The server side uses TRNG to generate a certain amount of incentives and send them to the token with XOR-APUF, and the token will input the incentives into XOR-APUF, and send the response corresponding to each incentive back to the server;
[0040] Step 3: The server uses CRPs to train the model of the evolutionary strategy algorithm, and finally obtains the XOR-APUF simulated by the software.
[0041] The authentication phase has the following steps:
[0042] Step 1: After the server re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com