Password unit creation method and device, data processing method and device and electronic equipment
A cryptographic device and data processing technology, which is applied in the field of computer cryptography, can solve problems such as slowing down the startup speed, affecting the startup speed of cryptographic devices, and increasing the attack surface
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
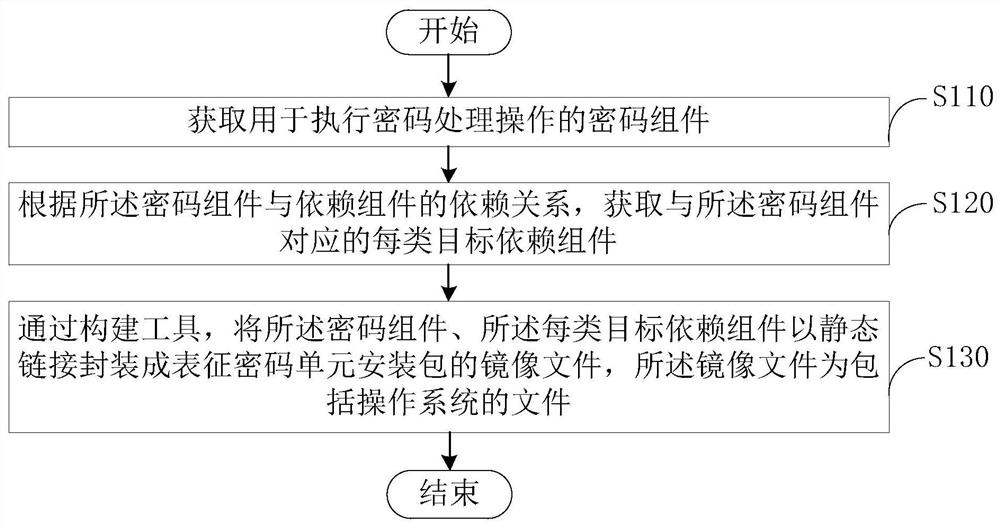
[0047] Please refer to image 3 , the embodiment of the present application also provides a cryptographic unit creation method, which can be applied to the above-mentioned development terminal 10, and each step of the method is executed or implemented by the development terminal 10, and the method may include the following steps:
[0048] Step S110, acquiring a cryptographic component for performing cryptographic processing operations;
[0049] Step S120, according to the dependency relationship between the cryptographic component and the dependent component, obtain each type of target dependent component corresponding to the cryptographic component;
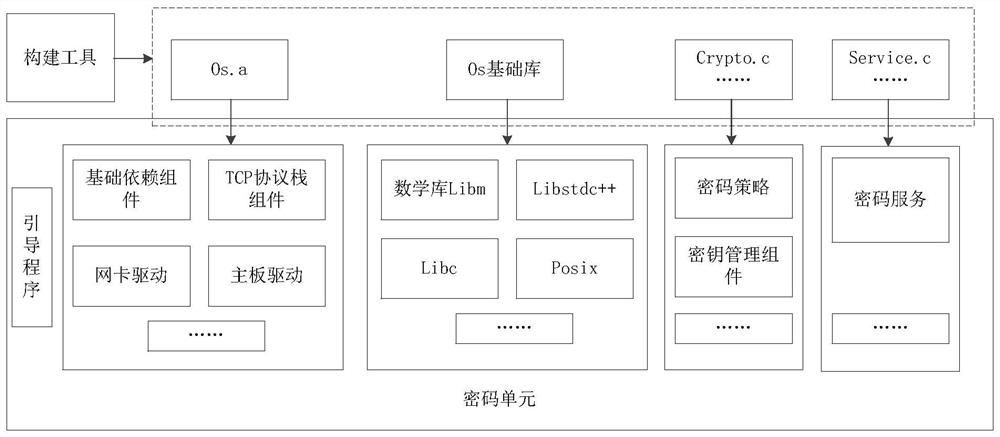
[0050] In step S130, the cryptographic component and each type of target dependent component are statically linked and packaged into an image file representing the installation package of the cryptographic unit through the construction tool, and the image file is a file including an operating system.
[0051] In the above embod...
no. 2 example
[0095] Please refer to Figure 5 , the embodiment of the present application also provides a data processing method, which can be applied to the encryption device 20 described above. The cryptographic device 20 stores the image file created through the first embodiment, and the cryptographic device 20 can execute or implement various steps of the method. Wherein, the method may include the following steps:
[0096] Step 310, acquiring a cryptographic processing request and data to be processed corresponding to the cryptographic processing request;
[0097] Step 320: According to the cryptographic operation policy corresponding to the cryptographic processing request, execute the image file to perform cryptographic operation on the data to be processed, and obtain the data to be processed after cryptographic operation.
[0098] In the second embodiment, the cryptographic operation strategy may be, but not limited to, the above-mentioned digital signature, character encryption...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com