Malicious software detection method and device
A technology of malware and detection methods, applied in neural learning methods, computer security devices, computer parts, etc., can solve problems such as terminal hazards and security risks, and achieve the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
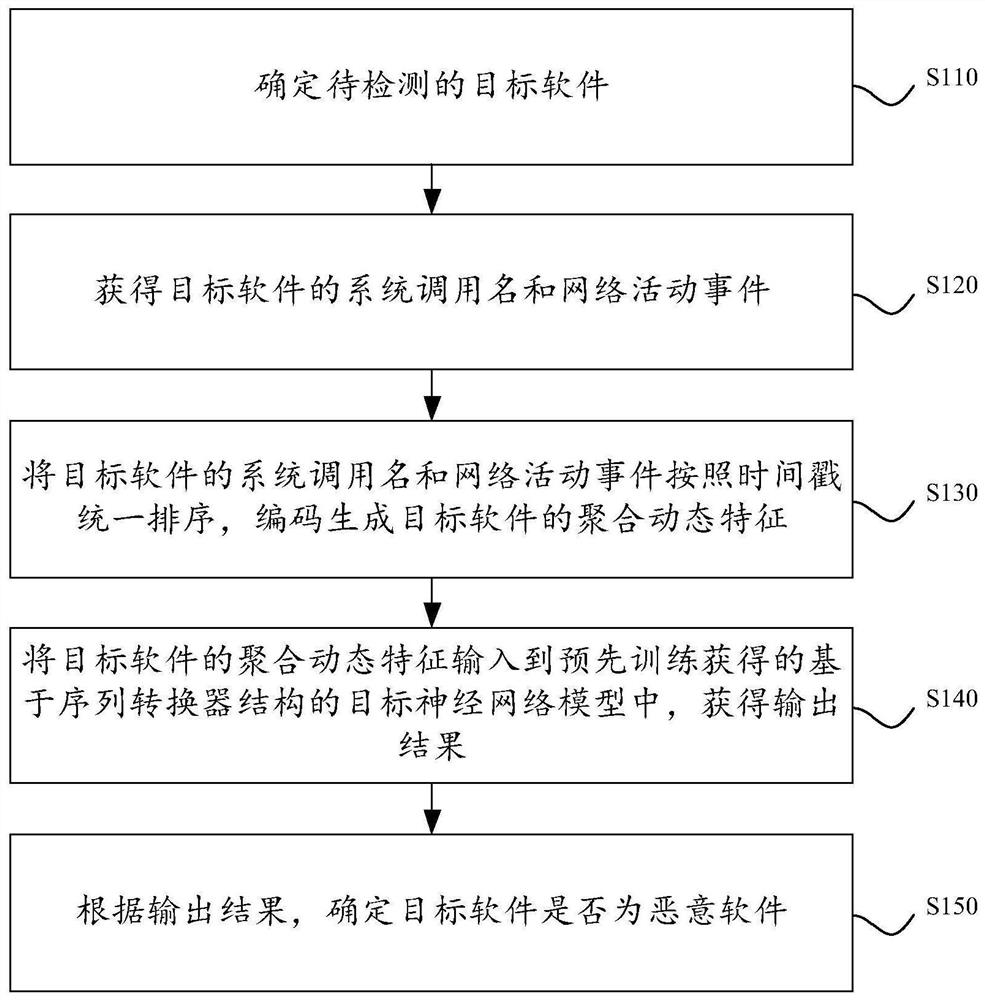
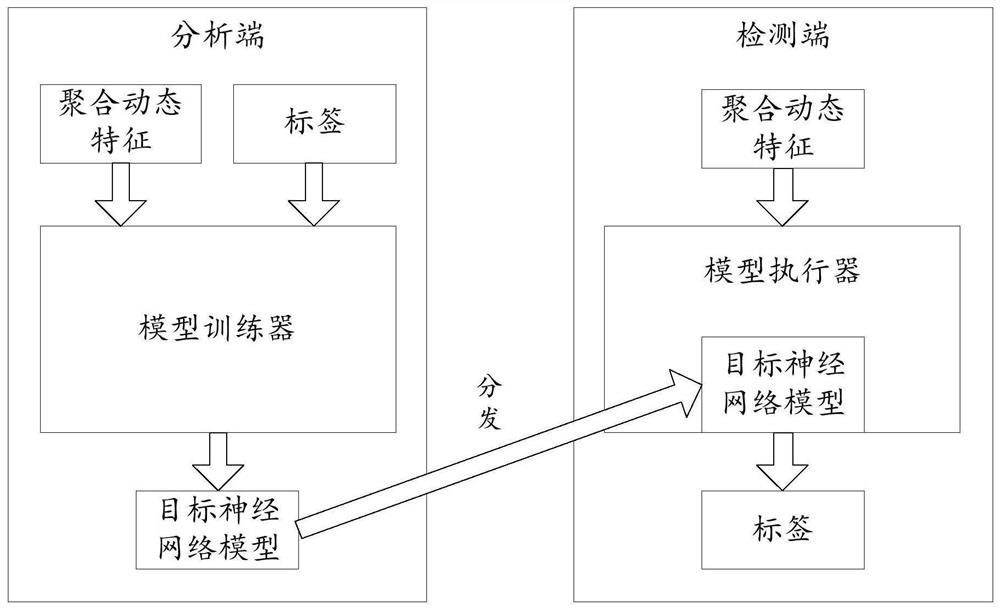
[0048] The core of the present application is to provide a malware detection method. Before describing the embodiment of the present application in detail, the malicious software detection method in the related art will be described first.
[0049] In related technologies, malware detection methods based on the Android system mainly include code feature-based detection methods and behavior analysis-based detection methods.
[0050] Among them, the code feature-based detection method operates by pattern matching the code set extracted from the Android software package. This method requires a complete software package code, and is relatively weak against increasingly diverse means of packing and camouflage. To detect new types of malicious code, it is necessary to manually extract new code features and add them to the matching set, which is cumbersome.
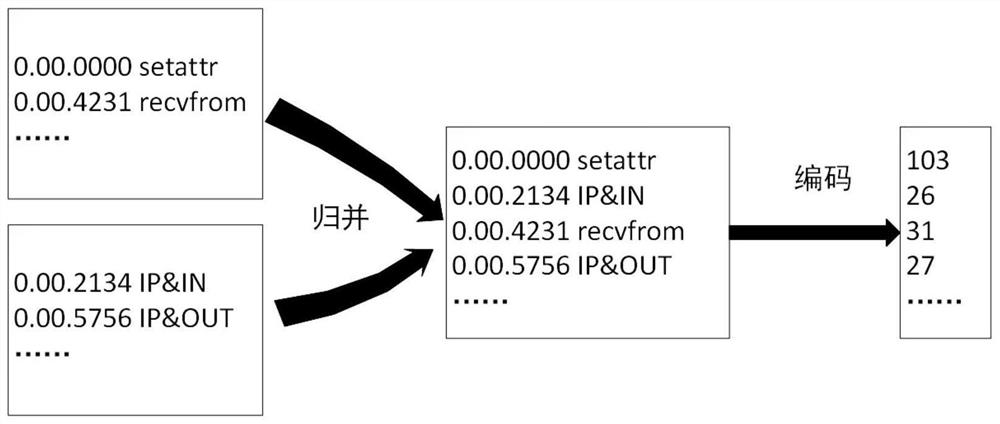
[0051] The detection method based on behavior analysis refers to the method of classifying the running records of the softwa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com