Cross-domain resource caching method and system, server and storage medium
A caching server and resource caching technology, applied in the field of realizing cross-domain resource caching, can solve problems such as video playback and other services that cannot be used normally, affect user perception and experience, and achieve the effect of easy technology and less adjustment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
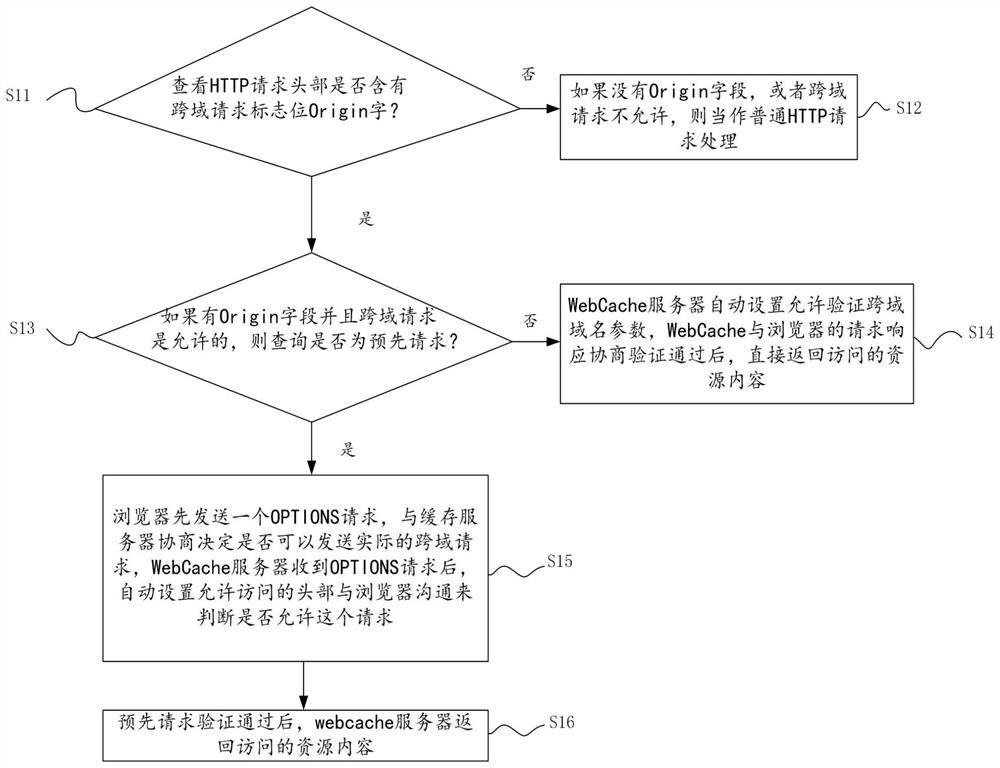
[0041] Such as figure 1As shown, a method for implementing cross-domain resource caching disclosed in the embodiment includes the following steps:
[0042] S11: Check whether the HTTP request header contains the origin field of the cross-domain request flag;
[0043] Specifically, the WebCache cache monitoring subsystem first checks whether the HTTP request header contains a cross-domain request flag Origin field; the origin is a URI that tells the server where the request comes from. It does not contain any path information, just the server name . In particular, the value of Origin can be an empty string. It is worth noting that not only cross-domain requests, but ordinary requests also carry Origin header information.
[0044] S12: If there is no Origin field, or the cross-domain request is not allowed, it will be treated as a normal HTTP request;
[0045] In this step, if there is no Origin field in the step, or the cross-domain request is not allowed, it is treated as a...
Embodiment 2
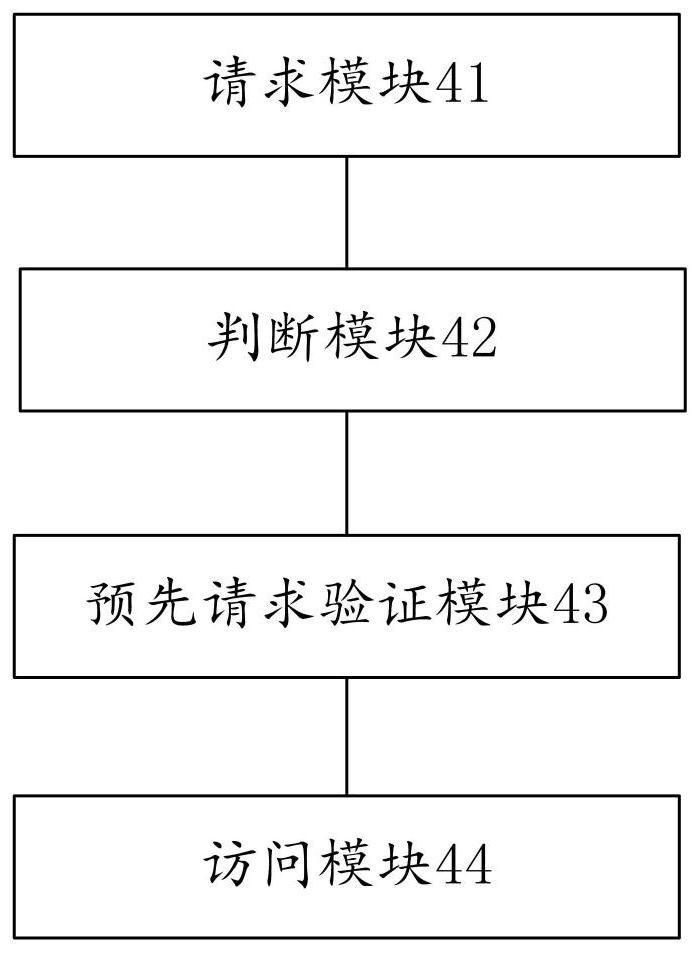
[0064] Figure 4 is another optical cable pipeline data analysis system shown in an exemplary embodiment of the present invention, such as Figure 4 shown, including:
[0065] The request module 41 is used to check whether the HTTP request header contains the origin field of the cross-domain request flag;
[0066] Judgment module 42, if there is no Origin field, or the cross-domain request is not allowed, it will be treated as a normal HTTP request;
[0067] If there is an Origin field and cross-domain requests are allowed, check whether it is a pre-request;
[0068] If it is not pre-requested, the WebCache server will automatically set the parameters allowing verification of cross-domain domain names; Access-Control-Allow-Origin, after WebCache and the browser's request response negotiation and verification pass, it will directly return the accessed resource content;
[0069] The pre-request verification module 43 is used for if it is a pre-request, the browser first sends...
Embodiment 3
[0079] Figure 5 A schematic structural diagram of a server according to Embodiment 3 of the present invention is shown, as shown in Figure 5 As shown, the terminal may include: a processor (processor) 502 , a communication interface (Communications Interface) 504 , a memory (memory) 506 , and a communication bus 508 .
[0080] in:
[0081] The processor 502 , the communication interface 504 , and the memory 506 communicate with each other through the communication bus 508 .
[0082] The communication interface 504 is configured to communicate with network elements of other devices such as clients or other servers.
[0083] The processor 502 is configured to execute the program 510, specifically, may execute relevant steps in the above-mentioned embodiment of the method for implementing cross-domain resource caching.
[0084] Specifically, the program 510 may include program codes including computer operation instructions.
[0085] The processor 502 may be a central proce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com