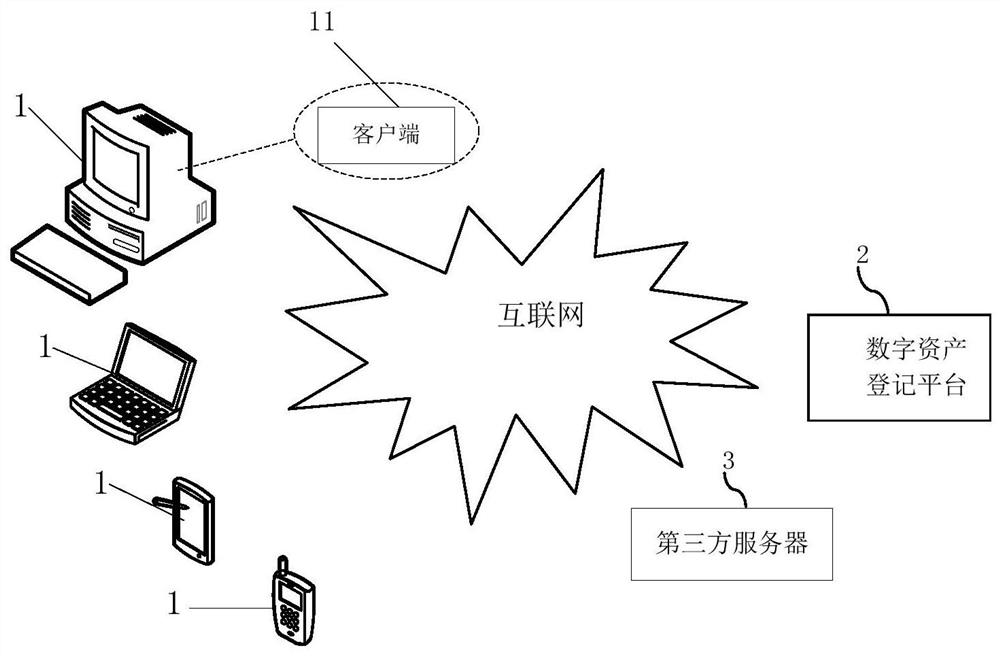
A method of verifying and authenticating authenticity of digital assets
A technology of digital assets and authenticity, applied in the direction of digital data authentication, digital data protection, digital transmission system, etc., to achieve the effect of ensuring effective progress
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
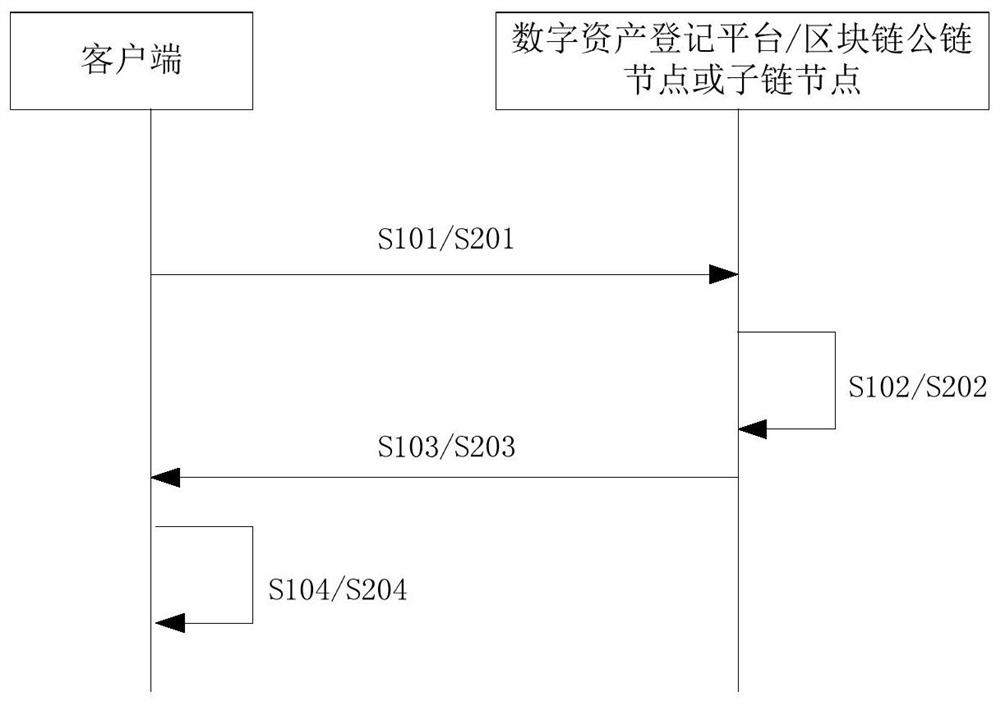
[0078] see figure 2 , figure 2 It is a flow chart of the first and second embodiments of the method for verifying the authenticity of certified digital assets provided by this application.
[0079] S101: After receiving the authenticated digital asset data whose authenticity has not been verified, the client needs to send the authenticated digital asset data to the digital asset registration platform; wherein, the authenticated digital asset data is the data including the authentication code and the digital asset entity package; in this embodiment, the data package can be in the form of an encrypted ciphertext data package plus a public key. At this time, when the client sends the data package to the digital asset registration platform, it needs to send the public key together to decrypt it through the public key the packet.
[0080] S102: The digital asset registration platform uses a digital signature algorithm to calculate the hash value A of the digital asset entity, a...
Embodiment 2
[0089] The difference between this embodiment and Embodiment 1 is that, in addition to extracting and storing the hash value in the authentication summary through the digital asset registration platform to verify the authenticity of the authenticated digital asset received by the client, the blockchain can also be extracted The hash value in the blockchain digest stored in the network is used to verify the authenticity of the certified digital assets received by the client, see also figure 2 , the digital asset registration platform at this time can be replaced by blockchain public chain nodes or sub-chain nodes. Methods as below:
[0090] S201: The client sends the certified digital asset data to the public chain node or sub-chain node in the blockchain network; wherein, the certified digital asset data is a data packet including the authentication code and the digital asset entity; in this embodiment The form of the data packet is the same as that in the first embodiment, ...
Embodiment 3
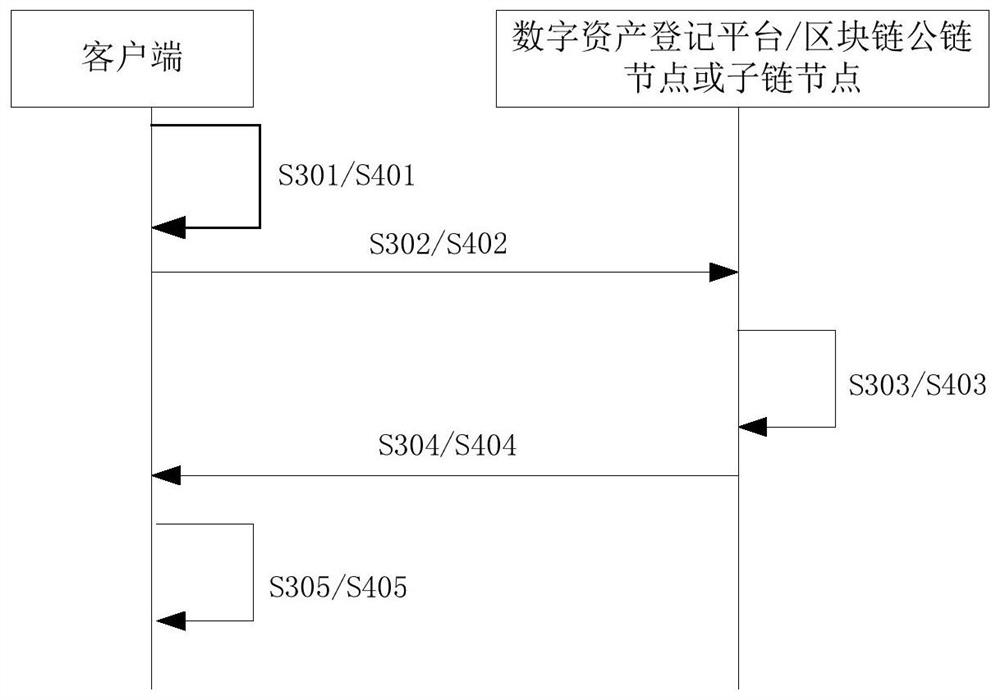
[0098] The difference between this embodiment and the first embodiment is that the first embodiment uses the form of sending the authentication code and the data packet of the digital asset entity, and the digital asset registration platform calculates the hash value of the digital asset entity to complete the verification process. In order to avoid problems such as mobile digital asset entities occupying too many transmission resources, increasing computing resource consumption and delaying the verification process, the client can complete the hash value calculation process for digital asset entities, and only the calculated hash value and authentication The code is sent to the digital asset registration platform. At this time, the digital asset registration platform only needs to perform the extraction and verification process. For details, see image 3 , image 3 The flow charts of the third and fourth embodiments of the method for verifying the authenticity of certified di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com