Mass storage device encryption method, main controller and access device
A mass storage and encryption method technology, which is applied in the field of information security, can solve the problems of affecting the transmission speed of equipment and low applicability, and achieve the effects of reducing encryption costs, improving security, and saving the analysis process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
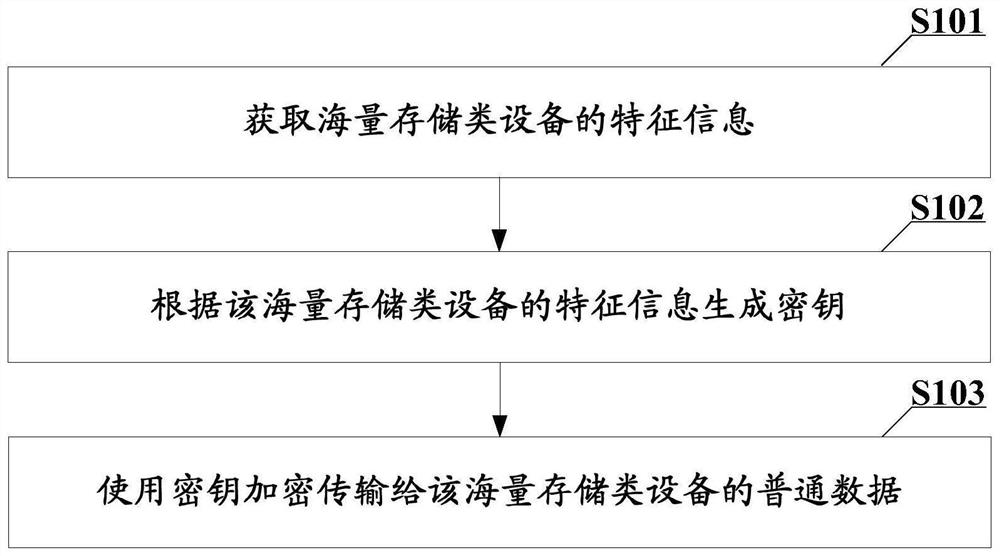
[0042] The embodiment of this application provides an encryption method for mass storage devices applied to the main controller of the access device, which can be found in figure 1 shown, including:
[0043] S101: Obtain characteristic information of mass storage devices.
[0044] In the embodiment of this application, after the mass storage device is connected to the access device, the main controller of the access device can analyze the control transmission with the mass storage device, so as to obtain the characteristics of the mass storage device. information.
[0045] In this embodiment of the present application, the characteristic information of a mass storage device refers to information that can uniquely identify a mass storage device, such as a device descriptor of a mass storage device.
[0046] It should be understood that the device descriptor of a mass storage device consists of 14 fields. Each of its fields can independently reflect certain information of mas...
Embodiment 2
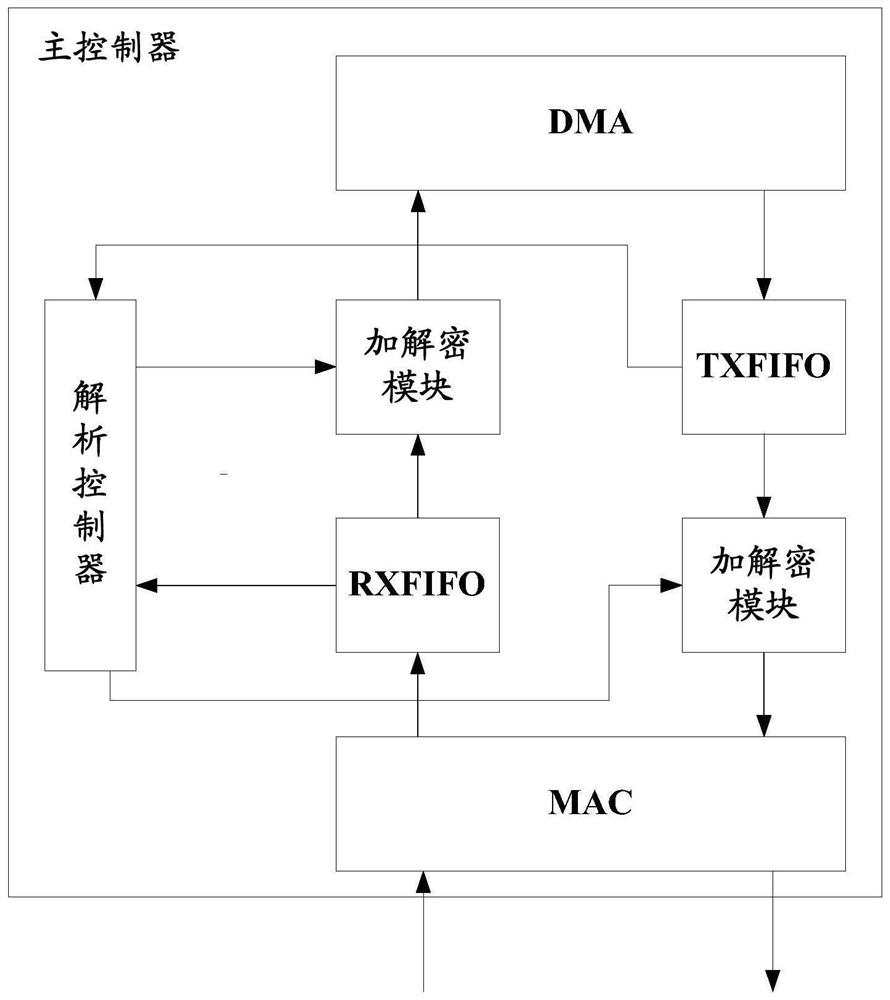
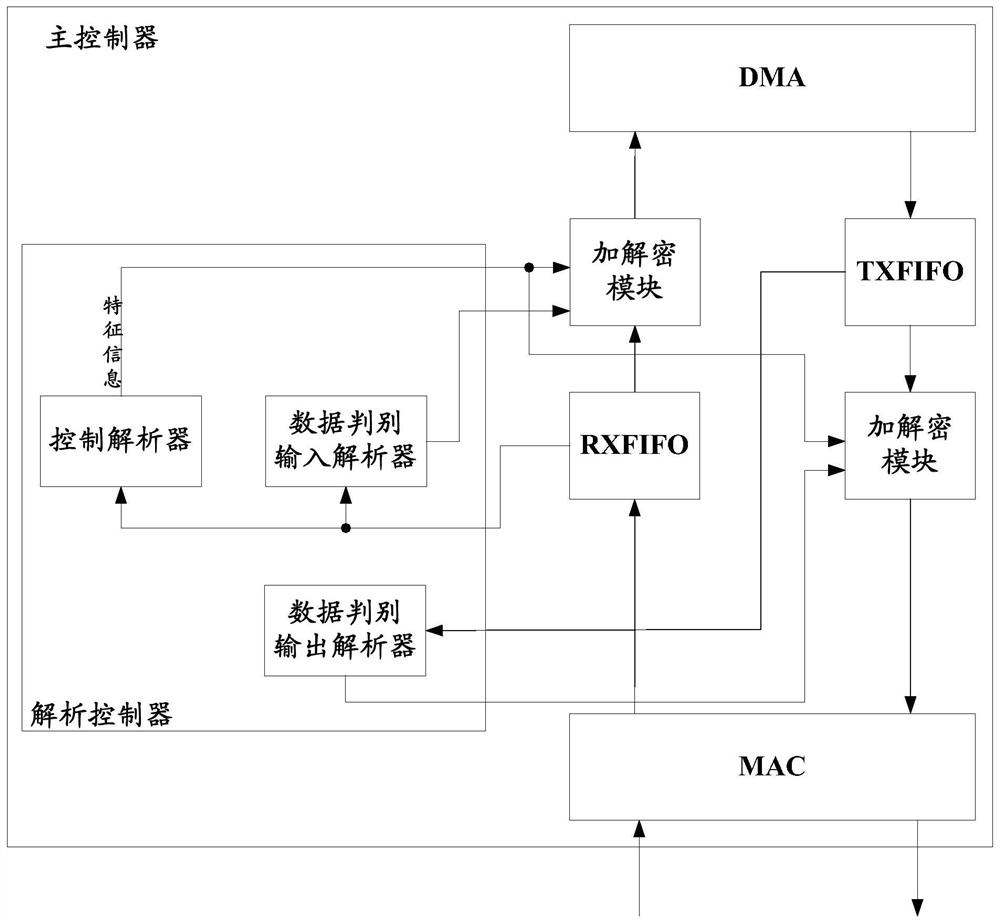
[0088] This embodiment provides a main controller and an access device.
[0089] see figure 2 As shown, the main controller may include an electrically connected parser controller (Parser Control, also called Parser_Ctrl) and an encryption and decryption module. in:
[0090] The analysis controller is used to obtain the characteristic information of the mass storage device, and distinguish the common data transmitted to the mass storage device;
[0091] The encryption and decryption module is used to generate a key according to the feature information of the mass storage device, and use the key to encrypt ordinary data transmitted to the mass storage device.
[0092] Wherein, the encryption and decryption module can be realized by selecting a corresponding algorithm circuit according to the difference of the adopted encryption and decryption algorithms. For example, when sm3 is used to generate a key, and sm4 is used for encryption and decryption, the encryption and decryp...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap