Method for verifying service chain, sending node, forwarding node and service function node
A technology of business function and forwarding node, applied in the field of business chain, which can solve the problem of inapplicability of business chain verification method.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
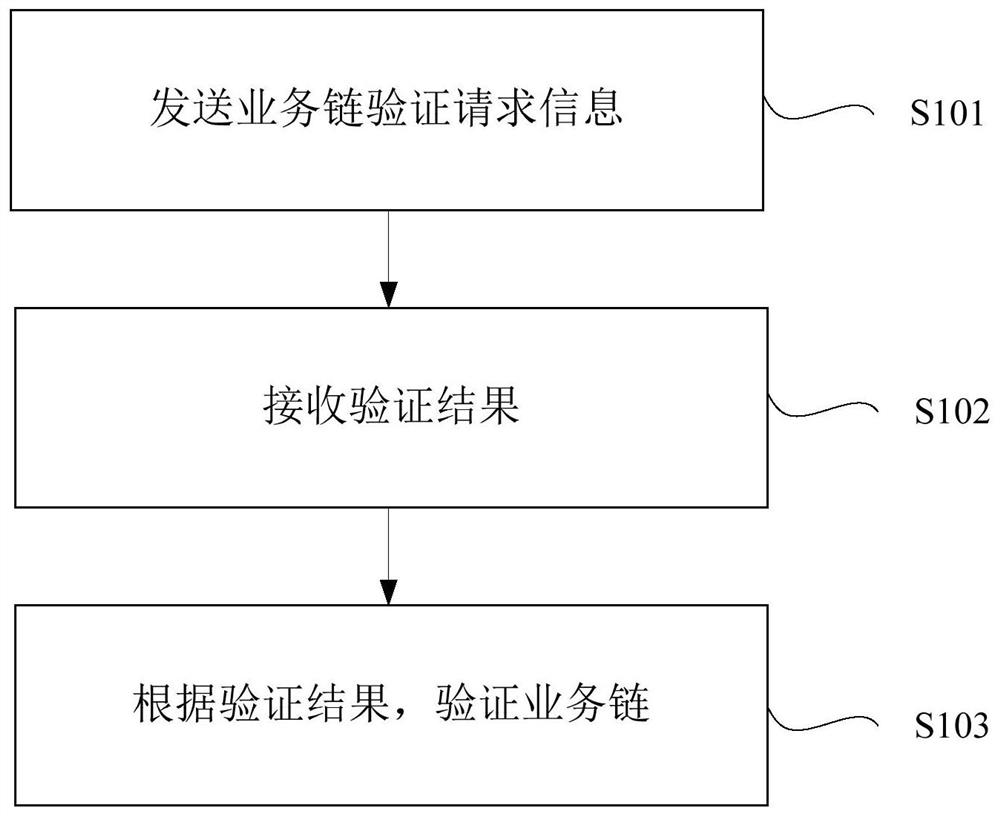
[0252] The specific method for verifying the business chain of this embodiment may include the following steps:
[0253] A101. The sending node constructs and sends service chain verification request information.
[0254] Wherein, the sending node first obtains the SIDs of the service nodes (SFF node and SF node) of the service chain to be verified, so as to determine the SF node to be verified.
[0255] Specifically, the SID of the service node of the service chain to be verified can be acquired locally, or can be configured by the control plane.
[0256] Wherein, the sending node also needs to add identity information (identity SID, identity identifier) to the service chain verification request information to indicate the identity of the service chain verification request information.
[0257] Among them, the sending node also needs to add the check node information, verification parameter information, etc. to the service chain verification request information.
[0258] ...
specific Embodiment 2
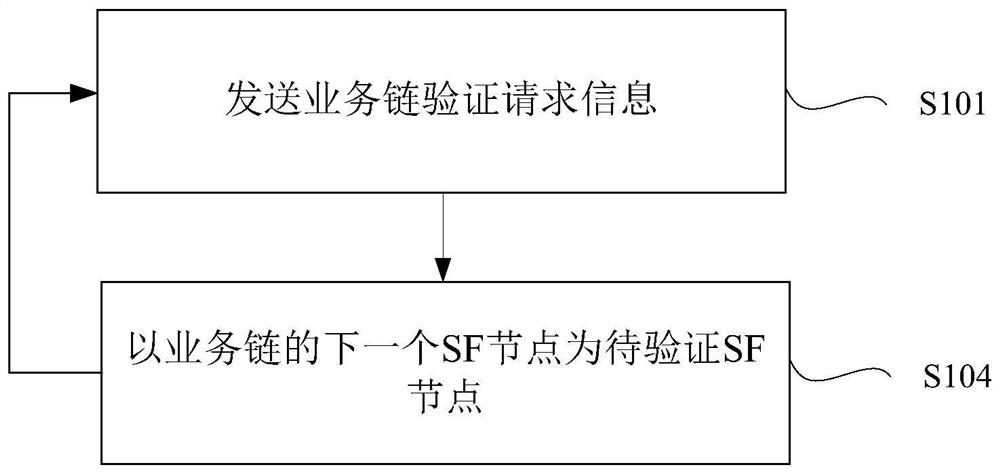
[0271] This embodiment is used for the path verification of the service chain, specifically, the path verification is realized through the interaction between the SF node and the SFF node.
[0272] refer to Figure 11 , the sending node in the network of this embodiment is connected to the first service function forwarding node (SFF1), and SFF1 is connected to the second service function forwarding node (SFF2); SFF1 has the first service function node (SF1) and the second service function node under SFF1 (SF2), SFF2 has a third service function node (SF3); meanwhile, both SFF1 and SFF2 are connected to the check node.
[0273] It should be understood that in this embodiment, the sending node and the checking node are logically regarded as two different nodes for description, and the entities of the two may be one node.
[0274] In this embodiment, the service chain to be verified is SF1-->SF2-->SF3 as an example for illustration.
[0275] refer to Figure 12 , the specific ...
specific Embodiment 3
[0319] This embodiment is used for the path verification of the service chain, specifically, the path verification is realized through the pre-stored information of the SFF node itself.
[0320] refer to Figure 11 , the network in this embodiment is similar to the above embodiment.
[0321] In this embodiment, the service chain to be verified is SF1-->SF2-->SF3 as an example for illustration.
[0322] refer to Figure 12 , the specific method for verifying the service chain in this embodiment may include the following steps
[0323] A301. The sending node constructs and sends service chain verification request information.
[0324] A302, SFF1, after receiving the service chain verification request information, recognizes it as the service chain verification request information, and queries SF1 in the locally pre-stored information table (such as adding in the forwarding table, or adding an attribute table associated with the forwarding table) The location and SF type of S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com