Ethereum phishing fraud detection method and device based on graph classification
A technology for phishing and detection methods, applied in the field of Ethereum network security, can solve the problems of complex processing, high time and computing costs, and achieve the effects of ensuring accuracy, improving expression ability, and good applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
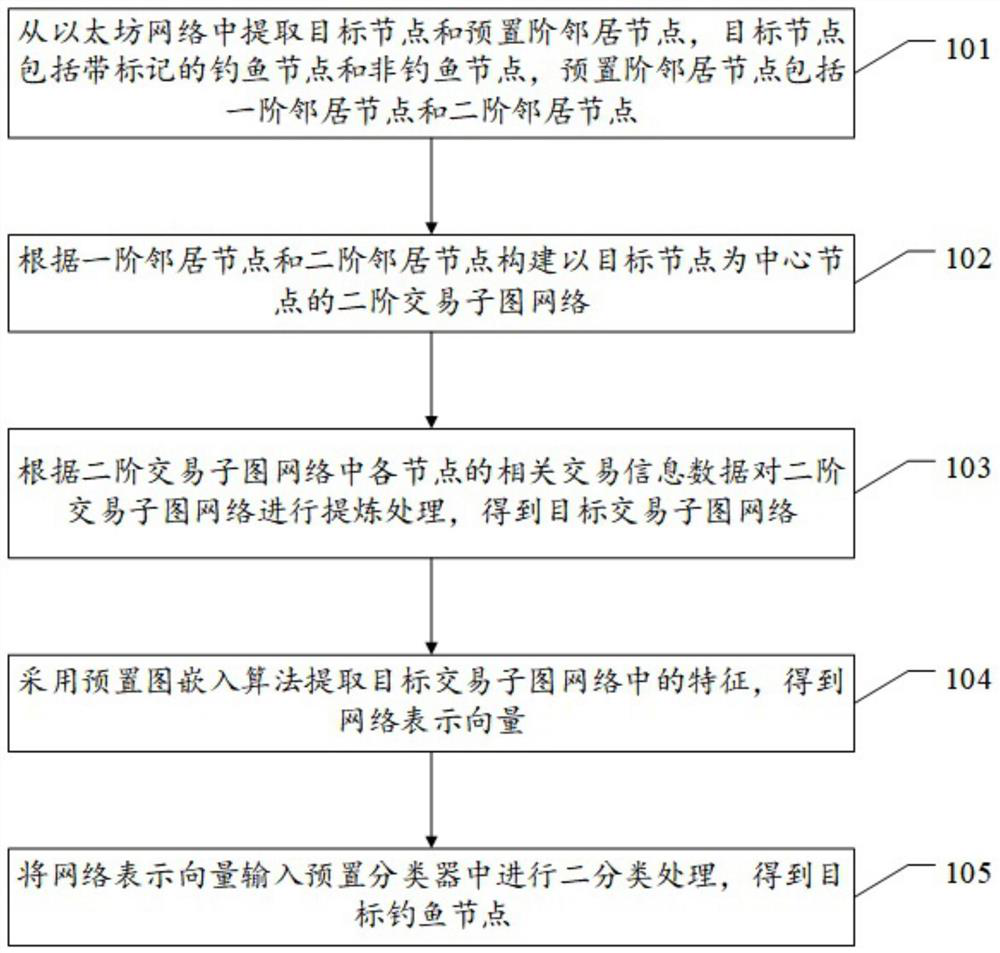
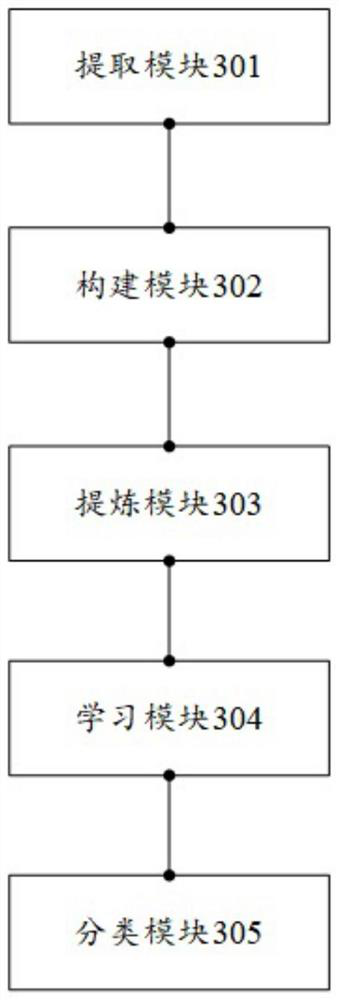
[0058] For ease of understanding, see figure 1 , Embodiment 1 of a graph classification-based Ethereum phishing fraud detection method provided by the application, including:
[0059] Step 101. Extract target nodes and preset order neighbor nodes from the Ethereum network. The target nodes include marked phishing nodes and non-fishing nodes, and the preset order neighbor nodes include first-order neighbor nodes and second-order neighbor nodes.
[0060] It should be noted that a node in the Ethereum network is an Ethereum account and has a corresponding account address; the first-order neighbor node is a related node that has direct transaction records with the target node, and the second-order neighbor node refers to a node that has a direct transaction record with the target node. The first-order neighbor nodes have related nodes with direct transaction records, and there are historical transaction record information between the associated nodes. Through the historical transa...
Embodiment 2
[0070] For ease of understanding, see figure 2 , the present application provides a second embodiment of a graph classification-based Ethereum phishing fraud detection method, including:
[0071] Step 201. Obtain historical transaction records in the Ethereum network. The historical transaction records include node account addresses, historical transaction amounts, historical transaction timestamps, historical transaction flow directions, and historical transaction times.
[0072] Step 202, extracting the target node and the preset order neighbor nodes from the historical transaction records.
[0073] It should be noted that the historical transaction records contain more information, mainly describing the dynamic changes in the transaction process. The target nodes include marked fishing nodes and non-fishing nodes, and the preset order neighbor nodes include first-order neighbor nodes and second-order neighbor nodes. The first-order neighbor nodes are related nodes that h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com