Malicious code identification method and device, computer equipment and medium
A malicious code and identification method technology, applied in computer parts, computer security devices, computing, etc., can solve the problems of inaccurate target code identification and misjudgment, and achieve a wide range of applications, low implementation costs, and reduced possibility. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The malicious code identification method, device, computer equipment and media specifically provided by the present invention will be explained and illustrated in detail below in conjunction with the accompanying drawings.
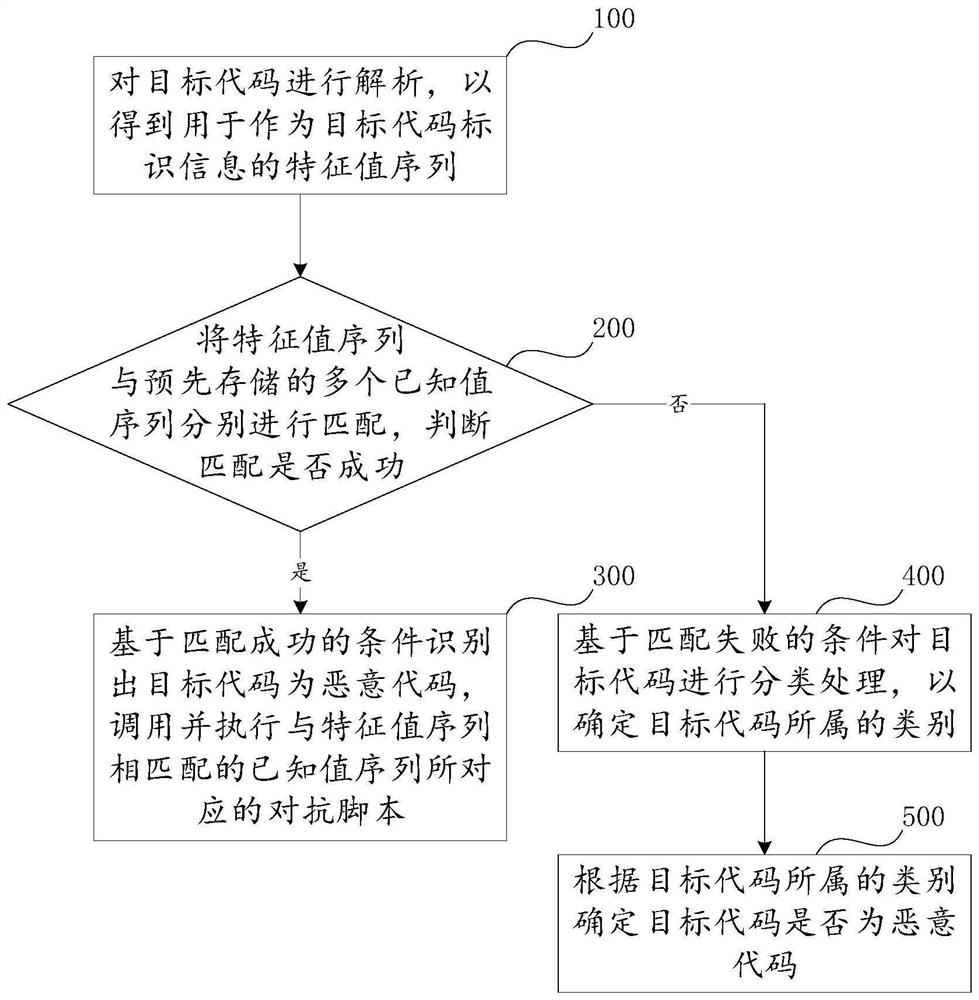
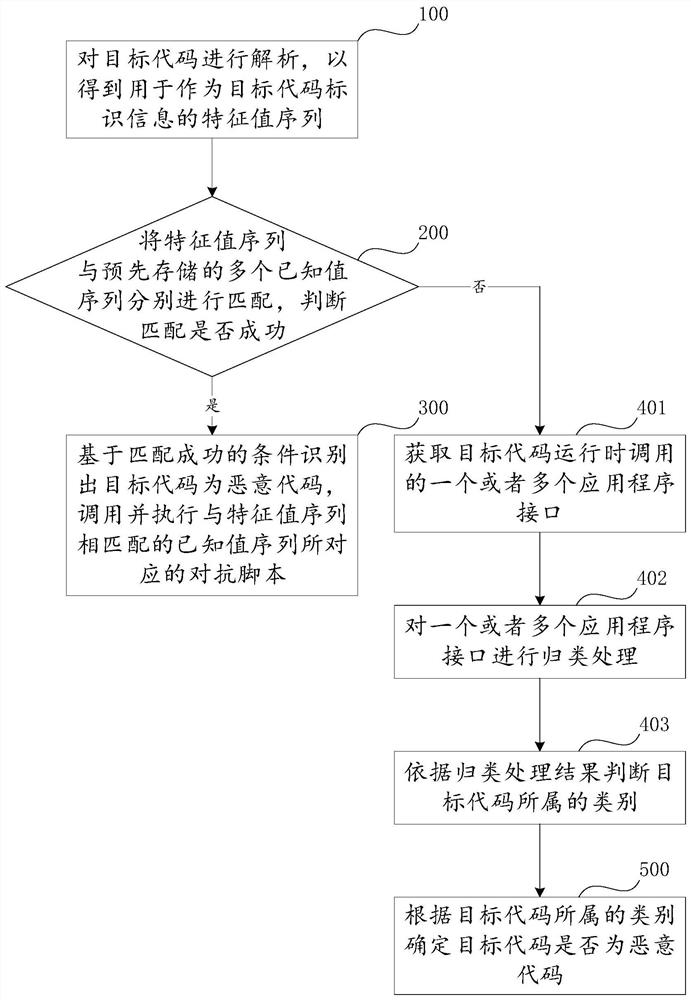
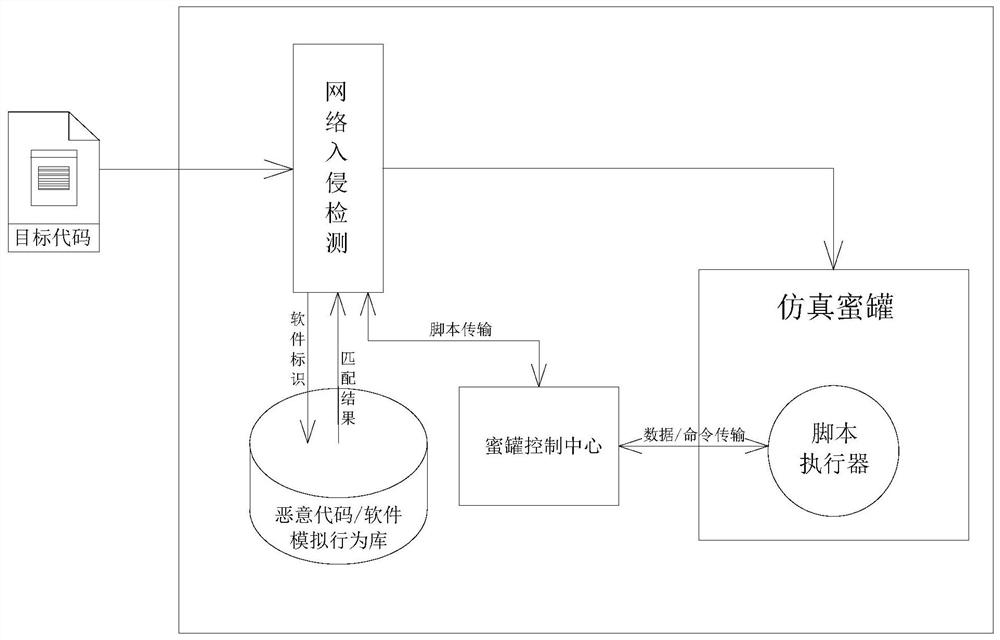
[0047] Such as figure 1 shown, and can be combined with figure 2 , one or more embodiments of the present invention may provide a malicious code identification method. The identification method effectively combines the static detection method and the dynamic detection method. Specifically, the malicious code identification method includes but is not limited to at least one of the following steps.
[0048] Step 100, analyzing the target code to obtain a feature value sequence used as identification information of the target code. The object code identification information can be used to distinguish different codes or software, and can also be understood as software identification, that is, the object code can be a piece of software or a program. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com