Program running method and system
A technology for program running and running equipment, applied in the computer field, and can solve problems such as leakage of sensitive information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
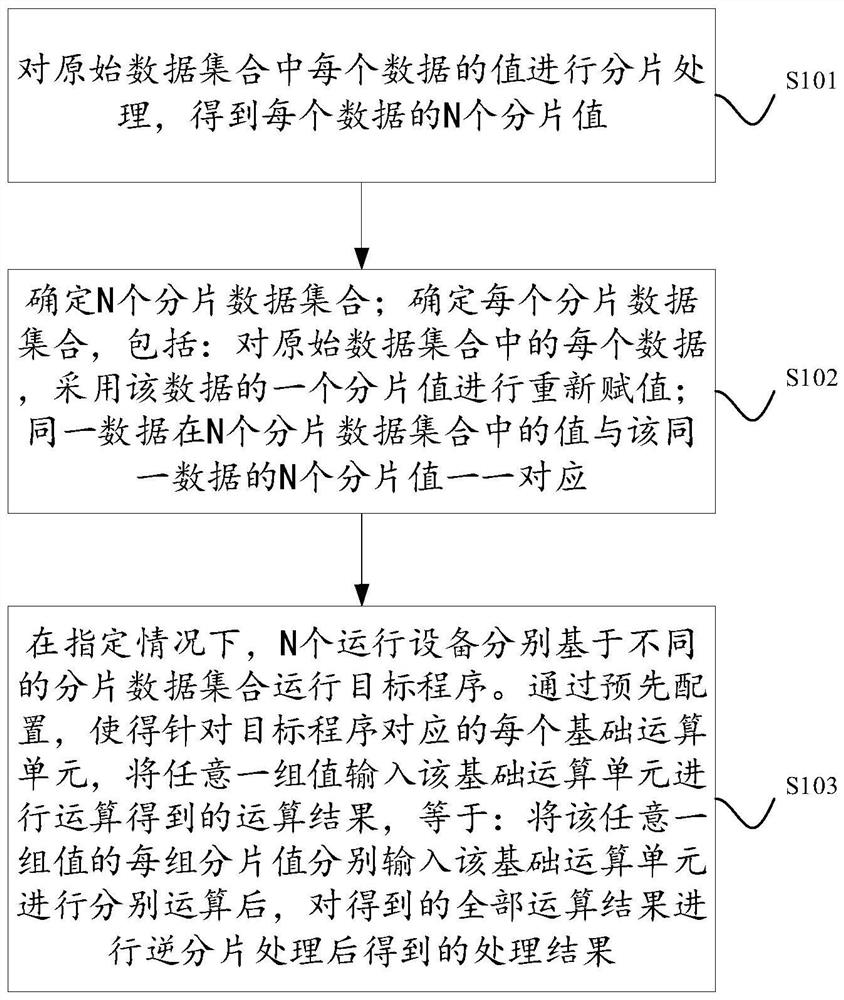
[0156] Embodiment 1: The original data set may be stored on a target device other than the N running devices.
[0157] The target device may be any storage device other than the N running devices, and stores all the data in the original data set. The target device can perform fragmentation processing for each data in the original data set to obtain N fragmentation values, thereby creating N fragmented data sets, where each fragmented data set can contain all the data in the original data set , and respectively reassign the N fragment values to the data in the N fragment data sets, so that the values of the same data in the N fragment data sets correspond one-to-one to the N fragment values of the same data.
[0158] The target device may send the created N fragmented data sets to the N operating devices respectively, so that the N operating devices correspond to the N fragmented data sets one-to-one.
[0159] For ease of understanding, in an optional embodiment, such as...
Embodiment 2
[0162] Embodiment 2: The original data set may be distributed and stored on N running devices.
[0163] That is to say, each of the N operating devices may store part of the data in the original data set.
[0164] To obtain N fragment values of each data and determine N fragment data sets, specifically, the data values stored locally by N operating devices (data values stored by the operating devices and belonging to the original data set) Perform fragmentation processing and interact with each other with fragmentation processing results, so that each operating device can obtain a fragmentation value for each data in the original data set, that is, the fragmented data set.
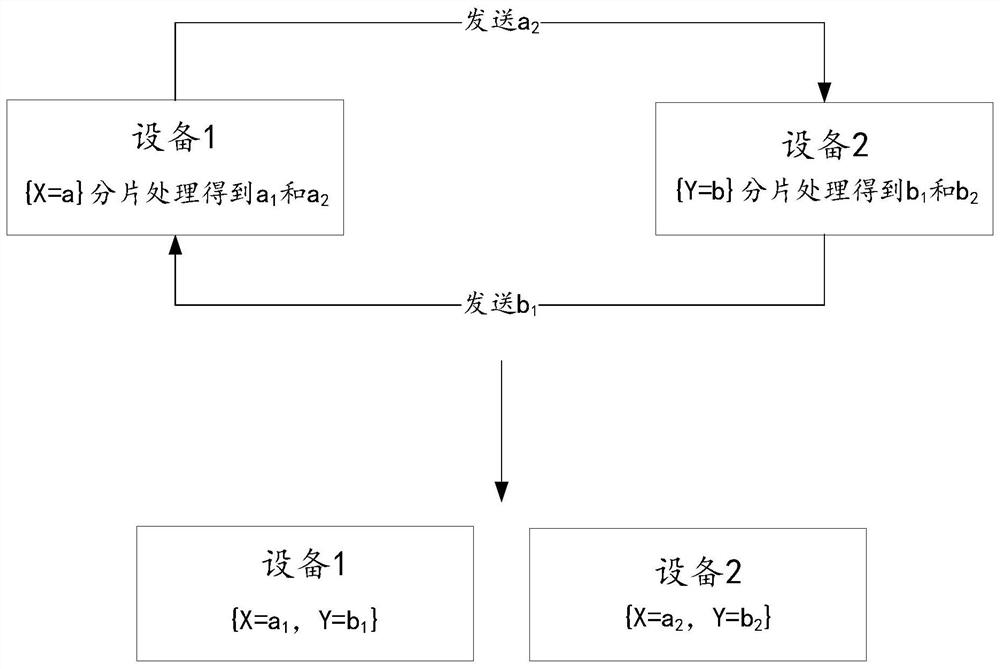
[0165] For ease of understanding, in an optional embodiment, such as image 3 As shown, it is a schematic diagram of the principle of another method for determining a fragmented data set provided in this specification, which includes device 1 and device 2 .
[0166]For the original data set {X=a, Y...
example 1
[0268] Example 1: Different data holders store sample data of different users. For example, running device 1 stores sample data of user 1, including feature X=a; running device 2 stores sample data of user 2, including feature X=b.
[0269] Then the two running devices perform slice processing on each feature of each sample data, running device 1 gets a1 and a2, and running device 2 gets b1 and b2. After interacting with each other, the running device 1 has a fragmented data set {X=a1 (user 1), X=b1 (user 2)}, and the running device 2 has a fragmented data set {X=a2, X=b2} .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com