Maximum likelihood estimation method and system for inferring attack stage based on factor graph
A technology of maximum likelihood estimation and inference attack, which is applied in the field of network security, can solve the problems of low inference efficiency and poor effect in the attack stage, and achieve the effect of avoiding joint probability calculation and speeding up calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be described in further detail below in conjunction with the accompanying drawings.
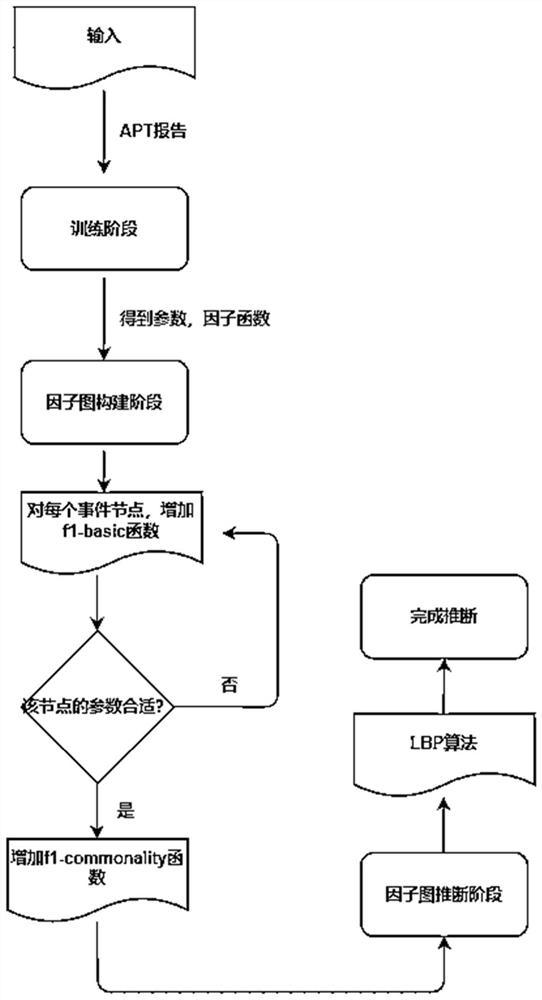
[0045] see figure 1 , a factor graph-based inference attack stage maximum likelihood estimation method proposed by the present invention mainly includes the following three stages: training, factor graph construction and factor graph inference. First, APT data preprocessing is collected from sources (public APT datasets, APT data in papers) to normalize the data. Then, train with these normalized data to get the corresponding parameters required by the system. Second, receive the input attack chain, and construct the corresponding factor nodes and factor functions. Finally, the Loopy Belief Propagation algorithm is used to obtain the maximum likelihood estimation of the attack phase.
[0046] In an embodiment of the present invention, a method for inferring attack phase maximum likelihood estimation based on a factor graph includes the following steps:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com