User website interaction behavior credibility judgment method based on virtual fingerprints
A technology of credibility and behavior, applied in the field of information security, can solve problems such as psychological factors that cannot be directly observed or measured, and achieve the effect of solving network security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described in detail below in conjunction with the accompanying drawings.
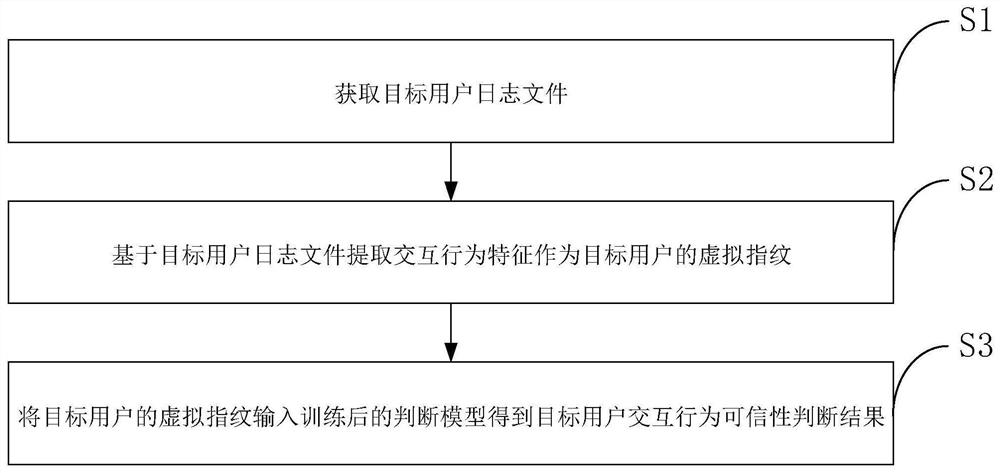
[0032] Such as figure 1 As shown, the present invention discloses a method for judging the credibility of user website interaction behavior based on virtual fingerprints, including:
[0033] S1. Acquiring the log file of the target user;
[0034] In the present invention, log data of user operations can be collected from the website, including time stamp, user ID, event type, current page, stay time, UA, URL, etc.
[0035] S2. Extracting interactive behavior features based on the target user log file as the virtual fingerprint of the target user;
[0036] In the present invention, interactive behavior features are constructed from log files without using any additional methods. In addition, the interaction behavior mode in the present invention involves many aspects of the interaction process, and is not limited to one behavior. The unique interactive beh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com