Transaction method and system, server and storage medium
A transaction method and server technology, applied in the computer field, can solve the problems of user inconvenience, unable to transfer smoothly, unable to transfer to strangers, etc., and achieve the effect of unlocking password security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
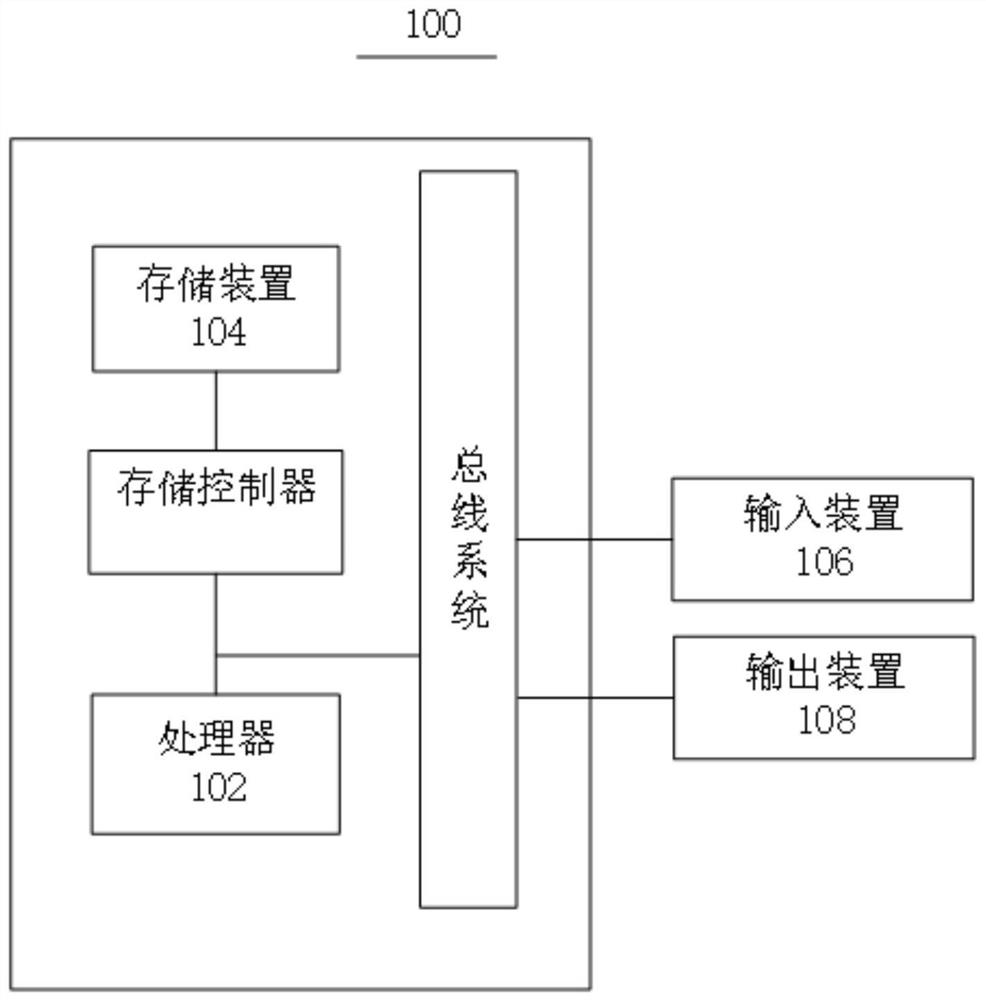
[0025] figure 1 A schematic structural diagram of a server provided in the embodiment of this application, which can be used in this application figure 1 The schematic diagram shown is used to describe an example server 100 for implementing the transaction method and system of the embodiment of the present application.
[0026] Optionally, the server 100 may be a computer, such as a computer.
[0027] Such as figure 1 A structural schematic diagram of a server is shown, the server 100 includes one or more processors 102, one or more storage devices 104, input devices 106, and output devices 108, and these components are connected through a bus system and / or other forms of mechanisms (not shown) interconnects. It should be noted that figure 1 The shown components and structure of the server 100 are exemplary rather than limiting, and the server may have figure 1 Some components shown may also have figure 1 Other components and structures not shown.
[0028] The processor...
no. 2 example
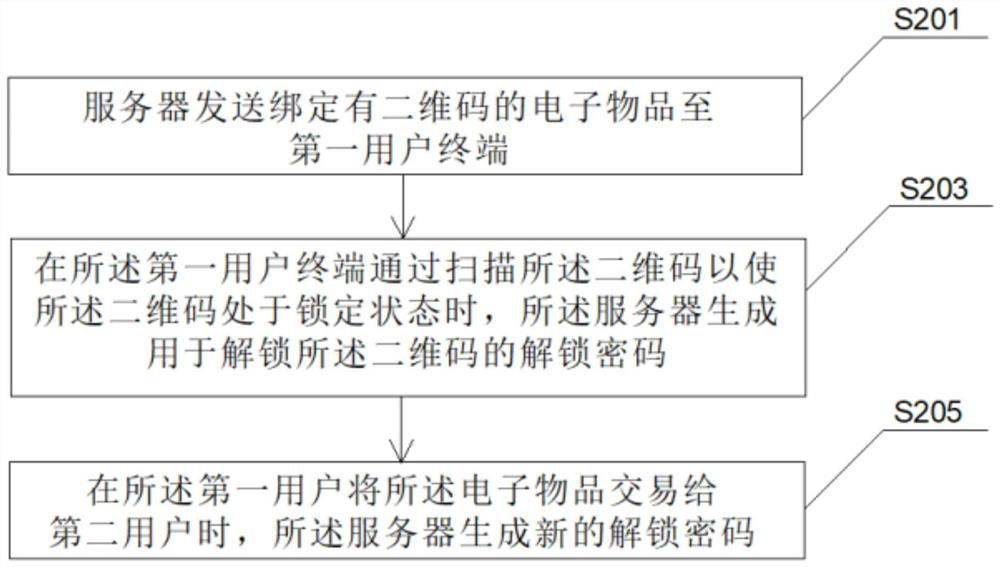
[0035] refer to figure 2 A flow chart of a trading method is shown, the method specifically includes the following steps:
[0036] Step S201, the server sends the electronic item bound with the QR code to the first user terminal.
[0037] It can be understood that the server will send the electronic item to the first user terminal after the server purchases the electronic item at the first user terminal.
[0038] Of course, it may also be an electronic item randomly sent by the server to the first user terminal, such as a coupon.
[0039] Optionally, the electronic item may be a voucher, or a purchase voucher (such as a voucher for online group buying), etc.
[0040] Of course, in actual use, the electronic item may also be an electronic visa, communication, anti-counterfeiting item, etc., which are not specifically limited here.
[0041] Step S203, when the first user terminal scans the two-dimensional code to make the two-dimensional code in a locked state, the server ge...
no. 3 example
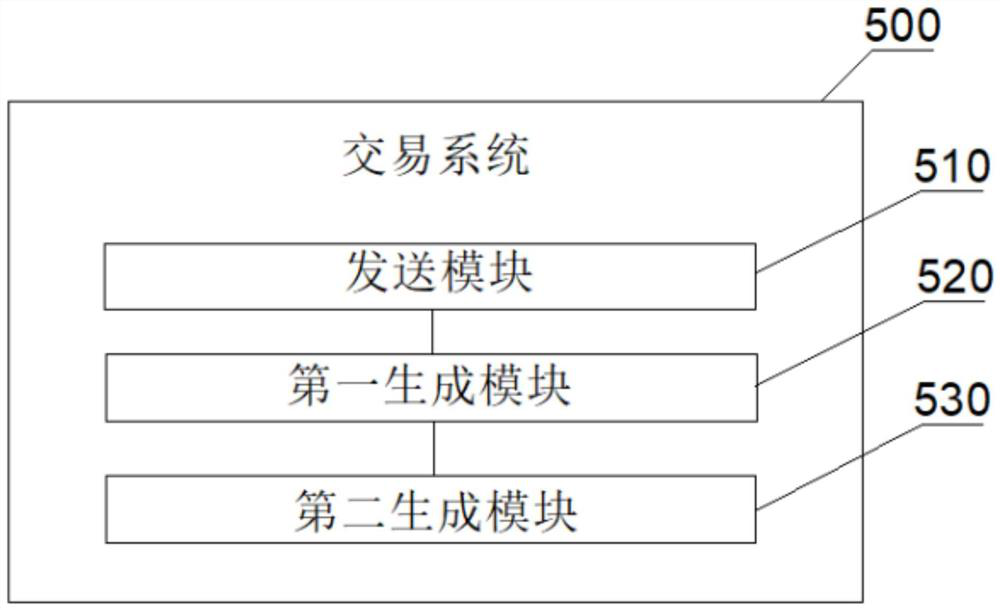
[0067] see image 3 A trading system is shown, the system 500 includes:
[0068] The sending module 510 is configured to send the electronic item bound with the QR code to the first user terminal.
[0069] The first generating module 520 is configured to generate an unlock password for unlocking the two-dimensional code when the first user terminal scans the two-dimensional code to make the two-dimensional code in a locked state.
[0070] The second generation module 530 is configured to generate a new unlock password when the first user trades the electronic item to a second user.
[0071] In a possible embodiment, the second generating module 530 is further configured to receive an unlock instruction for unlocking the two-dimensional code initiated by the first user terminal; unlock the two-dimensional code according to the unlock instruction, so that The two-dimensional code is in an unlocked state; receiving a purchase request initiated by a second user for purchasing an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com