Network fraud detection method and device thereof, electronic equipment and storage medium
A network and target network technology, applied in the field of information security, can solve problems such as identifying fraud in advance and reducing the probability of fraud incidents, and achieve the effect of reducing the probability of occurrence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
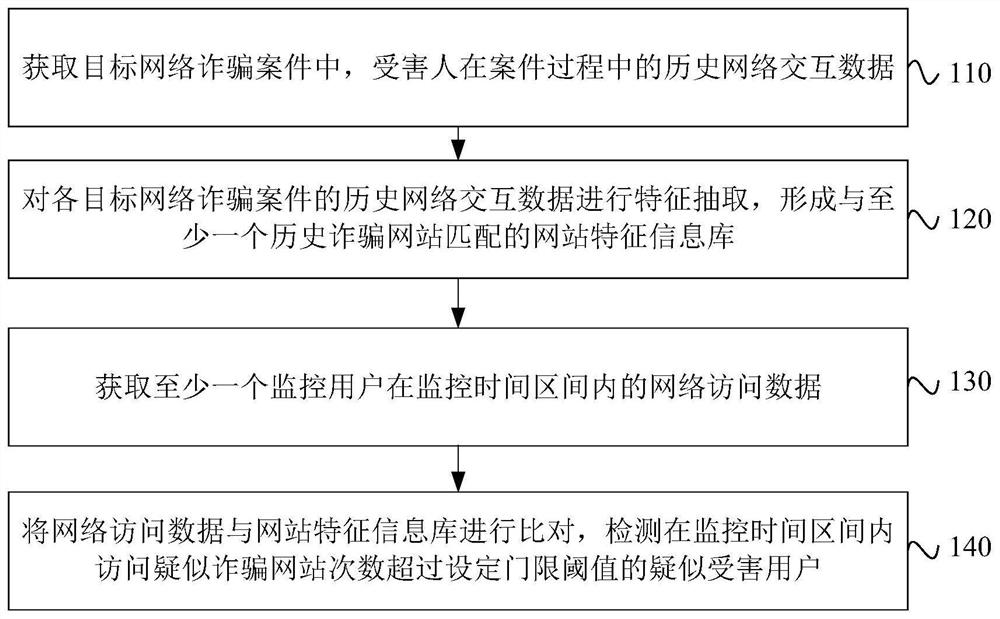
[0032] Figure 1a It is a flow chart of a network fraud detection method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of pre-identifying network fraud, especially the identification of fraud cases after gaining user trust through long-term emotional training. The method can be executed by a network fraud detection device, which can be realized by software and / or hardware, and the device can be integrated in an electronic device such as a computer or a server, such as Figure 1a As shown, the method specifically includes:
[0033] Step 110, acquiring the historical network interaction data of the victim during the course of the case in the target network fraud case.
[0034] Among them, the target online fraud cases are long-term, multi-online interactive fraud cases. Targeted online fraud cases can be different types of "short, flat and fast" types of fraud, or new types of online fraud in the form of long-term fishing for b...
Embodiment 2
[0061] Figure 2a It is a flow chart of a network fraud detection method provided in Embodiment 2 of the present invention. This embodiment is a further refinement of the above-mentioned technical solution, and the technical solution in this embodiment may be combined with each optional solution in one or more of the above-mentioned embodiments. Such as Figure 2a As shown, the method includes:
[0062] Step 210, acquiring historical network interaction data of the victim during the course of the case in the target network fraud case.
[0063] Among them, the target online fraud cases are long-term, multi-online interactive fraud cases.
[0064] Step 220, perform feature extraction on the historical network interaction data of each target network fraud case, and form a website feature information database matching at least one historical fraud website.
[0065] Optionally, feature extraction is performed on the historical network interaction data of each target network fra...
Embodiment 3
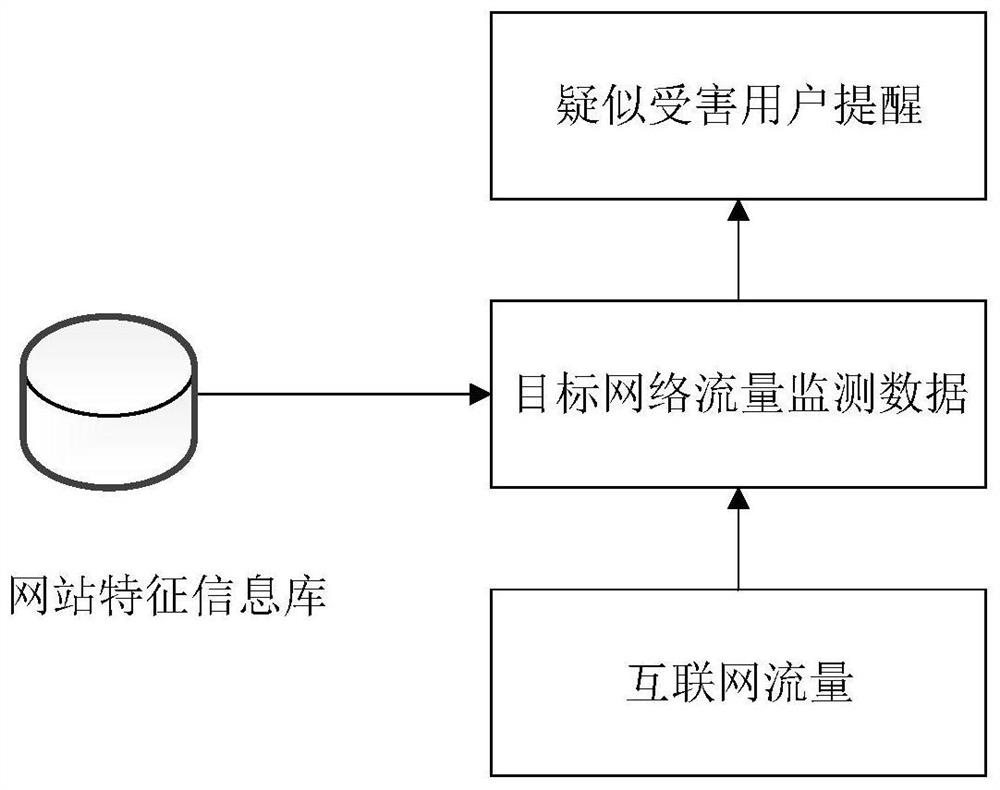
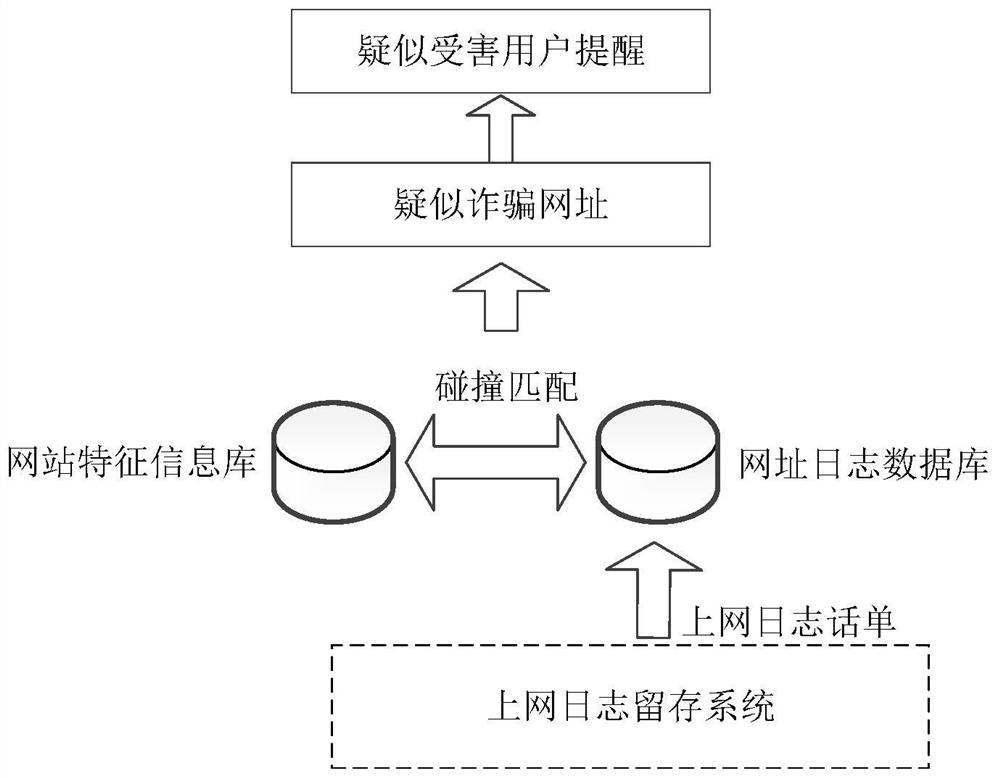
[0083] image 3 It is a schematic structural diagram of a network fraud detection device provided in Embodiment 3 of the present invention. combine image 3 , the device includes: a historical network interaction data acquisition module 310 , a website characteristic information database formation module 320 , a network access data acquisition module 330 and a suspected victim user detection module 340 . in:
[0084] The historical network interaction data acquisition module 310 is used to acquire the historical network interaction data of the victim during the course of the case in the target network fraud case, wherein the target network fraud case is a long-term, multi-online interaction fraud case;
[0085] The website characteristic information database formation module 320 is used to extract the characteristics of the historical network interaction data of each target network fraud case, and form a website characteristic information database matching at least one histo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com