Mobile network honeypot system for 5G independent networking
A mobile network and networking technology, applied in transmission systems, electrical components, etc., can solve problems such as penetration attacks and exploit attacks, signaling attacks, network security attacks, etc., and achieve the effect of reducing the risk of attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
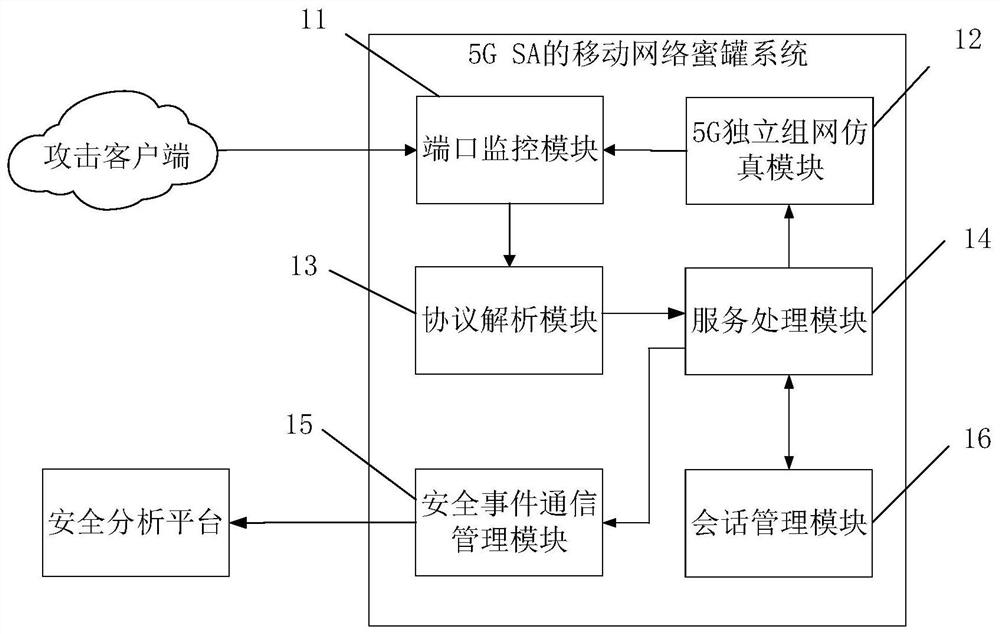
[0024] figure 1 It is a schematic structural diagram of a 5G independent networking mobile network honeypot system provided by Embodiment 1 of the present invention. The system specifically includes: a service processing module 14, a 5G independent networking simulation module 12 connected to the service processing module 14, and a port monitoring module 11 and a security event communication management module 15.
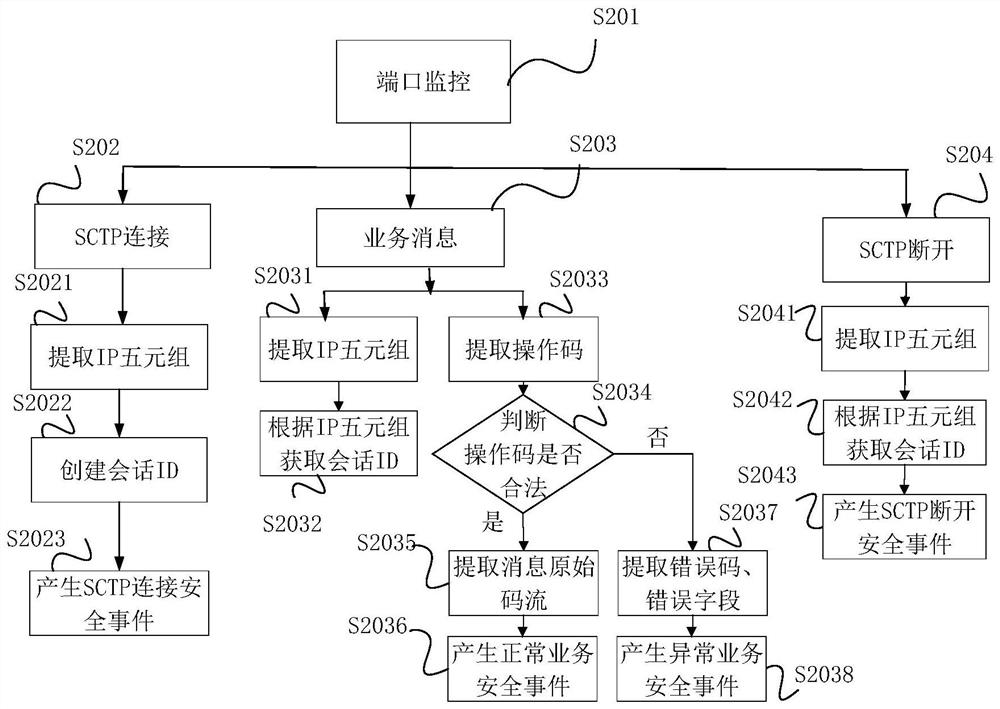
[0025] Among them, the 5G independent networking simulation module 12 is used to provide different types of simulated network elements; the port monitoring module 11 is used to monitor the port of each simulated network element to obtain the signaling message sent by the attacking client, and The signaling message is transmitted to the service processing module; the service processing module 14 is used to generate a corresponding security event according to the signaling message, and transmits the security event to the security event communication management module;...
Embodiment 2
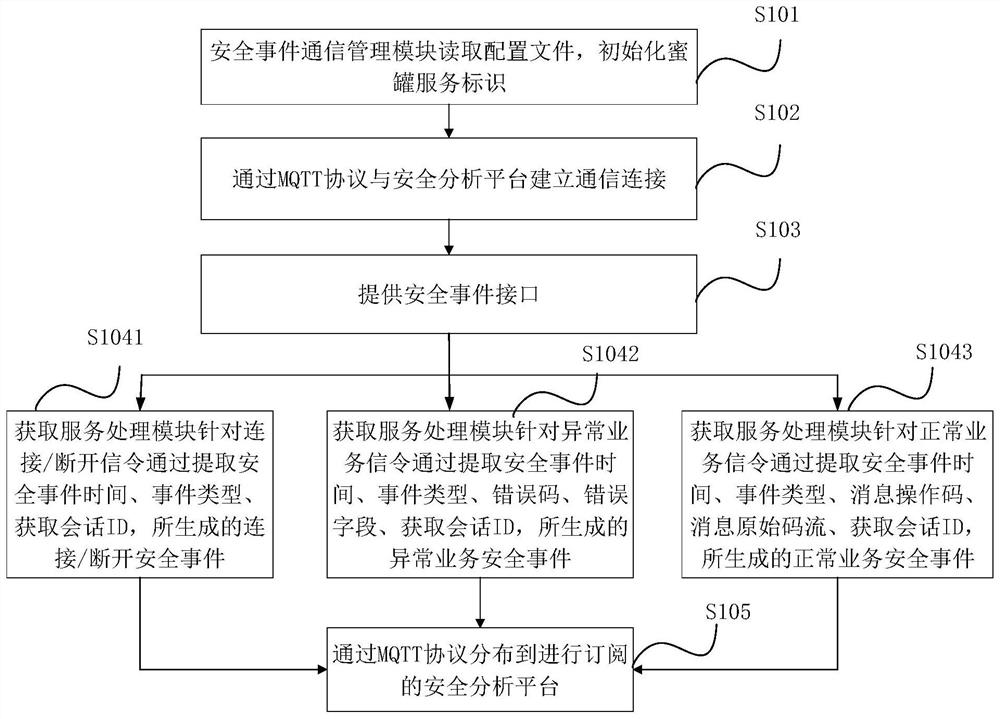
[0141] image 3 It is a sequence diagram of the response message corresponding to the signaling message generated by the simulation network element based on the simulation network element in the 5G independent networking simulation module provided by the second embodiment of the present invention. This embodiment specifically describes the working principle of the 5G independent networking simulation module illustrate.
[0142] Optionally, the service processing module is also used to transmit the signaling message to the 5G independent networking simulation module; the 5G independent networking simulation module is used to generate a response message corresponding to the signaling message based on the simulation network element, and send The response message is fed back to the attacking client.
[0143] Optionally, the response message includes a registration response message, an authentication authentication response message, an encrypted secure channel establishment respon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com