Learning data authentication method based on block chain
A data authentication and blockchain technology, applied in the blockchain field, can solve the problems of low fairness and credibility of authentication results, poor system flexibility, and large amount of block information redundancy, so as to reduce redundancy. The effect of margin, reduction of calculation amount, and improvement of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
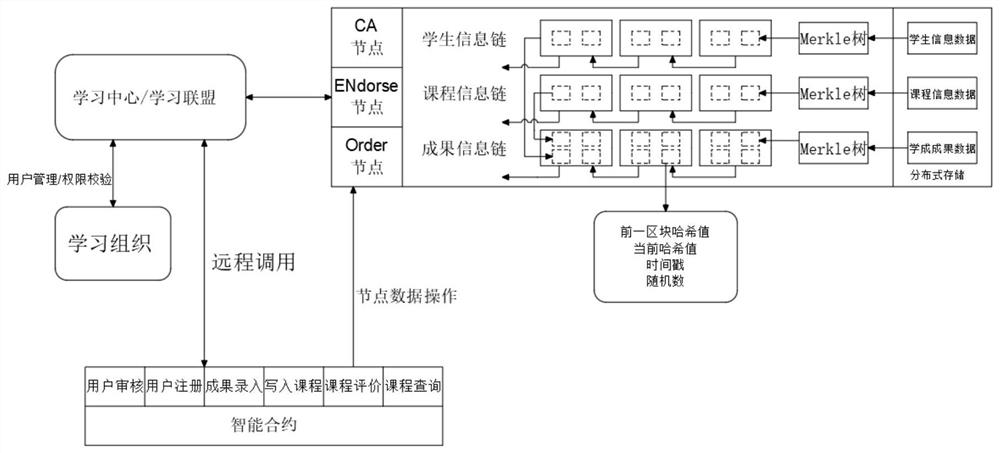
[0036] Example 1 A learning data authentication method based on a block chain, including:
[0037] First, intelligent contract
[0038] Enter personal information in the system.
[0039] (1) User audit, review the user's identity information;
[0040] (2) User registration, open account according to user information;
[0041] (3) The results are entered, and the learning data of the account is entered;
[0042] (4) Write the course and write the online learning course type and name of the account;
[0043] (5) Curriculum evaluation, entry into the relevant courses to complete quality and evaluation;
[0044] (6) Curriculum query, query the relevant course data of the account.
[0045] Second, remote call
[0046] Transfer personnel related information to the learning center for administrative classification.
[0047] Third, user management
[0048] Import the relevant personnel information into a corresponding learning organization.
[0049] Fourth, node management
[0050] The pe...
experiment example 1
[0087] In the learning data authentication method of the block chain, the present invention has high system operation flexibility, the learning data authentication time is short, and the two-way evaluation of online learning results and the quality of the course can be promoted. In order to verify the relevant technical solution, the inventors The following trial:
[0088] The actual operation time comparison of the first embodiment and the block-based learning data authentication method of the block chain in ratios 1, and the Group A uses the learning data authentication method in Example 1, and the B group uses the learning data authentication in ratio 1. Method, simultaneous input operation, compare the time required to consume, the structure is as follows:
[0089] Time / s required to consume Example 1 86 Contrast 1 350
[0090] As can be seen from Table 1, the learning data authentication method based on the block chain provided in the first embodime...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com