Secure cloud computing
A technology for identifying information and applications, which is applied in the field of secure cloud computing and can solve problems such as native applications connecting to malicious servers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
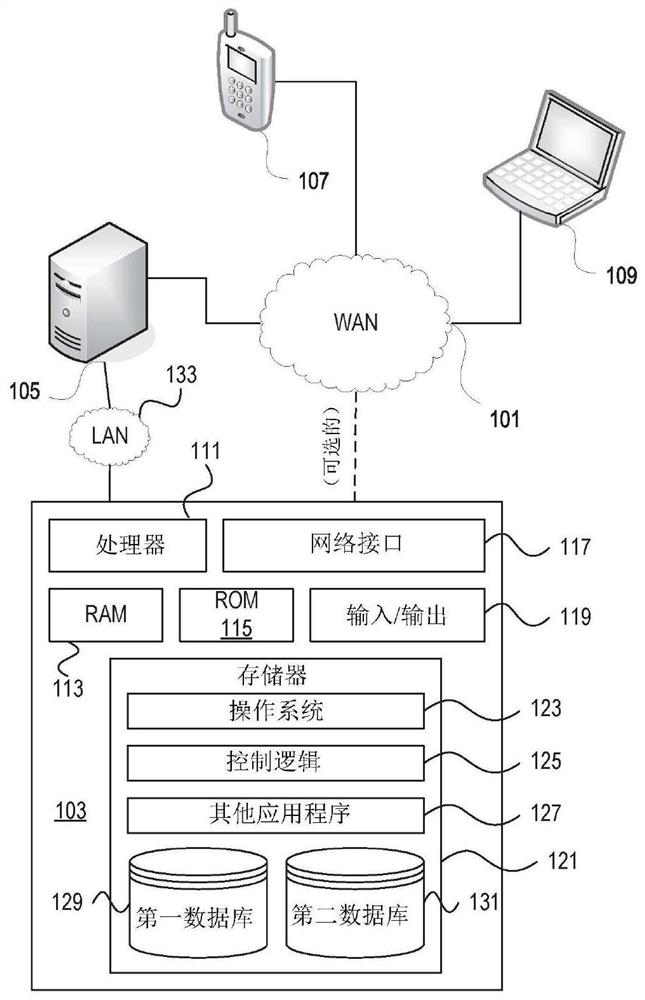
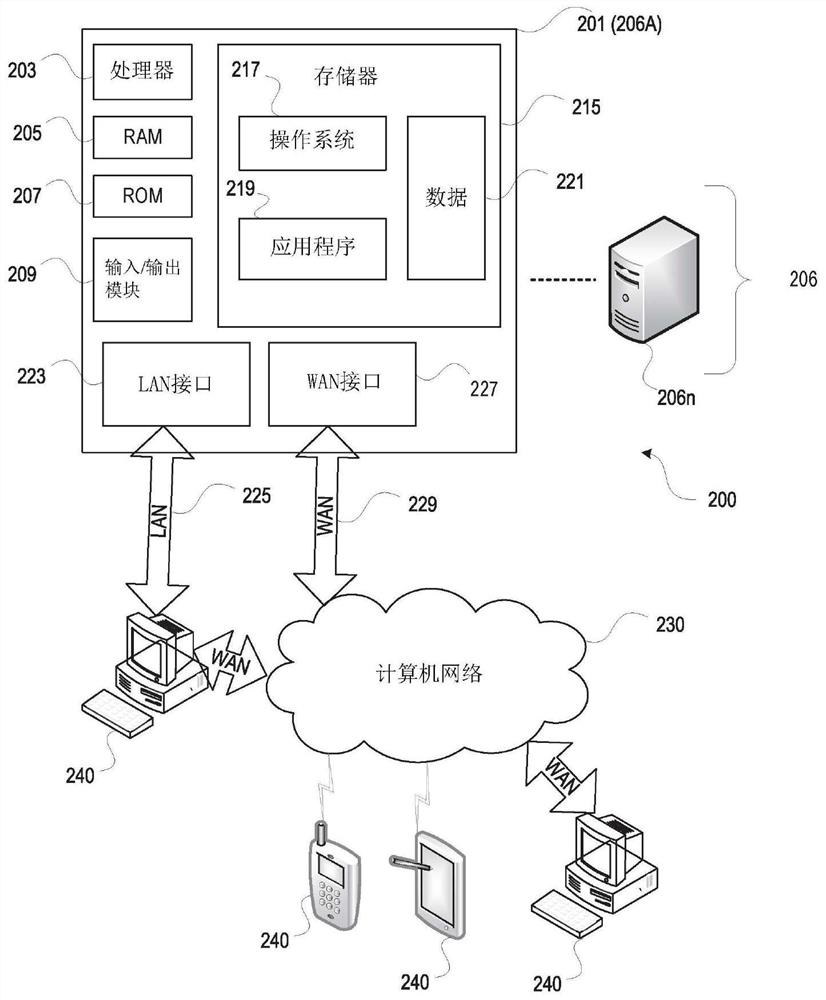
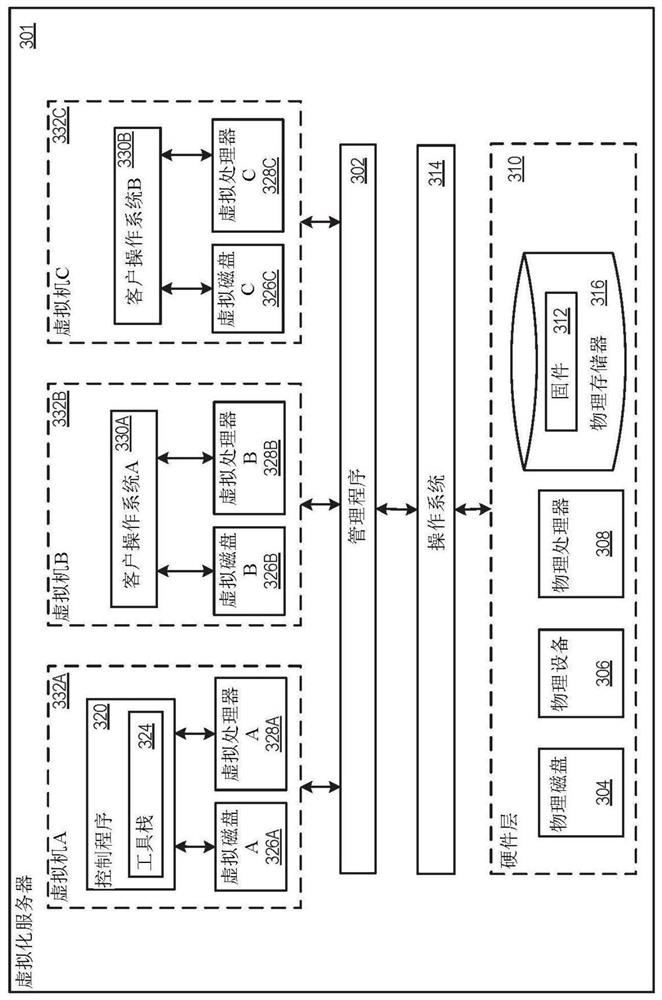
[0023] In the following description of various embodiments, reference is made to the accompanying drawings identified above and forming a part hereof, and in which is shown by way of illustration various embodiments in which aspects described herein may be practiced . It is to be understood that other embodiments may be utilized and structural and functional modifications may be made without departing from the scope described herein. The various aspects are capable of other embodiments and of being practiced or carried out in various different ways.
[0024] As an overview of the subject matter described in more detail below, aspects described herein aim to safely use web applications to invoke applications to accomplish tasks. An application can use the identity information provided by the web application to determine whether to honor a request from the web application. Web applications can send requests to applications via a browser. The request may include the origin of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com