Method and device for improving bytecode reverse engineering effect of smart contract
A reverse engineering, smart contract technology, applied in reverse engineering, software maintenance/management, etc., can solve problems such as difficulty in understanding programs, inability to recover function signatures, inability to recover variable types, etc., to achieve the effect of increasing transparency and improving effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
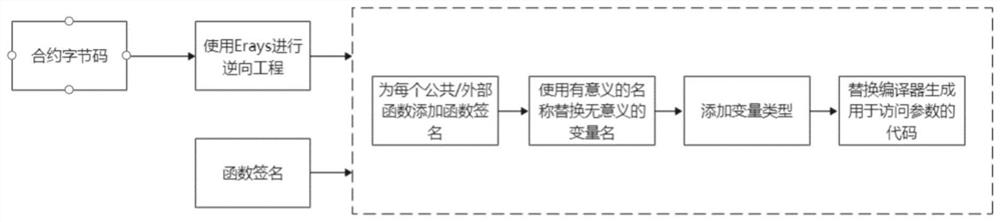
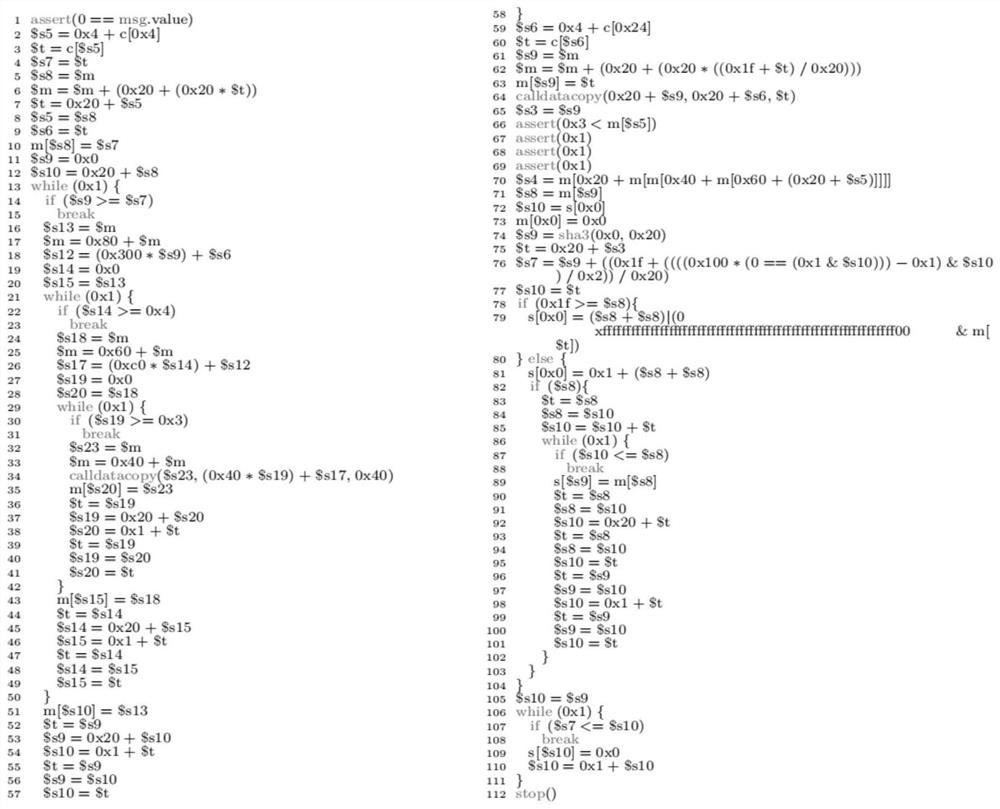
[0027] We use Erays + (the application method) and Erays (the prior art method) the result of reverse engineering the same bytecode. Erays+ adds the function signature (EarysABI) provided by SigRec (line 1). Since the restored function signature does not include the function name and parameter names, Erays + The function id is used, and argN is used for the Nth argument. Figure 4 Lines 7 and 8 in correspond to lines 4 and 5 in the source code. In addition, Erays + The code generated by the compiler to check ether transfers (line 2), array overflow (lines 3-6), and terminate program execution (line 10) is preserved. Note that Erays simplifies the lower dimension bounds checks to true (Lines 4-6), since the sizes of the lower dimensions are known, so the results of these bounds checks can be determined without being performed. Then we explain. Erays + How to simplify the result of Erays. First, Erays + Replace the meaningless variable name m[$s5] with num(arg1), indica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com