Information protection method and system based on user authority automatic check
A technology for automatic inspection and information protection, applied in digital data protection, instruments, electrical digital data processing, etc., can solve the problems of difficult adjustment of control methods, detection and control methods that depend on the response link of user requests, and easy misjudgment, etc. The effect of preventing leakage risk
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to understand the content of the present invention more clearly, it will be described in detail with reference to the drawings and embodiments.
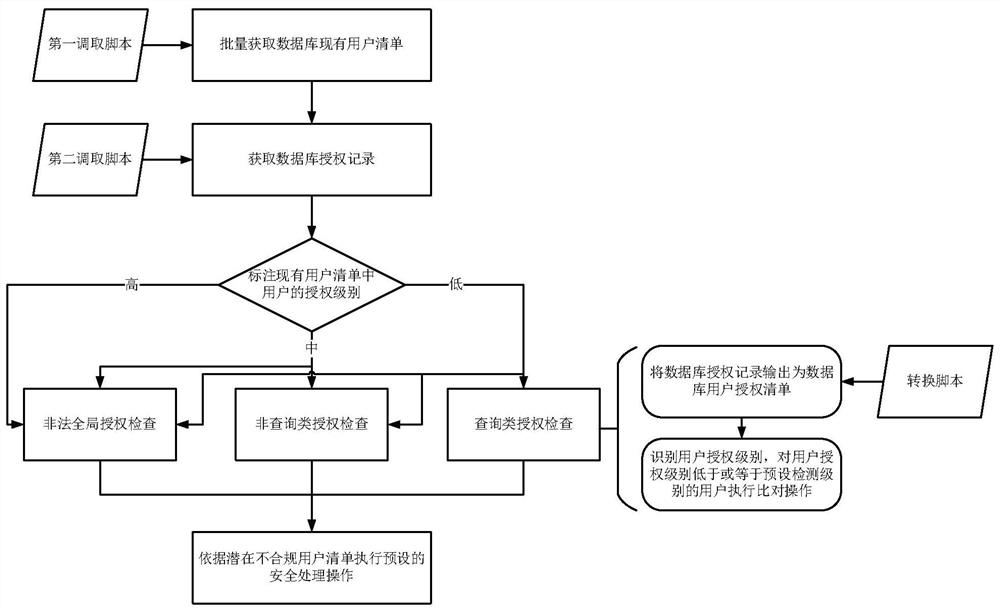
[0043] Such as figure 1 Shown is a schematic flow chart of the information protection method based on automatic inspection of user rights in the present invention, and the main steps include:
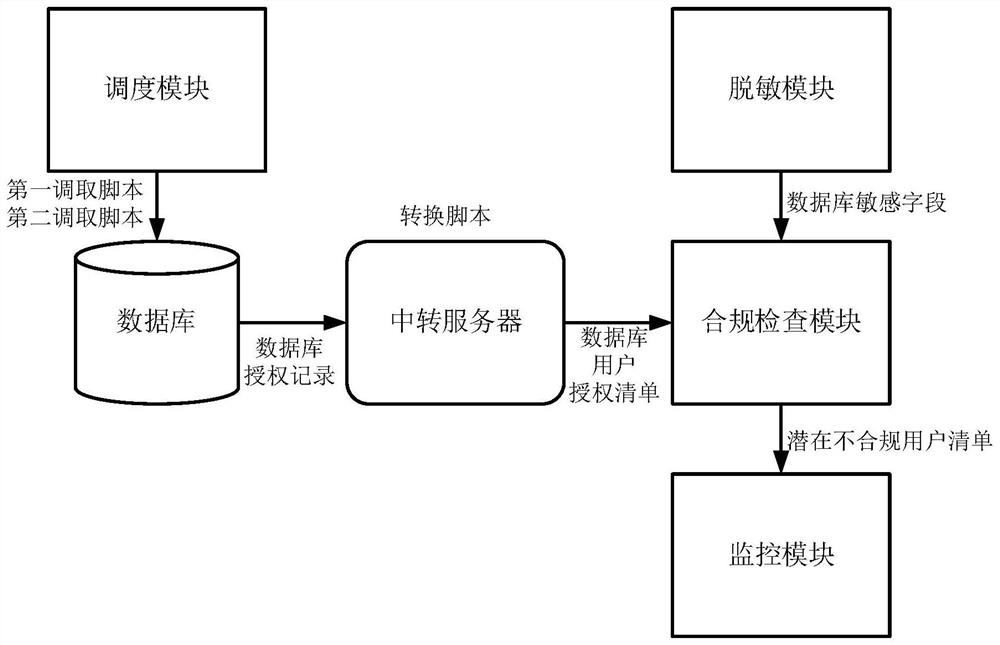
[0044] Use the first call script to automatically obtain the list of existing users in the database in batches;
[0045] Use the second call script to obtain the database authorization records of the users in the existing user list, especially including the use of the second call script to regularly and automatically query the database system table syscat.tabauth to obtain the historical user authorization records of the database. Call the script to read the configuration file to obtain the historical user database db authorization records, global global user authorization records, tables table user authorization records and c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com