A tamper-proof processing method and device
A processing method and anti-tampering technology, which is applied in the field of communication, can solve problems such as the inability to prevent malicious tampering of web pages, the inability to prevent tampering inspections, etc., and achieve the effect of preventing leakage and preventing spread
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
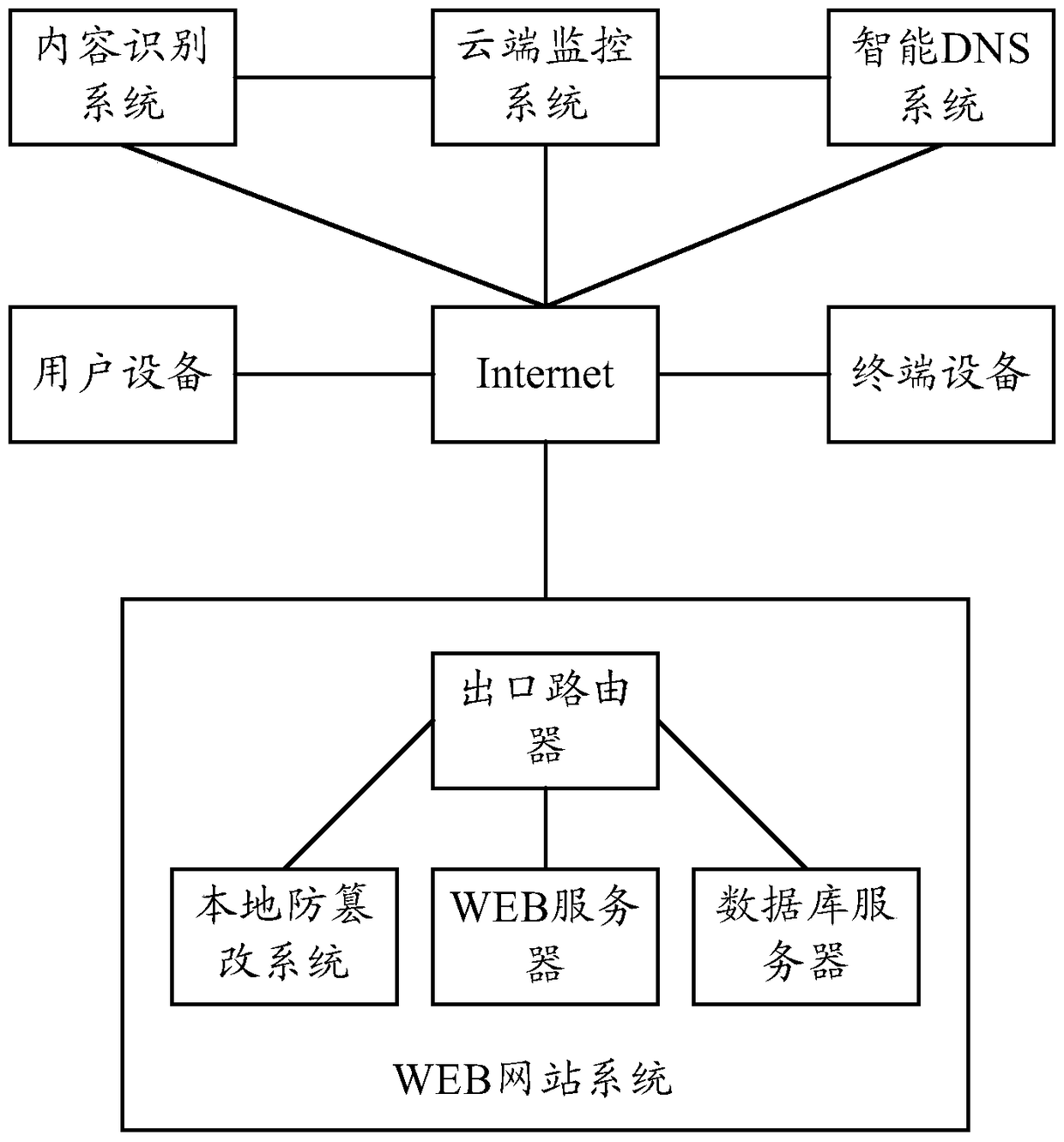
[0037] In view of the problems existing in the prior art, a tamper-proof processing method is proposed in the embodiment of the present invention, so as to figure 1 This is a schematic diagram of an application scenario of an embodiment of the present invention. The method can be applied to at least a cloud monitoring system deployed on a public network, an intelligent DNS (Domain Name System) system deployed on a public network, and a content identification system deployed on the public network. system, WEB website system, user equipment used by website administrators, and terminal equipment used by ordinary users.
[0038] The WEB website system may specifically include a local anti-tampering system, a WEB server, and a database server. The local tamper-proof system can be deployed on the WEB server or separately. The database server can be deployed on the WEB server, or it can be deployed separately.
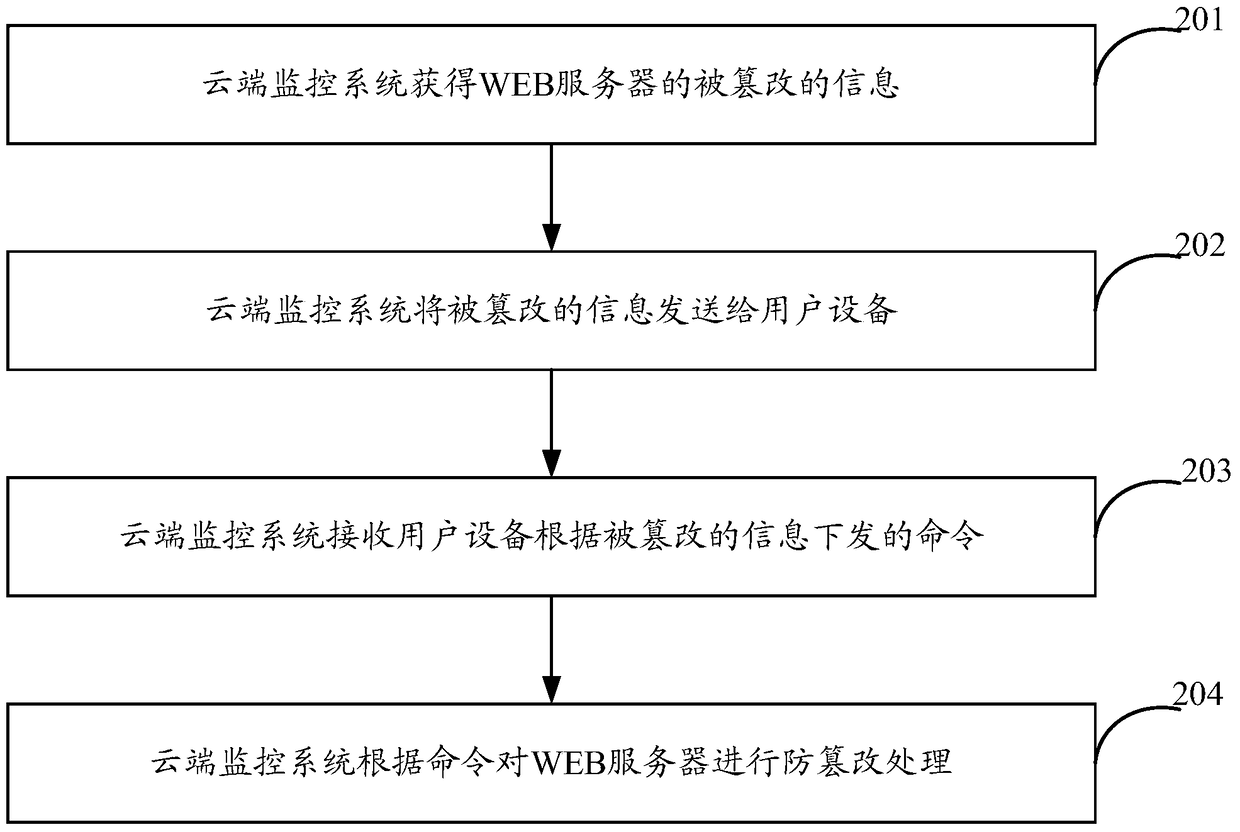
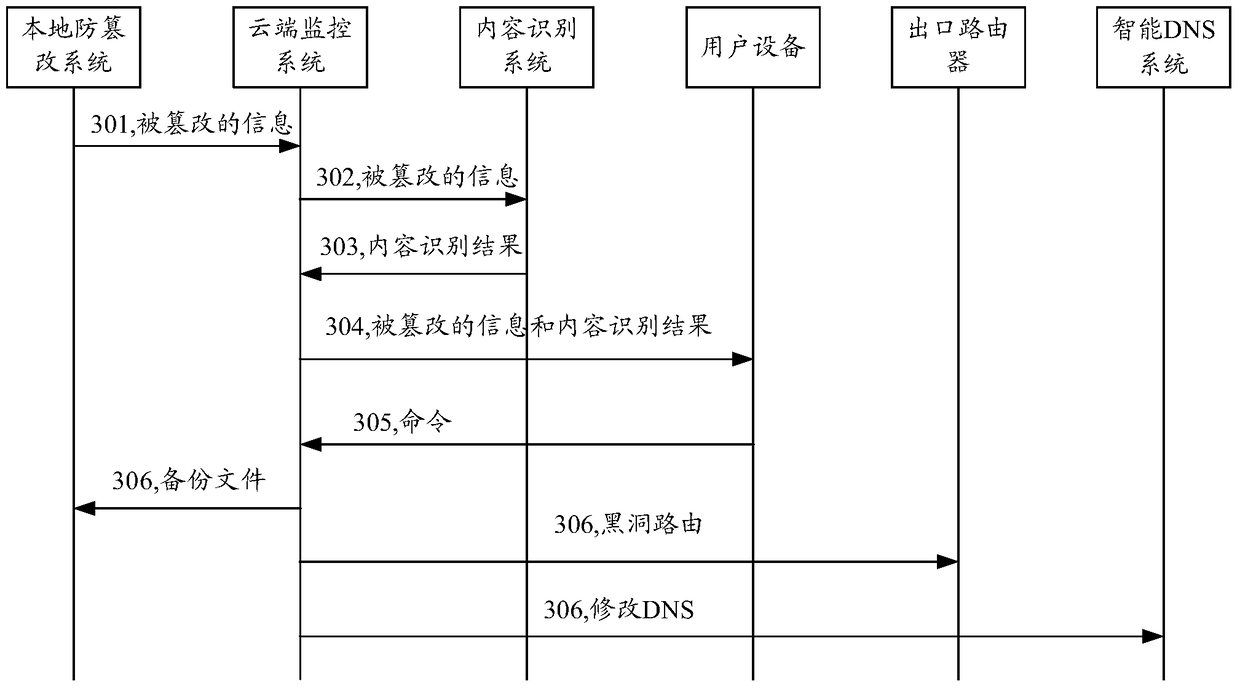
[0039] In the above application scenarios, such as figure 2 As shown...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com