Method and system for safely mounting storage device
A storage device and mounting technology, applied in the field of server security, can solve problems such as data security cannot be guaranteed, and achieve the effect of outstanding substantive features, simple structure, and wide application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
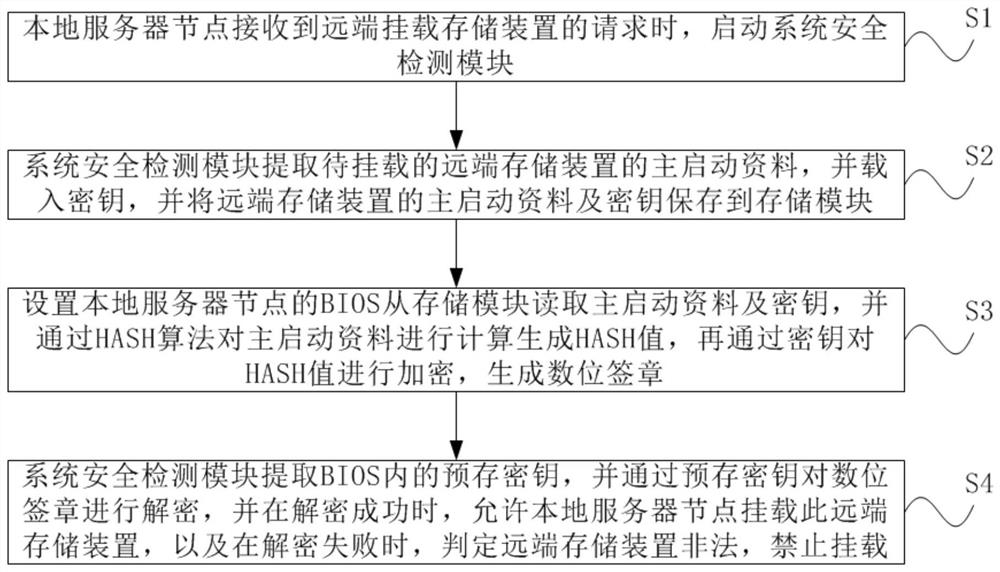
[0079] Such as figure 1 As shown, the present invention provides a method for securely mounting a storage device, comprising the following steps:
[0080] S1. When the local server node receives the request to mount the storage device from the remote end, it starts the system security detection module;
[0081] S2. The system safety detection module extracts the main startup data of the remote storage device to be mounted, and loads the key, and then saves the main startup data and the key of the remote storage device to the storage module;
[0082] S3. The BIOS of the local server node is set to read the main startup data and the key from the storage module, and calculate the main startup data through the HASH algorithm to generate a HASH value, and then encrypt the HASH value by the key to generate a digital signature;
[0083] S4. The system security detection module extracts the pre-stored key in the BIOS, and decrypts the digital signature through the pre-stored key, and...
Embodiment 2
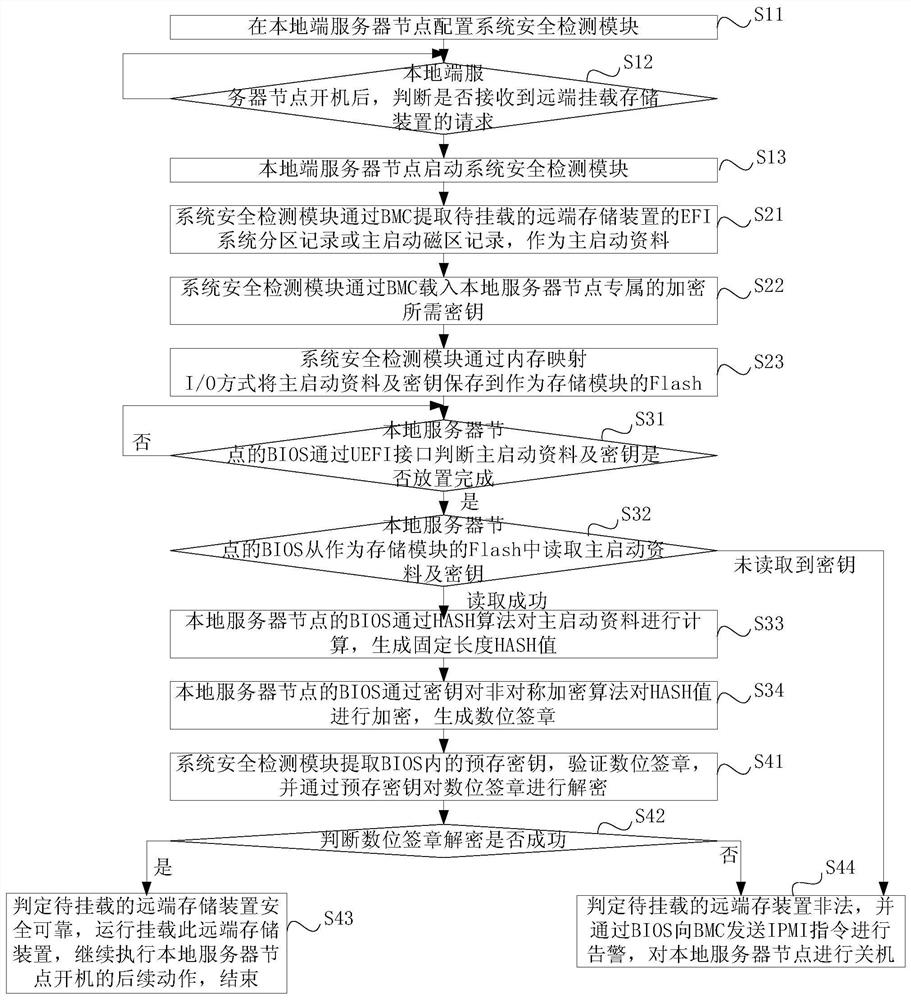
[0086] Such as figure 2 As shown, the present invention provides a method for securely mounting a storage device, comprising the following steps:
[0087] S1. When the local server node receives the request to mount the storage device at the remote end, it starts the system security detection module; the specific steps are as follows:
[0088] S11. Configure the system security detection module at the local server node; the system security detection module is implemented by a script program;
[0089] S12. After the local server node is turned on, it is judged whether a request for mounting the storage device at the remote end is received;
[0090] If yes, go to step S13;
[0091] If not, return to step S12;
[0092] S13. The local server node starts the system security detection module;
[0093] S2. The system safety detection module extracts the main boot data of the remote storage device to be mounted, and loads the key, and then saves the main boot data and the key of ...
Embodiment 3
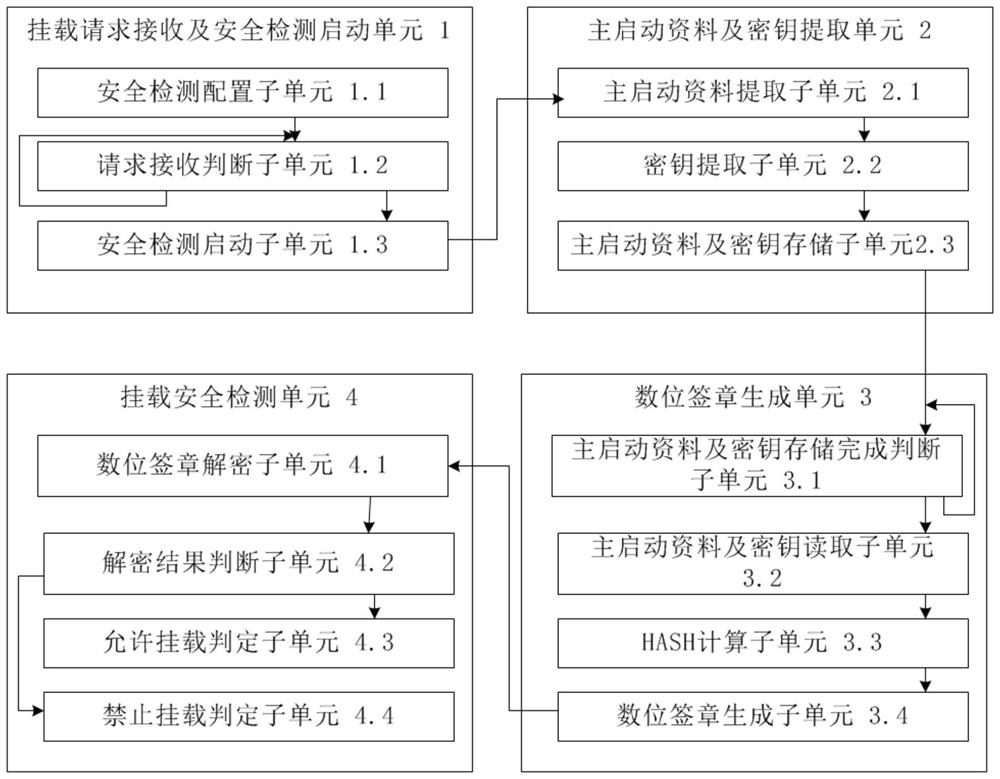
[0115] Such as image 3 As shown, the present invention provides a system for safely mounting storage devices, including:
[0116] Mounting request receiving and safety detection starting unit 1, used for starting the system safety detection module when the local server node receives a request to mount the storage device at the remote end;
[0117] The main boot data and key extraction unit 2 is used for the system security detection module to extract the main boot data of the remote storage device to be mounted, and load the key, and then save the main boot data and the key of the remote storage device to the storage module;
[0118] The digital signature generation unit 3 is used to set the BIOS of the local server node to read the main boot data and key from the storage module, and calculate the main boot data through the HASH algorithm to generate a HASH value, and then encrypt the HASH value through the key , to generate a digital signature;
[0119] Mounting security ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com