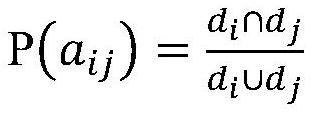Malicious user detection method based on feature learning and graph reasoning
A malicious user and feature learning technology, applied in the field of malicious user detection, can solve the problem that malicious user detection solutions are difficult to detect malicious user comments
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The present invention will be further described below in conjunction with the accompanying drawings.
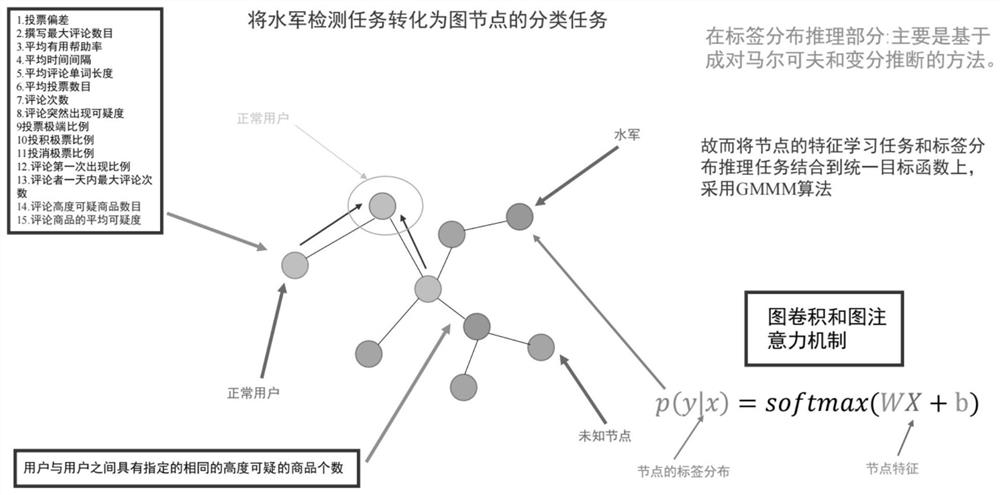
[0065] The invention provides a malicious user detection method based on feature learning and graph reasoning, comprising the following steps:
[0066] Step S1, building basic features;
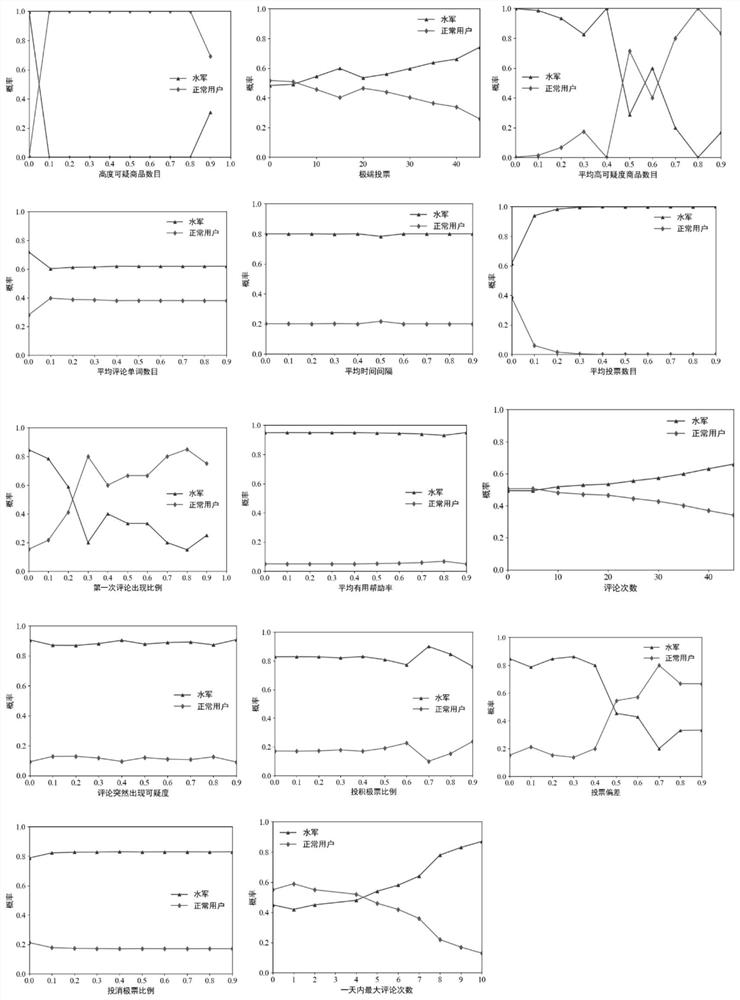
[0067] Based on the user's comment time, comment content, comment ID, commented product information and user's voting and scoring items, several features are screened out to distinguish malicious users from ordinary users. Specifically, the basic features constructed include: voting deviation, the maximum number of comments written, the average time interval, the average comment word length, the average number of votes, the number of comments, the sudden suspiciousness of comments, the extreme proportion of votes, the proportion of positive votes, and the negative votes Ratio of votes, ratio of comments appearing for the first time and the maximum number of comments a commenter makes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com